Chinese Military History <2005> People’s Republic of China’s New Military Transformation
繁體中文:
迎接世界新軍事變革的挑戰,積極推動中國特色軍事變革,中央軍委所做的重大戰略決策,總部推出了一系列重大舉措。 最大的措施是決定2005年前軍隊再裁減員額20萬人。
2002年,中央軍委會正式頒布《實施軍隊人才戰略工程規劃》;四總部相繼下發了《關於加強作戰部隊裝備技術保障幹部隊伍建設若干問題的規定》、《關於進一步做好幹部交流工作的意見》 和《關於提升參謀隊伍素質若干問題的意見》,全軍部隊人才培育的步伐明顯加快。 2002年10月,大軍區職領導幹部高科技知識訓練班開學,重點研究資訊化戰爭與軍隊資訊化建設的問題。 各總部機關也相繼開辦高科技知識培訓班。 抓資訊化建設從高級幹部和領率機關抓起,展現出一年來軍事變革的重點和特色。
軍委會總部的重大舉措直接提升了戰鬥力。 總參謀部部署年度訓練任務時突出強調創新前瞻性作戰理論,以新的需求牽引訓練內容和訓練方法的改革。 總政治部直接組織了修訂新的《政治工作條例》,強調政治工作要為推進中國特色軍事變革服務,全軍政工幹部大規模地展開學習新《政治工作條例》。 總後勤部大力推動三軍聯勤和後勤資訊化建設,邊遠部隊遠距醫療、軍隊住房管理等資訊系統都有了新的飛躍。 裝備系統官兵抓住戰略機會期,加速推進軍隊武器裝備跨越式發展,努力使現有裝備特別是新裝備成建制、成系統形成作戰能力和保障能力。
提高官兵素質,是推動中國特色軍事變革的重要內容。 適應建設資訊化軍隊、打贏資訊化戰爭,必須具備與之相適應的高素質。 至2003年,不管是基層官兵或師團主官,不管是低學歷幹部或高學歷幹部,都有強烈的危機感。 許多領導幹部率先垂範,下決心提升指揮資訊化戰爭的能力。 全軍各部隊狠抓人才工作的措施力度越來越大,為推動中國特色軍事變革提供了強而有力的人才和智力支持。裁軍20萬
2003年9月1日,中央軍委主席江澤民在出席國防科學技術大學50週年慶典活動時鄭重宣告:黨中央、中央軍委決定,將在“九五”期間裁減軍隊員額50萬的基礎上,2005年 前軍再裁減員額20萬。 這是新中國成立以來軍隊進行的第10次重大精簡整編,引起國際社會的高度關注,有輿論稱,「以大規模裁減軍隊員額為標誌,中國新軍事變革的大幕正式拉開」。
推動中國特色的軍事變革,必須依照實現資訊化的要求,科學確立軍隊建設的戰略目標、發展思路和具體步驟。 然而,軍費供給不足,是新軍事變革中包括中國在內的各國軍隊普遍遇到的難題。 從世界範圍來看,世界各國國防費用佔GDP的比例一般都在2%—4%,而中國只佔1.5%左右。 以2002年為例,中國國防開支為1,694.44億元,約200億美元,只相當於美國的6%左右。 軍費大部分用於250萬人員的生活費、活動維持費,用於裝備和訓練的相對較少。
軍事專家指出,高技術和資訊化武器裝備的購置費和維修費成幾何級數上升。 解決軍費供需矛盾,讓有限的軍費帶來最大的效益,其最佳想法是減少人員數量,提高軍隊品質。 新軍事變革對軍隊規模的要求是合理、適度、夠用,中國軍隊員額從250萬減少到230萬以後,將更可能使有限的戰略資源得到更有效的使用,發揮出更大效益。 大規模裁減員額並非僅僅“減人”,其實質是對軍隊現有體制編制的結構性調整,軍隊體制編制調整改革必須貫徹精兵、合成、高效的原則,只有深入研究高技術戰爭對軍隊體制編制 的影響,著重解決領導指揮和管理體制以及部隊編成中存在的矛盾和問題,才能建立起具有中國特色的軍事體制。
軍事專家認為,減少數量,提高質量,優化軍隊內部結構,增大高科技含量,加強綜合集成建設,逐步建立符合現代戰爭要求的體制、編制,是加速人民解放軍現代化建設和更好地做好軍事 抗爭準備的必然選擇。 堅定不移地走中國特色的精兵之路,是軍隊建設的既定方針。 壓縮軍隊員額,是不斷適應世界新軍事變革發展趨勢,服從服務國家經濟建設大局的需要。 這次裁軍之後,中國軍事力量的規模雖然出現一定程度的壓縮,但戰鬥力必將得以提高,維護國家主權和領土完整的能力定能進一步增強!
