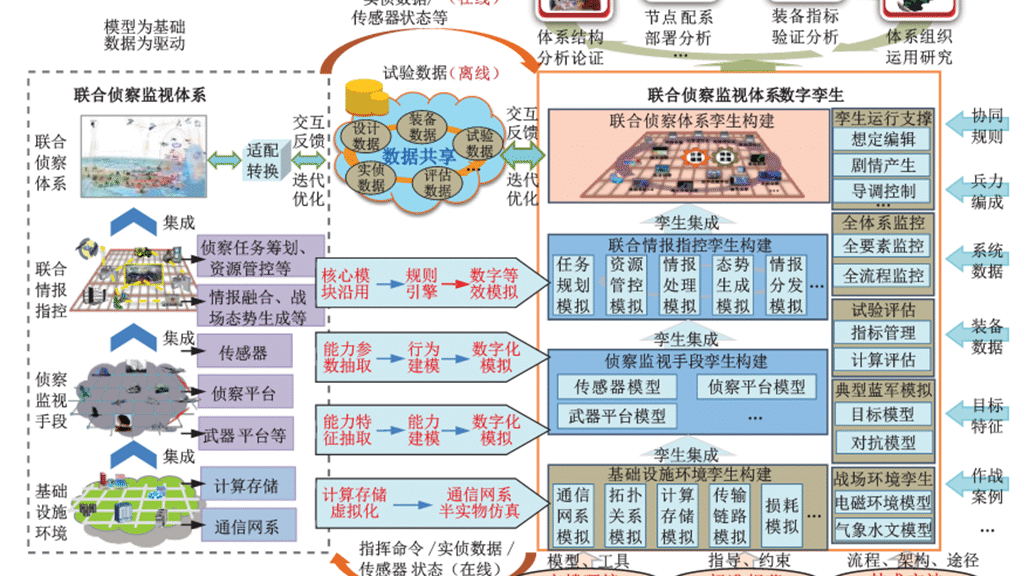
中國軍事體系優勢作戰概念研究-資訊化作戰體系如何作戰?九種典型作戰風格分析
現代英語:
System “Gathering Excellent War” It is “systematic warfare in information warfare. It does not necessarily refer to a certain combat style, but is composed of multiple combat styles and tactics” “combination boxing”, or combat style group . Emphasizes that, depending on the combat mission, combat opponent and the changing battlefield situation, any appropriate means and style of combat can be used flexibly to form combat advantages as long as it is conducive to forming comparative advantages and achieving system victory. In the specific implementation process of “system-based superior warfare”, these specific combat styles and operational tactics can not only be organized and implemented separately as part of joint all-domain operations, but also emphasize fighting “combination boxing”, using multiple strategies simultaneously, and winning as a whole.
In order to better understand its core connotation, this article lists Nine typical combat styles including overall deterrence warfare, electromagnetic disturbance warfare, network penetration warfare, and cognitive control disturbance warfare And analyze .
System “Juyouzhan” ――combination boxing that flexibly uses multiple combat styles“
1. Overall deterrence war: Emphasis on multi-domain joint deterrence; Three elements should be present in the implementation of an overall deterrent war ; Strong overall strength is central to achieving effective deterrence
2. Electromagnetic Disturbance Warfare : The key to competing for information advantage; On the combined means approach, information empowerment is achieved through “connection + sharing” ; Crack down on effective tactics for unmanned cluster operations
3. Cyber-sabotage: Soft “kill” is the main focus, combining soft and hard, focusing on breaking the net and reducing energy failure
4. Cognitive scrambling: Control the cognitive power of situational awareness and compete for information advantage; control the decision-making power of command and compete for decision-making advantage; control “brain” power and seize the advantage of brain control
5. Agile mobile warfare: High-efficiency and rapid decision-making; high-efficiency formation of a favorable combat situation; high-efficiency and instant gathering of combat forces; agile mobile warfare is an innovative development of traditional mobile warfare
6. Swarm autonomous warfare: It is conducive to forming a system advantage to suppress the enemy; it is conducive to enhancing the combat effect; it is conducive to falling into the enemy’s combat dilemma
7. Point-and-kill War: Achieving an efficient cost ratio for operations; targeting key nodes is an important option; large-scale system support is a basic condition; it is inseparable from precise intelligence support
8. Supply-breaking: The supply guarantee chain has a huge impact on the overall combat situation; the center of gravity of the attack is a key node in cutting off the enemy’s supply guarantee chain; the focus is on choosing the right time and making full use of tactics
9. System “paralysis battle:” The objectives of the operation are to make the enemy combat system run out of order; to strike the key nodes of the combat system with heavy blows; and to carry out soft strikes against the enemy combat system
For learning reference only, welcome to communicate and correct! Article views do not represent the position of this body
The concept of combat was first proposed as a new combat style. Innovative combat styles are a core element in the development of combat concepts. It can be said that system-gathering battle is a general term for a series of specific tactics. The following nine typical combat styles constitute the tactical system of system-gathering and superior warfare. They are: One is Overall deterrence warfare, actively organize static power display and deterrence actions in system excellence battles, and strive to defeat others without fighting or small battles; Two is Electromagnetic disturbance warfare uses various combat methods and action styles such as electronic detection, attack and defense to disrupt, prevent and destroy the enemy’s electromagnetic capabilities, actively compete for the advantages of the electromagnetic spectrum, seize the right to control information, and then win the initiative in combat; Three is In cyber attack warfare, various means such as soft strikes and hard destruction are used to defeat the enemy’s command network, intelligence network, communication network, logistics supply network, and disrupt the enemy’s command and support; Four is Cognitively Controlled Disturbance. Form a controlling advantage in the cognitive space through information attacks, public opinion attacks, and brain attacks; Five is Agile mobile warfare. Quickly adjust the deployment of troops and weapons, quickly gather capabilities on the battlefield, and seize combat opportunities; Six is Swarm autonomous warfare. Extensively use unmanned combat methods such as “bee swarms”, “wolf swarms”, and “fish swarms” to independently organize actions and distributed attacks to achieve joint human-machine victory; Seven is Pointkill. Accurately obtain intelligence, carry out multi-domain precision strikes, strive to shake the overall situation with one point, and maximize combat benefits; Eight is Supply-breaking. Organize an elite force to attack enemy logistics supplies and equipment supply supply chains, supply lines and supply bases, defeat the enemy and lose supplies and withdraw from the battle; Nine is System “paralysis battle”. A variety of means, such as breaking the net, exercising, and hitting nodes, are used to interfere with, delay, destroy, or even paralyze the effective operation of the enemy’s combat system and weaken its functions.
1. Overall deterrence
Overall deterrence warfare refers to actively organizing static power display and deterrence actions in the system’s battle for excellence, and striving to defeat others without fighting or small battles. Sun Tzu said: “Subduing one’s troops without fighting is a good thing.” Deterrence and war are the two main forms of military activity. And “deterrence” is mainly the act of showing determination and will to potential opponents by showing strength or threatening to use strong strength to deter opponents from action. It can be said that the overall deterrence war in the system-based battle of excellence is an important means or tactic to achieve the goal of “stopping” human troops without fighting. Clausewitz emphasized that the first rule of strategy is to be as strong as possible, first in general, and then in key locations. Modern warfare is system-to-system confrontation. The overall deterrence war under informationized local warfare requires not only traditional deterrence methods and capabilities on land, sea, air and space, but also new deterrence methods and capabilities such as space deterrence, electromagnetic deterrence, and network deterrence. It also requires an overall deterrence that shows the overall strength of the country. Especially with the rapid development of advanced technologies such as information technology, the technological revolution, industrial revolution, and military revolution have accelerated their integration, and strategic competitiveness, social productivity, and military combat effectiveness have become more closely coupled. Winning the information war is to a greater extent a contest between the will of the country and the overall strength of the country. To contain the war, we must first act as a deterrent to our opponents in terms of overall strength.