根據中央軍委會的統一部署,部隊的精簡整編工作將於2003年年底全面展開,精簡整編單位的編餘士兵多數要安排退出現役,其中包括未服滿服役期的編餘義務兵和士官。 解放軍總部已對此工作作出了具體安排:根據部隊調整精簡的需要,允許部分未服滿規定年限的義務兵和士官提前退出現役;精簡任務較重的單位的退役義務兵和復員士官,可安排提前 離隊;撤銷並改編為預備役部隊的單位的轉業士官,提前移交地方安置部門安置。 對因軍隊調整精簡提前退役士兵的安置,要與服役期滿的退役士兵同等對待,按時接收,納入2004年安置計劃。 其中,對服現役滿1年的城鎮退役義務兵,要按照服役期滿退伍義務兵的有關規定安置;對服現役滿9年的退役士官,要按照服滿現役10年以上退役士官的有關規定安排工作 。 對撤銷和改編為預備役部隊的單位的提前離隊的轉業士官,由各大單位派專人將檔案送地方有關安置部門審核,對符合條件的,簽發《接收安置通知書》,部隊即可組織轉業士官 離隊;本人要求復員的,經批准也可作復員安置。 對符合退休條件的士官,應依照國務院、中央軍委會頒發的《中國人民解放軍士官退出現役安置辦法》的規定,及時下達退休命令,並逐級上報列入移交安置計劃。 提前退役的士兵依實際服役年限和相應的標準發放退役費和物資,對該發放的經費和物資要及時足額地發放到退役士兵手中。 提前離隊的轉業士官按本年度正常時間離隊的轉業士官一樣對待,工資、福利、醫療待遇和服裝發放按有關規定辦理。
軍隊體制編制調整改革後,中國軍隊將有司務長、俱樂部主任等數10種幹部職務、數萬個幹部職位改為士官擔任。 改由士官擔任的專業職位的人員,從2004年起納入軍院中專以上學歷訓練。 為確保這項工作的順利進行,實現人才等職位及2003年年底能接替的要求,士官任職前培訓擬採取中專學歷培訓與短期培訓相結合的方式進行。 其中,從經過院校2年以上學歷培訓的現有士官中選拔接替對象的專業崗位,進行3至5個月的短期培訓。 對現有士官學歷培訓規劃中無相同相近專業、選不到接替對象的專業崗位,組織中專學歷培訓,學制2年,在校學習1年,在崗位實習1年;每年一季度招生並開學 ,在校學習期間不休暑假,2003年底前回部隊實習。附:前九次裁軍資料
第一次精簡整編:新中國成立初期,解放軍總兵力達550萬人。 1950年6月,中國軍隊參謀會議精簡整編方案中規定軍隊精簡為400萬,當年即復員23.9萬餘人。 不久,抗美援朝戰爭爆發,精簡整編工作終止。 截止到1951年底,軍隊人員達627萬人,是中國軍隊史上兵力最多的時期。
第二次精簡整編:1951年11月中央軍委召開整編會議,規定到1954年把軍隊總人員額控制在300萬人左右。 1952年1月,毛澤東批准《軍事整編計畫》,軍隊總定額縮減至300萬人左右。
第三次精簡整編:截至1953年9月底,軍隊人數減少到420萬人左右。 當年12月,中國軍事系統黨的高級幹部會議決定,把軍隊簡編為350萬人。 到1954年6月軍隊已精簡47.2萬餘人,年底基本完成計畫。
第四次精簡整編:1957年1月,中央軍委擴大會議,通過了《關於裁減軍隊數量加強質量的決定》,確定軍隊總人數再裁減三分之一,要求3年裁減130萬人,壓縮至 250萬人左右。
第五次精簡整編:1975年6月24日至7月5日,中央軍委擴大會議決定3年內將軍隊減少60萬人。 到1976年,軍隊總人數比1975年減少13.6%。 後來由於「四人幫」的干擾破壞,精簡整編任務沒有完成就停了下來。
第六、七、八次精簡整編:1980年3月,中央軍委決定軍隊再次進行精簡整編,大力精簡機關,壓縮非戰鬥人員和保障部隊,部分部隊實行簡編,將一部分部隊移交地方。 同年8月15日,中共中央批轉了中央軍委會《關於軍隊精簡整編的方案》。 1982年9月,中共中央和中央軍委決定軍隊進一步進行精簡整編。 1985年5月底6月初,中央軍委會決定裁減軍隊員額100萬人,精簡整編工作到1987年初基本結束。
第九次精簡整編:1997年9月,江澤民同志在黨的十五大報告中宣布,在80年代裁減軍隊員額100萬人的基礎上,中國將在今後3年內再裁減軍隊員額50萬人。 到1999年底,裁軍50萬人的任務已經完成,20餘萬軍隊幹部退出現役轉業地方工作。 這是新中國歷次裁減軍員額中幹部精簡比例較高的一次。科技練兵
2003年,中國軍隊和武警部隊圓滿完成了年度訓練任務,在理論創新、實戰演練、反恐訓練、人才培養、從嚴治訓等5個方面取得新成果。
一、用發展的軍事理論指導軍事訓練新實踐。 軍隊和武警部隊軍事訓練依照以資訊化帶動機械化、以機械化促進資訊化的要求,深入進行資訊作戰、非接觸作戰、聯合作戰等作戰樣式的理論研究,創新軍事理論和作戰思想,引導軍事訓練 改革的深化,推動科技練兵朝向資訊化方向發展。
二、突出提升打贏能力,以軍事鬥爭準備為龍頭,部隊訓練貼近實戰。 南京、廣州軍區加大實兵實裝演練力度,圍繞戰術技術難點問題開展攻關,並取得了一批有價值的成果。 瀋陽、北京、濟南軍區在近似實戰的條件下練指揮、練戰法、練協同、練保障;海軍、空軍、第二砲兵注重強化諸軍兵種聯合作戰指揮演練;蘭州、成都軍區深化高寒山地作戰 演練,研究解決機動、生存、指揮、協同、保障等重點課題;武警部隊加強處突、反恐怖主義和防衛作戰演練。 全軍積極進行區域協作訓練創新實踐,對聯合戰術兵團作戰理論和區域協作訓練機制等關鍵性問題展開重點攻關。
三、依據國家賦予軍隊反恐怖鬥爭新的軍事任務,擔負反恐怖任務的部隊紮實進行反恐怖軍事鬥爭研究和訓練實踐。
四、人才培育有新的措施。 軍院校著眼培養高素質新型軍事人才,深化院校體制編制調整改革,推動了院校教學改革的深入發展。 各部隊進一步加大訓練機構建設與教學改革力度,為基層培養了大批優秀指揮士官。
五、軍隊堅持依法治訓,嚴格依綱施訓,大力進行崗位練兵活動,契約戰術演練品質提高,部隊正規化訓練水準不斷提高。部隊改革
2003年6月10日,解放軍總政治部發出通知,要求全軍和武警部隊官兵認真學習貫徹《中共中央關於印發(「三個代表」重要思想學習綱要)的通知》精神,加深對「三個 代表」重要思想的理解,在全軍興起學習貫徹「三個代表」重要思想的新高潮。 總政治部組織出版部門迅速將《「三個代表」重要思想學習綱要》印發全軍,並特別發出通知,要求全軍團以上領導幹部和機關幹部要認真研讀江澤民同志一系列重要著作,以《綱要 》為線索,從整體深入系統地學習掌握「三個代表」重要思想。 基層要以《綱要》為主要輔導材料,選讀江澤民同志的若干重要著作,深入學習掌握「三個代表」重要思想的基本精神和基本觀點,把全軍官兵的思想和行動進一步統一到鄧小平理論和 「三個代表」重要思想上來,把智慧和力量進一步凝聚到實現黨的十六大確定的各項任務上來,堅決聽從黨中央、中央軍委和江主席的指揮,為實現全面建設小康社會的宏偉 目標,為軍隊的革命化、現代化、正規化建設努力奮鬥。