1.1 Emphasis on multi-domain joint deterrence
Means of deterrence typically include both nuclear and conventional deterrence. In the “system-based battle for excellence”, the overall deterrence war is implemented, aiming to comprehensively use conventional deterrence methods across the land, sea, air and space power grids to achieve the purpose of deterrence. Especially with the application of information network technology and space and directed energy technology in the military, space, networks, electromagnetic weapons, etc. have become new means of deterrence. Space deterrence, It mainly uses equipment such as rapid response electromagnetic orbit weapons, space-to-ground networked anti-navigation and positioning service systems, large elliptical orbit laser weapons, and high-power microwave weapons to threaten and attack the opponent’s space targets and form a deterrent against enemy space information “interference blocking”. Cyber deterrence mainly uses cyberspace situational awareness and attack equipment to threaten and attack the opponent’s military network and other critical information infrastructure to achieve deterrence against the enemy. Electromagnetic deterrence mainly uses electromagnetic spectrum combat systems to threaten and attack enemy detection, navigation, communications and other information weapons and equipment systems to achieve deafening and blinding deterrence against the enemy.
1.2 The implementation of overall deterrence should have three major elements
Implementing an overall deterrent war and achieving the desired effect of deterrence usually requires three main elements: One is strength. The deterrent must have the reliable ability or strength to frighten and fear the opponent; the second is determination and will. The deterrent party must dare to use this capability when necessary; third, to transmit information clearly. The deterring party must make the ability to act and the determination clearly known to the other party accurately and effectively.
Historically, the criteria for judging deterrent strength have varied in three main ways: First, the active military force; second, the combined national strength or war potential; and third, the total number of main battle weapons and equipment. For quite a long period of history, the number of troops was deterrence, and the strength of military strength depended directly on the size of the active military, the amount of vital weapons and equipment, and non-material factors such as the morale of the army’s training organization. After the twentieth century, with the expansion of the scale of warfare, deterrence power has become less limited to the strength of the military and the quantity of vital weapons and equipment, but is determined by the nation’s war potential, which includes economic power, scientific and technological power, energy resources, and even population size, among others. The overall deterrence war in the system’s “gathering and excellence war”, the formation of its deterrence strength is mainly based on the network information system, as well as the joint global deterrence capability formed under the integration of the system.
1.3 Strong overall strength is the core of achieving effective deterrence
The development of information technology and its widespread penetration and application in the military sector provide favourable conditions for building overall strength and achieving overall deterrence. System “Juyouzhan” is supported by the network information system, making full use of the permeability and connectivity of information technology, not only integrating various combat forces, combat elements, and combat units into an organic whole, realizing the military system combat advantages, but also integrating Various fields related to war and national mobilization, such as national politics, economy, diplomacy, finance, transportation, and energy, are connected and integrated into the national war mobilization system Gather all forces and resources to form an overall synergy, realize the emergence effect of system capabilities, show the overall strength advantage, and form a powerful invisible deterrent of united efforts and sharing the same hatred Create a situation that makes the enemy “powerful but unable to act ”“able to act but ineffective”, and play a role in containing and winning the war.
In the “overall deterrence war”, the scope of national war mobilization will be wider, not limited to a certain direction or region, but throughout the country and even the relevant regions of the world; mobilization time will be faster, and using networks and information systems, mobilization and action information can be quickly transmitted to everyone and every node at the first time; action coordination and synergy will be more consistent, and all forces distributed in various regions can be based on the same situation Under the same order, the operation is unified at almost the same time, which greatly improves the efficiency of operational synergy; resources are more fully utilized, and various war resources based on the Internet can quickly realize the conversion between peacetime and wartime, military-civilian conversion, and achieve integrated front and rear guarantees and precise guarantees.
2. Electromagnetic Disturbance Warfare
Electromagnetic disturbance warfare refers to the flexible use of electronic detection, attack and defense and other combat methods and action styles to disrupt, prevent and destroy the enemy’s electromagnetic capabilities, actively compete for the advantages of the electromagnetic spectrum, seize information control rights, and then win operational initiative.
2.1 The key to competing for information advantage Informatization local warfare is highly dependent on the electromagnetic spectrum, the Control and counter-control of electromagnetic space have become the focus of competition for information rights. Organize and carry out electromagnetic obstruction warfare, mainly to destroy the enemy’s electromagnetic spectrum and protect one’s own side from destruction. The electromagnetic spectrum is the main carrier for transmitting information. The use of electromagnetic means to disrupt the enemy’s electromagnetic spectrum will effectively reduce the enemy’s information combat capabilities and enable our own side to ensure the rapid and effective flow of information in the scenario of ownership of information rights, driving command flow, action flow, and material flow through information flow, energy flow, and then have the dominance and initiative in combat.
2.2 The basic focus is to implement electromagnetic disturbance warfare in the battle to deactivate the enemy’s combat system. It is mainly aimed at the enemy’s dependence on electromagnetic space. At the same time, in order to ensure its own effective use of electromagnetic space, it organizes various electronic reconnaissance and interference, attack, defense and support forces to attack enemy communication networks, radar networks, computer networks and command centers, communication hubs, radar stations, etc Computer network nodes, global navigation and positioning systems, space link systems such as the “Heaven and Earth Integrated Internet”, and various other frequency-using weapons and equipment carry out interference and attacks, block and destroy their communication and data transmission, and destroy the enemy’s combat system. “Connection” and “sharing” structural center of gravity provide support for seizing information control and electromagnetic control from the root, thereby weakening the enemy’s command and control capabilities Deactivating and disabling the enemy’s entire combat system.
2.3 Crack effective tactics for unmanned cluster operations
“Unmanned autonomous group operations such as swarms ”“wolves ”“fishes” are important features of information-based local warfare with intelligent characteristics. The various unmanned autonomous clusters are large in number, diverse in type, and complex in characteristics, and each individual can complement each other and play a role in replacing each other. It will be very difficult to intercept and damage the entire unmanned cluster. However, from a technical point of view, for unmanned combat clusters to achieve effective synergy, each individual must share and interact with each other. Once the communication coordination between unmanned clusters is interfered with, it will be impossible to share battlefield posture and information, and will not be able to coordinate actions with each other, making it difficult to achieve the combat effectiveness it deserves. This gives the other party an opportunity to implement interception of communications and electromagnetic interference. Therefore, the implementation of electromagnetic spectrum warfare, interference and attacks on the information and communication networks of unmanned clusters, and the destruction of their information sharing and interaction will make it impossible for each individual in the unmanned cluster to achieve effective synergy and thus lose its operational capabilities.
3. Cyber-sabotage
Cyber-blowout, It refers to military confrontation operations that comprehensively use technologies such as networks and computers and other effective means to control information and information networks. It is a major combat style of cyberspace operations and competition for network control. Its main combat operations are both soft-kill and hard-destroy, focusing on soft and combining soft and hard. Among them, soft kill is mainly a cyber attack, that is, it comprehensively uses blocking attacks, virus attacks and other means to block and attack enemy information networks, command systems, weapon platforms, etc., making it difficult for enemy networks, command information systems, etc. to operate effectively or even paralyze; hard destruction mainly uses precision fire strikes, high-energy microwaves, electromagnetic pulses, and anti-radiation attacks to paralyze and destroy enemy information network physical facilities Destroy enemy combat and weapons and equipment entities.
The important thing is to “break the net and reduce energy failure”. Organizing a cyber attack in a “system-based battle of excellence” is to target the weaknesses of the combat opponent’s military information network, use the advantages of the system to organize various cyber attack forces, and conduct combat command networks, reconnaissance intelligence networks, communication networks and even logistics throughout the entire operation. Supply networks, etc., continue to carry out soft killing and hard destruction operations to destroy the enemy’s network system The overall function of the enemy’s combat system is reduced or even disabled. It mainly targets core targets such as the enemy’s basic information network, intelligence network, command network, and support network, and implements a series of combat operations such as network-to-electronics coordinated attacks, deception and confusion, link blocking, and takeover control, so that the enemy’s intelligent combat network system becomes incapacitated and ineffective, achieving a critical victory that paralyzes the enemy system.
4. Cognitively Controlled Disturbance Warfare
Cognitive interference control war refers to interfering with, destroying or controlling the enemy’s thinking and cognition through information attacks, public opinion attacks, and brain attacks in the system optimization war, so that the enemy cannot make correct judgments and decisions, thereby controlling the enemy in cognitive space. form a controlling advantage.
Cognitive domains, That is, “human thinking space and consciousness space are areas that have a critical impact on combat decision-making and judgment”. The development of information technology, especially artificial intelligence technology, and its widespread application in the military field have expanded the battle of war from physical space and information space to cognitive space, making cognitive space a completely new combat domain. With the development of information and intelligent technology and its widespread and in-depth application in the military field, the Human-machine intelligence tends to converge This has made the status of cognition in intelligent warfare more prominent, and the cognitive field has gradually become an important battlefield. The right to control cognition has become a key element of future battlefield control. Fighting for cognitive control has become an important combat style for winning information-based local warfare operations with intelligent characteristics.
4.1 Control the cognitive rights of situational awareness and compete for information advantages
In the system’s “excellence battle”, information flow drives the flow of matter and energy, and information advantage determines decision-making advantage. Rapid and accurate knowledge of intelligence information and battlefield situations has an important impact on seizing command and decision-making advantages. Therefore, when organizing and implementing system-based battle gathering, we must make full use of intelligent technology and big data technology to conduct comprehensive analysis and judgment on massive intelligence information data, mine and extract the required intelligence information, and achieve more accurate and faster understanding of battlefield situations and combat environments. Cognition ensures that the enemy is discovered first and the enemy is recognized first from the source. While removing one’s own side “the fog of war”, create “the fog” for the opponent. Therefore, in order to compete for cognitive rights, we must not only control and process information before the enemy, but also take measures such as online public opinion attacks and high virtual reality chaos to actively create and spread false information, disrupt and disrupt the perception and cognition of hostile battlefield situations, maximize confusion and increase uncertainty, interfere with the opponent’s combat decisions, and delay its combat operations.
4.2 Control and command decision-making power and compete for decision-making advantages
Decision strengths determine action strengths. Quick decision-making by the commander is the key to shortening “the command cycle” and achieving quick wins. The organizational system focuses on excellent combat, and the success or failure of combat operations depends largely on the speed of the commander’s decision-making. It is necessary to “use intelligent auxiliary decision-making systems, select the best combat plans, scientifically and rationally allocate combat resources, and maximize combat effectiveness; use ubiquitous intelligent networks to access required combat nodes and combat platforms at any time to build and form an integrated combat system.” Achieve decentralized deployment of power, information, and capabilities, cross-domain linkage, form advantages at locations and times required for operations, gather energy to release energy, and gather advantages to win; Implementation “core attack”, Errors or deviations in the enemy’s command decisions are caused by hacking into the other party “chip”, tampering with its programs, and command and decision system algorithms.
4.3 Control “brain” power and seize the advantage of brain control
Cognitive interference control warfare in the system’s “gathering excellence war” emphasizes “attacking the heart and seizing the will”, that is, using network warfare, electromagnetic warfare and other methods to control the enemy’s human brain and consciousness cognition as well as the control system of the unmanned autonomous platform “attacking the heart Cognitive control warfare to control the brain and seize ambitions” Replace “destroy” with “control”, To achieve the goal of stopping and winning the war at the minimum cost. Attacking the heart and controlling the brain is different from traditional strategic deterrence. It places more emphasis on active attack. It is an active attack operation that mainly uses advanced information combat technology, brain control technology, etc. to attack the enemy’s decision-making leader, as well as intelligent unmanned autonomous combat platforms, auxiliary decision-making systems, etc., carry out controlled “brain” attacks, directly control and disrupt the opponent “brain”, influence and control the enemy’s decision-making, or disable it Enable stealth control of enemy combat operations. For example, “Targeting human cognitive thinking, using brain reading and brain control technology, and using mental guidance and control methods to directly carry out “inject ”“invasive” attacks on the brains of enemy personnel, interfering with, controlling or destroying the cognitive system of enemy commanders.”, deeply control it from the perspective of consciousness, thinking and psychology, seize “control intellectual power”, disrupt the enemy’s decision-making, destroy the enemy’s morale, and force the enemy to disarm.
5. Agile Mobile Warfare
Agile mobile warfare refers to the efficient decision-making, efficient adjustment of troop deployment and high-efficiency real-time gathering of combat forces in systematic battle, efficient gathering of capabilities on the existing battlefield, and seizing combat opportunities. Agility is the ability to respond quickly and timely to changes in the battlefield environment. It has the characteristics of responsiveness, robustness, flexibility, elasticity, innovation and adaptability.
Table 1 Connotation of the concept of agile warfare
5.1 Efficient and fast decision-making
To implement agile and mobile warfare, we must first make efficient and rapid decisions to win operational opportunities. Therefore, it is necessary to comprehensively use various means of reconnaissance, detection, perception and surveillance to obtain battlefield posture and target information in a timely manner, especially characteristic information, activity trajectories and real-time position information of time-sensitive targets, so as to ensure precise intelligence support for rapid decision-making. Efficient decision-making is also reflected in the speed of intelligence processing. It takes less time to screen effective intelligence information, formulate action plans at a faster speed according to changes in circumstances, and seize the initiative and seize the opportunity with one step ahead. High-efficiency decision-making focuses on shortening the decision-making cycle, taking the target time window as the central point, and integrating decision-making command with combat units and weapon platforms, rapid response, and overall linkage to improve combat efficiency.
5.2 High efficiency forms a favorable combat situation
It is necessary to “keep abreast of changes in the battlefield situation at any time, rely on the support of information networks, and achieve dynamic reorganization of combat forces and integration during movement through cross-domain, cross-dimensional, and diversified three-dimensional maneuvers. Combat resources flow efficiently throughout the region and gather during movement to achieve mobility and excellence.”, forming a favorable battlefield situation. Agile mobile warfare relies on data fusion processing, intelligent assisted decision-making and other means to quickly form combat plans, quickly project combat forces at a high frequency according to the case, organize troops to quickly form favorable combat deployments, and realize enemy discovery, enemy decision-making, and enemy fire, first enemy assessment, change the balance of power in the shortest time and fastest speed, form combat advantages, and improve the efficiency of combat operations.
5.3 Efficient and instant gathering of combat power
To organize agile mobile warfare, the key is to select the right combat force within a limited time, coordinate the entire battle situation, and form an overall synergy to ensure a fatal blow. Therefore, in response to changes in battlefield posture, especially target situations, it is necessary to draw up groups to form a joint mobile combat system formed by multi-domain combat forces, gather combat forces in real time, deploy quickly and mobilely to a favorable battlefield, and carry out real-time strikes against the enemy. For deep space, deep sea, etc. to become a new combat space, an intelligent unmanned autonomous combat platform can be organized Rapid mobility is deployed to lurk near key targets or important passages that are difficult for humans to reach due to physiological limitations, and ambush operations are carried out on standby, creating new cross-domain checks and balances.
5.4 Agile mobile warfare is an innovative development of traditional mobile warfare
In the history of both ancient and modern warfare at home and abroad, there have been numerous examples of successful battles that relied on rapid covert maneuvers to achieve combat objectives. However, the combat process of information-based local warfare has been greatly compressed, the combat rhythm has accelerated rapidly, and fighter aircraft are fleeting. It has put forward higher requirements for fast mobile capture fighters. It is difficult to meet the requirements of joint operations and all-area operations under information conditions alone “fast pace, high speed”. requirements, so agile mobility must be implemented.
6. Unmanned cluster autonomous warfare
Unmanned cluster autonomous warfare refers to the widespread use of unmanned combat methods such as “bees”“ wolves ”“fishes” in system optimization warfare to independently organize actions and distributed attacks to achieve joint human-machine victory. With unmanned autonomous equipment becoming the main combat force on the battlefield, defeating the enemy with unmanned autonomous equipment clusters and numerical superiority has become an important combat style in information warfare.