6月18日,全軍學習貫徹「三個代表」重要思想理論研討會在北京舉行。 會議強調,必須更加牢固地確立「三個代表」重要思想在軍隊建設中的指導地位,把廣大官兵的意志和力量凝聚在「三個代表」重要思想的旗幟下,進一步打牢堅持黨對軍隊 絕對領導的思想理論根基,使全軍部隊始終保持與時俱進的精神狀態,肩負起神聖使命,積極推進中國特色軍事變革,實現軍隊現代化跨越式發展。
6月中旬,經中央軍委批准,解放軍總政治部就認真貫徹中共中央通知精神,在全軍興起學習貫徹「三個代表」重要思想新高潮提出意見。
經中央軍委批准,總政治部委託國防大學分別於8月下旬和9月中旬舉辦兩期全軍軍職以上領導幹部學習貫徹「三個代表」重要思想輪班班,來自全軍和武警部隊的近 百名軍以上領導幹部分別進行為期10天的學習。 輪班以胡錦濤同志「七一」重要講話精神為指導,按照中央《通知》和總政《意見》的要求,以《「三個代表」重要思想學習綱要》和《江澤民國防和軍事建設思想學習 綱要》為基本線索,組織學員學習了江澤民同志的著作和黨的十六大報告。 為了加深對所學內容的深刻理解和系統把握,了解掌握當前最新理論研究成果,輪班也分別邀請中央宣講團相關成員、中央文獻研究室、國家發展和改革委員會、北京大學以及軍隊思想理論戰線 的專家、學者,作了專題講座和輔導報告。 透過輪訓,學員們對「三個代表」重要思想的時代背景、實踐基礎、科學內涵、精神實質和歷史地位的認識有了新的提高,進一步加深了對江澤民國防和軍隊建設思想的理解,增強 了以「三個代表」重要思想指導部隊改革和建設,開創各項工作新局面的使命感和責任感。
2003年,全軍和武警部隊廣泛深入學習學習實踐「三個代表」重要思想,為全面建構小康社會做貢獻教育活動。 透過教育,廣大官兵進一步堅定了對黨的創新理論的政治信仰,增強了自覺運用「三個代表」重要思想推進部隊改革建設、為全面建設小康社會做貢獻的責任感和使命感。
根據解放軍總政治部相關部門負責人介紹,教育活動分成兩個階段實施,上半年重點學習了黨的十六大報告,集中進行專題教育;下半年貫徹胡錦濤總書記在省會級主要領導幹部 學習貫徹「三個代表」重要思想專題研討班上的重要演說和黨中央、中央軍委的部署,結合學習江澤民國防和軍隊建設思想,進一步把教育活動引向深入。 教育中,各大單位的主要領導深入部隊具體指導,近千名軍以上領導、萬餘名團以上幹部給部隊講課。 許多部隊請地方黨政領導介紹發展經濟、改善人民生活的舉措;組織觀看鄭培民、範匡夫等先進事蹟報告錄像;組織參觀抗擊非典圖片展,請抗非典英模作報告;舉辦形勢報告會,與專家學者 座談交流等。 官兵們說,在中國特色社會主義事業的偉大旅程中,一刻也離不開「三個代表」重要思想的指引,必須始終堅持,毫不動搖。
各部隊引導官兵運用「三個代表」重要思想的立場觀點方法,深刻理解黨對國家經濟、社會、文化全面進步作出的重大戰略決策,激勵大家以實現中華民族偉大復興為己任,自覺服從服務於 全面建構小康社會的大局。 參加小湯山醫院對抗非典的軍隊醫護人員,奮戰50多個晝夜,為戰勝非典病魔做出突出功績。 黃河、淮河、渭河等流域發生洪水,新疆、雲南等地發生地震,大興安嶺等地區發生火災後,10多萬名官兵舍生忘死衝鋒在搶險救災第一線,協助地方政府轉移安置群眾100多 萬人,運送物資200多萬噸,用熱血和生命捍衛了「小康」建設成果。