6.1 It is conducive to forming a system advantage to suppress the enemy
Unmanned cluster independent warfare gives full play to the special advantages of unmanned combat weapons such as all-weather, unlimited, difficult to defend, and low consumption, and builds and forms large-scale unmanned combat clusters or formations such as unmanned “bee swarms”“ wolves ”“fish swarms”, and organizes independently, mutual coordination, can implement close-range and full-coverage reconnaissance, or act as bait to interfere or deceive, or cooperate with main battle weapons to implement distributed coordinated attacks Enable overall mobility and joint control of the enemy.
6.2 Conducive to enhancing combat effectiveness
In “unmanned cluster autonomous operations”, different combat units within the unmanned cluster organization are responsible for different functions and different tasks, including those responsible for reconnaissance, those carrying out electromagnetic interference and fire strikes, and those playing “decoy” roles. Clusters transmit and share battlefield information through inter-group networks, perform their respective duties according to the division of labor, and collaborate in real-time, independently, and dynamically according to battlefield changes. They not only give full play to their advantages in quantity and scale, but also use information networks and intelligent integration technology to achieve integration effects, using cluster advantages to consume enemy defense detection, tracking and interception capabilities, rapidly saturating and paralyzing the enemy’s defense system.
6.3 Conducive to getting into enemy combat difficulties
Unmanned cluster autonomous warfare uses a large number of autonomous unmanned combat platforms with different functions to form an unmanned combat cluster integrating reconnaissance and detection, electronic interference, cyber attacks, and fire strikes. It can carry out multi-directional and multi-directional operations against the same target or target group. Multiple, continuous attacks will make it difficult for the enemy to make effective counterattacks.
7. Pointkill Battle
“Precise point-killing warfare” refers to accurately obtaining intelligence in system-based battles, implementing multi-domain precision strikes, striving to shake the overall situation with one point, and maximizing combat benefits. Informationized local warfare is an overall confrontation between systems. Implementing precise point-killing warfare and precise strikes on important nodes and key links of the enemy’s combat system will destroy the enemy’s combat system and reduce enemy combat capabilities, which will achieve twice the result with half the effort. Combat effect.
7.1 Achieve efficient combat cost ratio
Achieving maximum combat effectiveness at the minimum cost is a goal pursued by both sides of the war. With the widespread application of information technology in the military field and the advent of information warfare, precision-guided weapons, intelligent kinetic energy weapons, integrated surveillance and attack drones, and laser weapons are widely equipped with troops; through the use of big data, artificial intelligence and other technologies, it has become possible to accurately calculate the required troops and weapons. These all provide material and technical conditions for achieving precision point kill warfare, achieving operational objectives at a lesser cost, and achieving operationally efficient fee ratios.
7.2 Targeting key nodes is an important option
The key to precise point-killing battles is to hit the key points and nodes. If you don’t hit, it will be enough. If you hit, it will be painful. If you hit, you will win. If you hit a point, you will break the enemy’s system and shake the overall situation. The target of the strike is not limited to the enemy’s dispersed deployment of ships and aircraft, but should also be targeted at local, dynamic, time-sensitive targets or independent targets such as enemy command centers, important hubs, and even major generals and commanders, in pursuit of deterrence, shock and enemy-breaking system effects. It will also be an effective countermeasure to use precision strike fire to carry out “point-kill” strikes in response to the distributed tactic of decomposing expensive large-scale equipment functions into a large number of small platforms and implementing decentralized deployment of forces.
7.3 Large-scale system support is the basic condition
The implementation of precise point-kill warfare cannot be separated from the support of a large-scale system. Focusing on achieving combat goals, the required troops and weapons are transferred from each operational domain that is dispersed and deployed. With the support of the network information system, they are dynamically integrated to form a precision strike system to achieve overall linkage and system energy gathering. Through reasonable and sufficient firepower, the target is concentrated. Strike to achieve precise use of troops and precise release of energy. To implement precise point-and-kill operations to be precise, all links within the entire combat system need to be closely connected without any mistakes. The U.S. military’s killing of bin Laden in 2011 can be said to be a typical strategic precision killing operation supported by the strategic system.
7.4 It is inseparable from precise intelligence support
In precision point kill warfare, precise intelligence support is always the key to achieving operational goals. Therefore, before the war, various means should be used to collect various enemy intelligence information, especially accurate analysis and judgment of enemy targets. During combat operations, various sensors and intelligence reconnaissance methods should be used to accurately grasp enemy target changes and dynamic target situations in a timely manner, so as to provide powerful and effective intelligence support for the implementation of precise point-kill warfare. The U.S. military’s targeted killing operation against Soleimani was a typical precise point-killing battle supported by an efficient intelligence system.
8. Supply-breaking
Supply chain-breaking warfare refers to organizing elite forces in a system-gathering battle to attack the enemy’s logistics supplies and equipment supply supply chain, supply lines and supply bases, defeat the enemy and lose supplies and withdraw from the battle. In response to weaknesses such as the enemy’s long logistics supply line and large equipment support stalls, the organization of elite forces to build “chain-breaking warfare” combat systems, and to carry out sustained, precise and devastating strikes against enemy logistics supplies and equipment supply chains, supply lines and supply bases, will make it unsustainable due to the loss of supplies and will have to withdraw from the battle.
8.1 The supply guarantee chain has a huge impact on the overall combat situation
Logistics equipment support is an important basis for operations. The constant supply of logistical supplies and weapons and equipment ultimately determines the size of an army’s combat troops, whether they can fight, in what season, where they can fight, how far they can leave their rear bases, how long they can fight, how fast they can maneuver, and so on. In information warfare, the consumption of battlefield materials has increased exponentially. Not only has the dependence on logistics equipment support for operations not decreased, but it has become larger and larger. Moreover, the requirements for the specialization of support have also become higher and higher In particular, modern combat equipment is available in a wide variety of models and specifications, with huge volumes of mixed transport, more dispersed troop deployment and very high requirements for transport capacity, which makes bases, communication lines and transport more important than ever. The stable and efficient operation of the supply guarantee chain and continuous and uninterrupted supply guarantee are the key to operational victory and have a huge impact on the overall operational situation.
8.2 The center of gravity of the attack is a key node in cutting off the enemy’s supply guarantee chain
The operational center of gravity of supply chain-breaking warfare is a key link in attacking the enemy’s supply support chain, and its continuous support capability is lost through chain-breaking. Therefore, the organization of supply chain-breaking warfare should mainly target enemy ground railway and road transport lines, maritime supply convoys, military requisitioned merchant ships and combat support ships, large and medium-sized air transport aircraft, and rear supply bases. For example, striking the enemy’s maritime supply support chain and cutting off the enemy’s fuel, ammunition, fresh water, and food supplies will make the enemy aircraft carrier battle group lose its ability to continue fighting, which in turn will even affect the outcome of a battle.
8.3 The key is to choose the right time and make full use of tactics
It is crucial to organize the implementation of supply chain-breaking warfare and to choose a favorable time to strike. The timing of strikes in supply chain-breaking warfare should be organized and implemented when the enemy’s supply maneuvers are selected, so as to surprise and attack unprepared concealed tactics, carry out sudden strikes on enemy supply vehicles, ships and transport aircraft, and terminate their supply operations. Specific tactics usually include covert ambush warfare, organizing capable forces to ambush the routes and routes that enemy transportation must pass through, waiting for opportunities to carry out covert surprise attacks; stealth surprise warfare, using submarines, stealth fighters, etc. to covertly move forward to carry out attacks on enemy transportation targets, and win by surprise; long-range precision warfare, using long-range conventional surface-to-surface missile forces to attack enemy supply bases and airports Long-range precision strikes are carried out at the departure points of supplies such as docks.
9. System “paralysis battle”
System destruction and paralysis war refers to the comprehensive use of various means such as breaking the network, breaking the chain, and defeating nodes in the system optimization war to interfere with, delay, destroy, or even paralyze the effective operation of the enemy’s combat system and weaken the functions of the enemy’s combat system. The essence of system destruction and paralysis warfare is to weaken the correlation and structural power between the elements of the enemy’s combat system, degrade the functions of the system, and fail to play a role in doubling capabilities.
9.1 The combat goal is to disorderly operate the enemy’s combat system
In information warfare, the combat systems of both warring parties have their own internal order, and this order is the key to maintaining and supporting the operation of the combat system. The side that can maintain and navigate the internal order of the combat system will gain an advantage and, conversely, a disadvantage. Therefore, the goal of “disrupting the enemy’s winning mechanism and causing the enemy’s combat system to become disordered” should be established in system destruction and paralysis warfare. This requires that the system be fully utilized in the battle of paralysis Information technology in particular intelligent algorithms The “powerful enabling effect” can quickly adjust and reconstruct one’s own combat system, quickly generate and release powerful combat power, and implement agile and precise strikes on the enemy’s combat system, causing the enemy’s combat system to lose normal operating order and become disordered. The system functions are destroyed and the overall combat capabilities are significantly reduced.
9.2 A key node in the heavy strike combat system
Systematic confrontation is a major feature of information warfare. System is an important foundation and support for system confrontation, and is also the key to effectively exerting combat effectiveness by integrating various combat forces, weapon platforms and weapon systems on the battlefield. Whether the system can be kept robust and run smoothly has a decisive influence on the achievement of war and campaign victories. In the battle to destroy and paralyze the system, the key is to focus on the enemy’s integrated combat system of land, sea, air and space power grids, breaking the network, breaking the chain, and attacking nodes. By attacking key node targets, the operating mechanism of the enemy’s combat system will be out of order, and it may even be severely damaged or destroyed. Paralysis. Therefore, the basic direction of system destruction and paralysis warfare is to select key units, key nodes, and key elements of the enemy’s combat system to carry out strikes, attack one point, destroy one part, and paralyze the whole, so as to achieve the goal of defeating the enemy.
9.3 Implement soft strikes against the enemy’s combat system
When organizing and implementing system breaking and hard destruction, it simultaneously organizes soft-kill combat operations such as electronic warfare, cyber warfare, psychological warfare, and public opinion warfare, and carries out soft strikes on the information domain and cognitive domain of the enemy’s combat system. Electronic warfare uses the power of electronic warfare to carry out strong electromagnetic interference against the enemy, causing its information to malfunction and fall into the fog of war; cyber warfare uses the power of cyber attack to attack the enemy’s network information system, causing the enemy’s command and communication system and computer network to be severely damaged, causing its command to malfunction and fall into information islands or even war islands; psychological warfare and public opinion warfare, using psychological warfare and public opinion warfare methods It carries out psychological strikes and public opinion guidance against the enemy, severely damaging his will to fight and inducing his cognitive disorientation. Organizing “people’s livelihood wars” to attack the opponent’s major national economy and people’s livelihood facilities can also play a role in the enemy’s combat system “drawing fuel from the bottom of the cauldron”. In the 1999 Kosovo War, the US military did not attack the Yugoslav army, but attacked its war potential target system, causing the Yugoslav soldiers and civilians to lose their will to fight and lead to defeat.