專注於把學習成果轉化為推動部隊建設,實現新發展、開創新局面的強大精神動力,是這次教育活動最鮮明的特色。 許多部隊引導官兵查找陳舊思維在訓練教學、教育管理、後勤保障、裝備建設等方面的表現,一項一項加以糾正,樹立起與全面建設小康社會、建設信息化軍隊相適應的訓練、管理和 人才觀念。 各單位積極組織官兵從實戰需要出發大膽改革創新,開發出了野戰指揮控制系統、戰時工作決策系統、模擬模擬訓練器材等一批新成果。 擔負緊急機動作戰任務的部隊,叫響了「練科技精兵,當打贏先鋒」的口號,練技術、強素質,圓滿完成了海訓野訓和實彈發射等任務。 2003年全軍12萬多名官兵踴躍報名參加各類函授學習和自學考試,數千名幹部攻讀軍事專業的碩士、博士學位,中央軍委關於實施人才戰略工程的決策正在變為廣大官兵的實際行動 。
2003年7月底,經中央軍委會批准,由總政治部組織編寫的《江澤民國防與軍隊建設思想學習綱要》正式出版並印發全軍。 中央軍委發出通知,要求全軍官兵以江澤民《論國防和軍隊建設》和一系列重要講話為基本教材,以《綱要》為重要輔助材料,認真學習貫徹江澤民國防和軍隊建設思想,推動全軍學習 貫徹「三個代表」重要思想新高潮不斷深入發展。
中央軍委會7月31日在北京召開《江澤民國防與軍隊建設思想學習綱要》出版座談會。 會議指出,江主席在領導國防和軍隊建設的偉大實踐中,形成了完整系統的國防和軍事建設思想。 江澤民國防與軍隊建設思想,同毛澤東軍事思想、鄧小平新時期軍隊建設思想是一脈相承而又與時俱進的軍事科學體系,是「三個代表」重要思想的重要組成部分,是馬克思主義軍事理論在 中國發展的最新成果,是新世紀新階段軍隊建設與發展的科學指南。 全軍部隊要毫不動搖地將江澤民國防和軍隊建設思想作為指導統領各項工作的根本指針和行動指南。 各級領導幹部要做學習貫徹江澤民國防與軍隊建設思想的模範,帶頭把這科學理論學習好、貫徹好、運用好。
後勤支援
軍隊後勤工作堅持以「三個代表」重要想法統攬各項建設,按照積極推進中國特色軍事變革的要求,加大改革創新力度,加快發展步伐,後勤建設取得顯著成績。
三軍聯勤體制運作良好,透過調整保障關係,多數部隊實現了就近就便保障;開展聯勤優質服務,保證了經費和物資及時足額供應;建立協調協作機制,為平時聯合訓練和戰時聯合 保障創造了條件。
隨著新一輪後勤保障社會化全面啟動,2003年全軍有2179個食堂實施改革;1283個軍人服務社進行了撤、並、停、改;1851個非作戰部隊營區在營房維修、供水供電 、綠化清潔等項目上實施了社會化保障;採取整體移交、委託管理、自謀職業、解除勞動關係等多種方式,分流安置職工和臨時工31,000多人。
2003年全軍招標採購突破70億元,比上年平均節省10%以上。 軍以下部隊採購制度改革普及推開,集中採購超過10億元,實現經濟、社會效益雙豐收。
2003年首次推行總部事業部行政消耗性開支限額標準,戰備、訓練等重點項目得以有效保障。 2003年上半年,通過此制度壓縮總部事業經費中行政消耗性開支2000多萬元。
全軍上下關注的住房制度改革穩步推進。 2003年總部推出了關於加強經濟適用住房管理、加速售房區現有住房出售和部分離休老幹部住房出售有關政策,現有住房政策基本完善配套。 2003年軍委投資9.5億元建設士官家屬臨時來隊住房,截至2003年,這項工作已取得階段性成果。