現代國語:
體系聚優戰是資訊化戰爭中的體係作戰,其不限定特指某一種作戰樣式,而是由多種作戰樣式和戰法組成的“組合拳”,或作戰樣式群。強調根據作戰任務、作戰對手和戰場情勢變化,只要有利於形成相對優勢、達成體系製勝,可以靈活運用任何適宜的作戰手段和样式,形成作戰優勢。在體系聚優戰具體實施過程中,這些具體作戰樣式和行動戰法既可以作為聯合全局作戰的一部分單獨組織實施,更強調打“組合拳”,多策並舉,整體制勝。
為更能理解其核心內涵,本文列舉了整體威懾戰、電磁擾阻戰、網路破擊戰、認知控擾戰等九大典型作戰樣式,並進行分析。
體系聚優戰――靈活運用多種作戰樣式的「組合拳」作者:學術plus高級觀察員 東週
本文主要內容及關鍵字
1.整體威懾戰:強調多域聯合威懾;實施整體威懾戰應具備三大要素;強大整體實力是實現有效威懾的核心
2.電磁擾阻戰:爭奪資訊優勢的關鍵;在組合手段方法上,透過「連結+共享」實現資訊賦能;破解無人集群作戰的有效戰法
3.網路破擊戰:軟殺傷為主,軟硬結合,重在破網降能失效
4.認知控擾:控制態勢感知認知權,爭奪資訊優勢;控制指揮決策權,爭奪決策優勢;控制「腦」權,奪取腦控優勢
5.敏捷機動戰:高效率快速決策;高效率形成有利作戰態勢;高效率即時聚合作戰力量;敏捷機動戰是對傳統機動作戰的創新發展
6.蜂群自主戰:有利於形成體系優勢壓制敵方;有利於增強作戰效果;有利於陷敵於作戰困境
7.精確點殺戰:實現作戰的高效費比;打關鍵節點目標是重要選項;大範圍體系支撐是基本條件;離不開精確情報保障
8.補給斷鍊戰:供應保障鏈對作戰全局影響巨大;打擊重心是斷敵供應保障鏈的關鍵節點;重在選準時機活用戰法
9.體系毀癱戰:作戰目標是使敵作戰體系運作失序;重拳打擊作戰體系的關鍵節點;對敵作戰體系實施軟打擊
僅供學習參考,歡迎交流指正!文章觀點不代表本機構立場
作戰概念首先是作為一種新的作戰樣式提出。創新作戰樣式是作戰概念開發的核心內容。可以說,體系聚優戰是一系列具體戰法的總稱。以下九大典型作戰樣式構成了體系聚優戰的戰法體系。分別為:一是整體威懾戰,在體系聚優戰中積極組織靜態威力展示和威懾行動,力爭不戰或小戰而屈人之兵;二是電磁擾阻戰,運用電子偵攻防等多種作戰手段和行動樣式,擾亂、阻止、破壞敵電磁能力的發揮,積極爭奪電磁頻譜優勢,奪取制資訊權,進而贏得作戰主動;三是網路破擊戰,運用軟打擊和硬摧毀等多種手段,破敵指揮網、情報網、通信網、後勤補給網,亂敵指揮保障;四是認知控擾。透過資訊攻擊、輿論攻擊、腦攻擊,在認知空間形成控制優勢;五是敏捷機動戰。快速調整兵力兵器部署,在即設戰場快速聚集能力,搶奪作戰先機;六是蜂群自主戰。廣泛運用「蜂群」、「狼群」、「魚群」等無人作戰手段,自主組織行動、分散式攻擊,實現人機聯合製勝;七是精確點殺戰。精準獲取情報,實施多域精確打擊,力爭打一點撼全局,實現作戰效益最大化;八是補給斷鏈戰。組織精銳力量,打敵後勤物資裝備供應補給鏈、補給線和補給基地,破敵失去補給而退出戰鬥;九是體系毀癱戰。綜合採取破網、鍛鍊、打節點等多種手段,幹擾、遲滯、破壞甚至癱瘓敵作戰體係有效運轉,削弱敵作戰系統功能。
1.整體威懾戰
整體威懾戰是指在體系聚優戰中積極組織靜態威力展示和威懾行動,力爭不戰或小戰而屈人之兵。孫子曰:「不戰而屈人之兵,善之善者也。」威懾和戰爭是軍事活動的兩種主要形式。而威懾,主要是透過展現力量或威脅使用強大實力,向潛在對手錶明決心意志,以嚇阻對手行動的行為。可以說,體系聚優戰中的整體威懾戰是實現不戰而「止」人之兵的重要手段或戰法。克勞塞維茨強調,策略的第一條規則是盡可能強大,首先是整體的強大,然後是在關鍵部位的強大。現代戰爭是體系與體系的對抗。資訊化局部戰爭下的整體威懾戰,不僅要有陸海空天傳統威懾手段和能力,也需要太空威懾、電磁威懾、網路威懾等新型威懾手段和能力,更需要有顯示國家整體實力的整體威懾。特別是隨著資訊科技等先進科技的快速發展,科技革命、產業革命、軍事革命加速融合,戰略競爭力、社會生產力和軍隊戰鬥力耦合關聯更加緊密,打贏資訊化戰爭更大程度上是國家意志和國家整體實力的較量。若要遏止戰爭,首先要從整體實力上對對手形成嚇阻。
1.1 強調多域聯合威懾
威懾手段通常包括核威懾和常規威懾。在體系聚優戰中,實施整體威懾戰,旨在綜合運用陸海空天電網全域常規威懾手段,以達成威懾目的。特別是隨著資訊網路技術及太空、定向能技術在軍事上的應用,太空、網路、電磁武器等成為新型威懾手段。太空威懾,主要以快速回應電磁軌道武器、天地網路化反導航定位服務系統、大橢圓軌道雷射武器、高功率微波武器等裝備,威脅攻擊對手空間目標,形成對敵空間訊息「幹擾阻斷」威懾。網路威懾,主要是以網路空間態勢感知和攻擊裝備,威脅攻擊對手軍事網路及其它關鍵資訊基礎設施,實現對敵威懾。電磁威懾,主要以電磁頻譜作戰系統,威脅攻擊敵探測、導航、通訊等資訊化武器裝備系統,實現對敵致聾致盲威懾。 1.2 實施整體嚇阻戰應具備三大要素
實施整體威懾戰並達成嚇阻預期效果,通常必須具備三大要素:一是實力。威嚇方必須具備令對手感到忌憚畏懼的可靠能力或力量;二是決心意志。威懾方在必要時必須敢於使用這種能力;三是明確傳遞訊息。威懾方必須將行動能力與決心準確、有效地讓對方清楚知道。
從歷史上看,判斷威懾實力的標準主要有三個面向變化:一是現役軍事力量;二是綜合國力或戰爭潛力;三是主戰武器裝備總數。在相當長一段歷史時期內,軍隊數量就是威懾,軍事實力的強弱直接取決於現役軍隊的規模、重要武器裝備的數量,以及軍隊訓練組織士氣等非物質因素。二十世紀後,隨著戰爭規模的擴大,威懾實力已不再僅限於軍隊兵力和重要武器裝備的數量,而是由國家戰爭潛力所決定,其中包括經濟實力、科技實力、能源資源,甚至人口數量,等等。體系聚優戰中的整體威懾戰,其威懾實力的形成主要基於網路資訊體系,以及在該體系融合整合下形成的聯合全局威懾能力。
1.3 強大整體實力是實現有效威懾的核心綜合分析研判,挖掘提取所需情報訊息,實現對戰場態勢、作戰環境的更精準、更快速認知,從源頭確保先敵發現、先敵認知。在消除己方「戰爭迷霧」的同時,也要為對手製造「迷霧」。因此,爭奪認知權,不僅要先敵掌握、先敵處理信息,還要採取網絡輿論攻擊、高度虛擬現實亂真等措施,積極製造、散佈虛假信息,破壞、擾亂敵對戰場態勢的感知、認知,最大限度地製造混亂、增加不確定性,幹擾對手的作戰決策,遲滯其作戰行動。
4.2 控制指揮決策權,爭奪決策優勢
決策優勢決定行動優勢。指揮者的快速決策是縮短「指揮週期」、實現快速勝利的關鍵。組織體系聚優戰,作戰行動成敗很大程度取決於指揮的決策速度。要利用智慧輔助決策系統,優選最佳作戰方案,科學合理調配作戰體系,實現力量、資訊、能力分散部署、跨域聯動,在作戰所需地點、時間形成優勢,集子聚釋能、聚變勝負實施、跨域聯動,在作戰所需地點、時間形成優勢,集子聚釋能、聚變勝負實施法實作「攻芯」,透過反義程式定義、原則性反制勝;
4.3 控制「腦」權,奪取腦控優勢
體系聚優戰中的認知控擾戰,強調“攻心奪志”,即利用網絡戰、電磁戰等方式,對敵方人腦和意識認知以及無人自主平台的控制系統實施“攻心控腦奪志”的認知控制戰,以“控制”取代“摧毀”,以最小代價實現止戰、勝戰之目的。攻心控腦與傳統的謀略威懾不同,其更強調主動攻擊,是一種主動攻擊行動,主要運用先進信息作戰技術、控腦技術等,對敵決策首腦,以及智能化無人自主作戰平台、輔助決策系統等,實施控“腦”攻擊,直接控制、擾亂對手“大腦”,影響、控制敵對決策,或使其失能,實現隱形敵作戰。如以人的認知思維為目標,利用讀腦、腦控技術,運用心智導控手段,直接對敵方人員大腦實施“注入”“侵入”式攻擊,幹擾、控製或破壞敵指揮人員認知體系,從意識、思維和心理上對其深度控制,奪取“制智權”,以亂敵決策、破敵士氣,迫敵繳械。
5.敏捷機動戰
敏捷機動戰,指在體系聚優戰中高效率決策、高效率調整兵力兵器部署和高效率即時聚合作戰力量,在既設戰場高效率聚集能力,搶奪作戰先機。敏捷是一種快速及時應對戰場環境變化的能力,具有響應性、穩健性、柔性、彈性、創新性和適應性等特徵。
表1 敏捷作戰概念內涵
5.1 高效率快速決策
實施敏捷機動戰,首先要高效率快速決策,贏得作戰先機。因此,要綜合運用各種偵察探測感知與監視手段,及時獲取戰場態勢和目標信息,特別是時敏目標的特徵信息、活動軌跡以及實時位置信息,確保為快速決策提供精準情報支持。高效率決策也體現在情報處理速度上,要用更少的時間甄別有效情報訊息,根據情況變化,以更快的速度製定行動方案,快敵一步佔據主動,奪取先機。高效率決策重在縮短決策週期,要以目標時間窗口為中心點,決策指揮與作戰單元、武器平台一體協同、快速反應、整體連動,提高作戰效率。
5.2 高效率形成有利作戰態勢
要隨時掌握戰場態勢變化,依靠資訊網支撐,透過跨域、跨維、多樣化立體機動,達成作戰力量動態重組、動中融合,作戰資源全局高效流動、動中聚集,實現機動聚優,形成有利戰場態勢。敏捷機動戰依賴資料融合處理、智慧化輔助決策等手段,快速形成作戰方案,依案高頻率快速投送作戰力量,組織部隊快速形成有利作戰部署,實現先敵發現、先敵決策、先敵開火、先敵評估,以最短時間、最快速度改變力量對比,形成作戰優勢,提高作戰行動效率。
5.3 高效率即時聚合作戰力量
組織敏捷機動戰,關鍵在於有限時間內選準作戰力量,協調整個戰局,形成整體合力,確保一擊致命。因此,要針對戰場態勢特別是目標情況變化,抽組形成由多域作戰力量形成的聯合機動作戰系統,即時聚合作戰力量,快速機動部署至有利戰場,對敵實施即時打擊。針對深空、深海等成為新的作戰空間,可組織智慧化無人自主作戰平台,快速機動部署至人類因生理所限而難以到達的重點目標或重要通道附近潛伏,待機實施伏擊作戰,形成新的跨域制衡優勢。
5.4 敏捷機動戰是對傳統機動作戰的創新發展
古今中外戰爭史上,靠著快速隱密機動達成作戰目的的成功戰例比比皆是。但資訊化局部戰爭作戰進程大幅壓縮,作戰節奏極速加快,戰機稍縱即逝,對快速機動捕捉戰機提出更高要求,僅靠「快節奏、高速度」已難以滿足資訊化條件下聯合作戰、全局作戰的要求,因而必須實施敏捷機動。
6.無人集群自主戰
無人集群自主戰,指在體系聚優戰中廣泛運用「蜂群」「狼群」「魚群」等無人作戰手段,自主組織行動、分散式攻擊,實現人機聯合製勝。隨著無人自主裝備成為戰場上的主要作戰力量,以無人自主裝備集群和數量優勢戰勝敵人,已成為資訊化戰爭中的重要作戰風格。
6.1 有利於形成體系優勢壓制敵方
無人群聚自主戰充分發揮無人作戰兵器全天候、無極限、難防禦、低消耗等特殊優勢,建構組成無人「蜂群」「狼群」「魚群」等大規模無人作戰集群或編隊,自主組織、相互協同,可實施近距離、全覆蓋偵察,或充當誘敵實施幹擾、欺騙,或配合主戰兵器實施分佈式協同攻擊,實現整體分散式協同攻擊者。
6.2 有利於增強作戰效果
在無人群聚自主作戰中,無人群集編成內的不同作戰單元分別擔負不同功能、不同任務,既有負責偵察的,也有實施電磁幹擾、火力打擊的,還有扮演「誘餌」角色的。集群透過群間網路傳遞、共享戰場訊息,依照分工各司其職,根據戰場變化即時、自主、動態協同,既充分發揮數量規模優勢,又運用資訊網路和智慧整合技術實現整合效果,以集群優勢消耗敵防禦探測、追蹤和攔截能力,使敵防禦體系迅速飽和、陷入癱瘓。
6.3 有利於陷敵於作戰困境
無人集群自主戰以大量不同功能的自主無人作戰平台混合編組,形成集偵察探測、電子乾擾、網路攻擊、火力打擊於一體的無人作戰集群,對同一目標或目標群實施多方向、多波次、持續不斷的攻擊,將使敵難以作出有效反擊。
7.精確點殺戰
精確點殺戰,是指在體系聚優戰中精準獲取情報,實施多域精確打擊,力爭打一點撼全局,實現作戰效益最大化。資訊化局部戰爭是體系與體系之間的整體對抗,實施精確點殺戰,對敵方作戰體系重要節點與關鍵環節實施精確打擊,破壞敵作戰體系,降維敵作戰能力,將形成事半功倍的作戰效果。
7.1 實現作戰的高效費比
以最小代價實現最大作戰效益是作戰雙方都在追求的目標。隨著資訊科技在軍事領域的廣泛應用及資訊化戰爭來臨,精確導引武器、智慧化動能武器、察打一體無人機以及雷射武器等廣泛裝備部隊;透過運用大數據、人工智慧等技術,精確計算所需兵力兵器已成為可能。這些都為實現精確點殺戰,以較小代價達成作戰目標,實現作戰高效費比,提供了物質和技術條件。
7.2 打關鍵節點目標是重要選項
精確點殺戰重在打關鍵、打節點,不打則已,打則必痛、打則必勝,打一點破敵體系、撼動全局。打擊的目標不僅限於敵分散部署的艦機等,還應針對敵指揮中心、重要樞紐,甚至主要將領、指揮等局部、動態、時敏目標或獨立目標實施打擊,追求威懾震撼和破敵體系效果。針對將昂貴的大型裝備功能分解到大量小型平台、實施兵力分散部署這一分佈式戰術,運用精確打擊火力對其進行「點殺」式打擊,也將是一個有效對策。
7.3 大範圍體系支撐是基本條件
實施精確點殺戰,離不開大範圍體系支撐。圍繞著實現作戰目標,從分散部署的各作戰域抽調所需兵力兵器,在網路資訊體系支撐下,動態融合形成精確打擊體系,實現整體連動、體系聚能,透過合理夠用的火力集中對目標實施打擊,達成精確用兵、精確釋能。實施精確點殺戰要做到精確,需要整個作戰體系內各環節緊密銜接,不能有絲毫差錯。 2011年美軍擊斃賓拉登作戰行動,可以說是戰略體系支撐下的一次典型的戰略精確點殺作戰行動。
7.4 離不開精確情報保障
在精確點殺戰中,精確情報保障始終是達成作戰目標的關鍵。因此,戰前應動用各種手段蒐集敵方各種情報資料信息,特別要對敵方目標作出精準分析研判。作戰行動中,應動用各種感測器和情報偵察手段,適時精準掌握敵方目標變化及動態目標狀況,為實施精確點殺戰提供有力有效的情報保障。美軍對蘇萊曼尼的定點清除行動,就是一場典型的以高效情報體系支撐的精確點殺戰。
8.補給斷鍊戰
補給斷鏈戰,是指在體系聚優戰中組織精銳力量,打敵後勤物資和裝備供應補給鏈、補給線和補給基地,破敵失去補給而退出戰鬥。針對敵後勤補給線長、裝備保障攤子大等弱點,組織精銳力量建構「斷鍊戰」作戰體系,對敵後勤物資和裝備供應補給鏈、補給線和補給基地等,實施持續、精確、毀滅性打擊,將使其因失去補給而難以為繼,不得不退出戰鬥。
8.1 供應保障鏈對作戰全局影響巨大
後勤裝備保障是作戰的重要基礎。後勤物資和武器裝備持續不斷的供應補給,最後決定一支軍隊作戰部隊的規模、能否作戰、在什麼季節作戰、在哪裡作戰、能離開後方基地多遠、能作戰多長時間、機動的速度多快,等等。在資訊化戰爭中,戰場物資消耗呈指數級上升,作戰對後勤裝備保障的依賴程度不僅沒有減小,反而越來越大,而且保障的專業化程度要求也越來越高,特別是現代化作戰裝備器材型號規格紛繁多樣,混裝運輸體積巨大,部隊部署更加分散,對運力也提出非常高的要求,這使線路、通信和運輸比以往任何時候都更加重要。供應保障鏈的穩定高效運作和持續不間斷的供應保障,是作戰制勝的關鍵,對作戰全局產生巨大影響。
8.2 打擊重心是斷敵供應保障鏈的關鍵節點
補給斷鍊戰的作戰重心是打擊敵方供應保障鏈的關鍵環節,透過斷鍊使其喪失持續保障能力。因此,組織補給斷鍊戰應主要以敵方地面鐵路公路運輸線、海上補給船隊、軍事徵用的商船和戰鬥支援艦,空中大中型運輸機,以及後方補給基地等作為打擊目標。例如打擊敵方海上供應保障鏈,斷敵燃料、彈藥、淡水、食物補給,將使敵航母戰鬥群失去持續作戰能力,進而影響一場戰役的勝負。
8.3 重在選準時機活用戰法
組織實施補給斷鍊戰,選擇有利打擊時機至關重要。補給斷鍊戰的打擊時機,應選擇敵補給機動時組織實施,以出其不意攻其不備的隱蔽戰法,對敵補給車輛、艦船和運輸機實施突然打擊,終止其補給行動。具體戰法通常有隱蔽伏擊戰,組織精幹力量埋伏在敵運輸工具必經路線和航線上,伺機實施隱密性突然打擊;隱形奇襲戰,使用潛艦、隱形戰機等隱蔽前出,對敵運輸目標實施打擊,以奇制勝;遠程精確補給
9.體系毀癱戰
體系毀癱戰,指在體系聚優戰中,綜合採取破網、斷鍊、打節點等多種手段,幹擾、遲滯、破壞甚至癱瘓敵作戰體係有效運轉,削弱敵作戰體系功能。體系毀癱戰的本質,是透過削弱敵作戰體係要素間的關聯性與結構力,使體系功能退化,無法發揮能力倍增作用。
9.1 作戰目標是使敵作戰體系運作失序
在資訊化戰爭中,交戰雙方作戰體係都有其內在秩序,而這種秩序是維繫和支撐作戰體系運作的關鍵所在。能夠維護和駕馭作戰體系內在秩序的一方將獲得優勢,反之則處於劣勢。因此,體系毀癱戰應確立亂敵制勝機制、致敵作戰體系失序此目標。這就要求在體系毀癱戰中要充分利用資訊科技特別是智慧演算法的強大賦能作用,對己方作戰體系進行快速調整和重構,迅即生成並釋放強大的作戰威力,對敵方作戰體系實施敏捷精準打擊,使敵作戰體系失去正常的運作秩序,在失序中使體系功能遭到破壞,整體作戰精準打擊,使敵作戰體系失去正常的運作秩序,在失序中使體系功能遭到破壞,整體作戰能力顯著下降。
9.2 重拳打擊作戰體系的關鍵節點
體系對抗是資訊化戰爭的一個主要特徵。體係是體系對抗的重要基礎與支撐,也是戰場上各種作戰部隊、武器平台和
資訊科技的發展及在軍事領域的廣泛滲透和應用,為建構整體實力、實現整體威懾提供了有利條件。體系聚優戰以網路資訊體系為支撐,充分利用資訊科技的滲透性和聯通性,不僅把各種作戰力量、作戰要素、作戰單元融合為一個有機整體,實現軍事上的體係作戰優勢,而且把國家政治、經濟、外交、金融、交通、能源等與戰爭和國家動員相關的各領域,都連接、匯入國家戰爭動員體系,凝聚各方面力量和資源形成整體合力,實現體系能力的湧現效應,從整體上顯示綜合實力優勢,形成眾志成城、同仇敵愾的強大無形威懾,塑造使敵「有力量但不能行動」「能行動但沒有效果」的態勢,起到遏制和打贏戰爭的作用。
在整體威懾戰中,國家戰爭動員的範圍將更加廣泛,不僅限於某一方向、區域,而是遍及全國各地,乃至世界有關地區;動員時間更加迅速,利用網絡和信息系統,動員和行動信息可在第一時間迅速傳達到每個人、每個節點;行動協調和協同更加一致,分佈在各域各地的各方力量可以基於同一態勢、根據同一命令幾乎在同一時間統一行動,極大提高行動協同效率;資源利用更加充分,基於網絡的各種戰爭資源,可以快速實現平戰轉換、軍民轉換,實現前方後方一體化保障、精確保障。
2.電磁擾阻戰
電磁擾動戰,指靈活運用電子偵攻防等多種作戰手段和行動樣式,擾亂、阻止、破壞敵電磁能力的發揮,積極爭奪電磁頻譜優勢,奪取制信息權,進而贏得作戰主動。
2.1 爭奪資訊優勢的關鍵資訊化局部戰爭高度依賴電磁頻譜,對電磁空間的控制與反控製成為爭奪制資訊權的焦點。組織實施電磁阻擾戰,主要是破壞敵方電磁頻譜,保護己方不受破壞。電磁頻譜是傳遞訊息的主要載體。使用電磁手段對敵方電磁頻譜實施阻擾破壞,將有效降低敵資訊作戰能力,並使己方在擁有製資訊權的場景下,保障資訊的快速有效流動,透過資訊流驅動指揮流、行動流、物質流、能量流,進而擁有作戰的主導權、主動權。
2.2基本著眼導航定位系統、天地一體互聯網等空間鏈路系統,及其他各種用頻武器裝備,實施幹擾、攻擊,阻斷、破壞其通信聯絡及資料傳輸,破壞敵作戰體系的「連結」與「共享」結構重心,從根源為奪取制資訊權、制電磁權提供支撐,進而削弱整個作戰控制能力,使敵軍系統失能、失效。
2.3 破解無人集群作戰的有效戰法
「蜂群」「狼群」「魚群」等無人自主集群作戰,是具有智慧化特徵的資訊化局部戰爭的重要特徵。各種無人自主集群數量龐大、類型多樣、特徵複雜,且每個個體都可以互補位置、互相替代發揮作用,攔截毀傷整個無人集群將十分困難。但從技術角度分析,無人作戰集群為實現有效協同,每個個體之間必須進行資訊共享與互動。無人集群間通訊協同一旦受到干擾,將無法分享戰場態勢與訊息,無法相互協同行動,也就很難發揮應有作戰效能。這就給對方實施通訊攔截與電磁幹擾提供了機會。因此,實施電磁頻譜戰,對無人集群的資訊通訊網路實施幹擾、攻擊,破壞其資訊共享與交互,將使無人集群中每個個體無法實現有效協同,從而失去作戰能力。
3.網路破擊戰
網路破擊戰,指綜合運用網路和電腦等技術以及其他有效手段,圍繞著資訊、資訊網路的控制權而進行的軍事對抗行動,是網路空間作戰、爭奪制網權的主要作戰樣式。其主要作戰行動既有軟殺傷也有硬摧毀,以軟為主、軟硬結合。其中,軟殺傷主要是網路攻擊,即綜合利用阻塞攻擊、病毒攻擊等手段,對敵資訊網路、指揮系統、武器平台等進行阻滯與攻擊,使敵網路、指揮資訊系統等難以有效運作甚至癱瘓;硬摧毀主要是利用精確火力打擊、高能量微波、電磁脈衝以及反輻射攻擊等手段,癱毀敵資訊資訊網路和物理設施,摧毀敵人實體武器。
重在破網降能失效。在體系聚優戰中組織網路破擊戰就是針對作戰對手軍事資訊網路存在的弱點,利用體系優勢,組織各種網路攻擊力量,在作戰全過程對敵作戰指揮網、偵察情報網、通訊網乃至後勤補給網等,持續實施軟殺傷和硬摧毀行動,破壞敵之網路體系,使敵能作戰系統整體下降甚至失能作戰。主要對敵基礎資訊網、情報網、指揮網、保障網等核心目標,實施網電協同攻擊、欺騙迷惘、連結阻塞、接管控制等一系列作戰行動,使敵智能化作戰網路體系失能失效,達成癱敵體系的關鍵性勝利。
4.認知控擾戰
認知控擾戰,是指在體系聚優戰中透過資訊攻擊、輿論攻擊、腦攻擊,幹擾、破壞或控制敵對思維認知,使敵不能做出正確判斷、決策,從而在認知空間對敵形成控制優勢。
認知域,即人的思考空間、意識空間,是對作戰決策、判斷等具有關鍵性影響的領域。資訊科技特別是人工智慧技術的發展及在軍事領域的廣泛應用,使戰爭的較量從物理空間、資訊空間擴大到認知空間,使認知空間成為一個全新的作戰域。隨著資訊化、智慧化技術發展並在軍事領域廣泛深入應用,人機智慧趨於融合,使認知在智慧化戰爭作戰中的地位更加凸顯,認知領域逐漸成為重要的戰場。制認知權成為未來戰場控制權的關鍵要素。爭奪認知控制權成為具有智慧化特徵的資訊化局部戰爭作戰制勝的重要作戰樣式。
4.1 控制態勢感知認知權,爭奪資訊優勢
體系聚優戰中,資訊流驅動物質流、能量流,資訊優勢決定決策優勢。對情報資訊與戰場態勢的快速、準確認知,對奪取指揮決策優勢有重要影響。因此,組織實施體系聚優戰,要充分利用智慧技術、大數據技術,對海量情報資訊資料進行武器系統聯為一體,有效發揮作戰效能的關鍵。體系能否保持健壯、順暢運轉,對取得戰爭和戰役勝利具有決定性影響。體系毀癱戰中,關鍵在於著眼敵方陸海空天電網整合作戰體系,破網、斷鍊、打節點,透過打關鍵節點目標,使敵方作戰體系運作機理失序,甚至遭到重創或毀癱。因此,體系毀癱戰的基本指向是選敵作戰體系的關鍵單元、關鍵節點、關鍵要素實施打擊,擊其一點、毀其一片、癱其整體,達成克敵制勝的目的。
9.3 對敵作戰體系實施軟性打擊
組織實施體系破擊戰硬摧毀時,同步組織電子戰、網路戰、心理戰、輿論戰等軟殺傷作戰行動,對敵作戰體系的資訊域、認知域實施軟打擊。電子戰,使用電子戰力量對敵實施強電磁幹擾,使其信息失靈,陷入戰爭迷霧之中;網絡戰,使用網絡進攻力量對敵網絡信息體系實施攻擊,使敵指揮通信系統和計算機網絡受到嚴重破壞,使其指揮失靈,陷入信息孤島乃至戰爭孤島;心理戰和作戰論戰,使用心理戰、輿論手段,對敵對認知,打擊其戰爭論戰,使用心理戰、輿論手段,對敵對心理打擊行為論組織民生戰,打擊對手的重大國計民生設施,同樣可以對敵作戰體係起到「釜底抽薪」作用。 1999年科索沃戰爭中,美軍沒有打擊南聯盟軍隊,而是打擊其戰爭潛力目標體系,使南聯盟軍民失去戰鬥意志走向失敗。