擔負醫改試點任務的瀋陽、蘭州、濟南軍區實現了醫改試點的預期目標,在門診、住院經費的消耗上,比醫改前上升了10.5%,住院人均消耗比醫改前上升4.1%,用藥從數量品種 到檔次都有了較大提高;建立了大病醫療統籌補助標準,醫改工作初見成效。
後勤資訊化建設穩步推進。 在已經建立20個全軍衛星遠距醫療系統站點的基礎上,2003年又為駐邊遠艱苦地區部隊新建60多個站點,在全軍基本形成了遠距醫療規模體系。 《軍隊住房建設與管理資訊系統》使全軍住房管理有了質的飛躍。 全軍規模最大的軍需自動化立體庫在總後軍需供應局正式投入使用,標誌著全軍軍需物資供應步入自動化。
住房制度日趨完善
經過多年的探索和不斷深化,全軍住房制度改革取得了重大進展,住房制度日趨完善,住房保障新體系逐步形成。 全軍住房保障攤子大、出口不暢,軍人薪資中住房部分含量低、買不起房、買不到房等問題,逐漸解決。
一、明確了各類人員的住房保障方式。 對在職幹部、離休幹部、退休幹部、轉業幹部及士官、職工等6類人員,分別實施不同的住房保障。 在職幹部主要住公寓房,有條件的可以購買自有住房;離休幹部主要購買乾休所現有住房,退休幹部主要購買專門為其建設的經濟適用住房,也可以自理住房;轉業、復員幹部和 士官由軍隊發給相應的住房補貼後購買社會提供的住房;職工按屬地原則實施房改。
二、建立了住房補貼和公積金制度。 各類人員按月計算住房補貼,計入個人的帳戶,經批准購買住房或退休、轉業離開部隊時發給個人。 在工資總額中提取部分經費用於建立住房公積金,個人所有、統一存儲、專項使用。
三、實施劃區售屋及發展經濟適用住宅。 部隊家屬生活區劃分為公寓區及售房區。 公寓區住房保障在職人員住用,離職遷出。 售房區住房向個人出售,產權歸己,維修自理。 軍事單位利用國家經濟適用住宅政策,在售屋區或徵用地方的土地建設經濟適用住宅向軍隊人員出售。
四、住房管理實行社會化。 壓縮住房保障規模,減輕軍隊管房負擔,售房區出售的住房、新建的經濟適用住房全部實行物業管理,公寓區住房的管理逐步向社會化管理過渡。
基層幹部住宅建設明顯加快
為了改善旅團作戰部隊、特別是駐鄉鎮和邊遠艱苦地區的旅團作戰部隊幹部的住房條件,軍委、總部多次撥出專項經費,著手安排住房建設和改造。 各級各部門依據總部製定的建設規劃,優先解決駐鄉鎮和邊遠艱苦地區旅團作戰部隊幹部住房問題,並針對幹部流動性大,能進能出,人走家搬等特點,因地制宜,通過缺 房屋新建、危險房屋完工、舊房整修和補缺配套等多種方式,加速進度,擴大受益面。 同時,加強以限額設計為主要內容的勘察設計管理,嚴格施工管理,確保新建、翻建和整修的房屋經濟實用,工程品質優良。 截至2003年底,全軍已累計投資17億多元,新建改造房屋300多萬平方米,使5萬多名旅團部隊的幹部住上了新房。 全軍士官家屬臨時來隊住房建設已完成投資3.5億元,建成士官家屬臨時來隊住房1.4萬套、56萬平方米,使10萬名士官家屬臨時來隊有房可住。
軍人配偶隨軍未就業期間可享有基本生活補貼
新推出的《軍人配偶隨軍未就業期間社會保險暫行辦法》明確規定,軍人配偶隨軍未就業期間可享有基本生活補貼。 《辦法》規定,根據軍人駐地艱苦程度,軍人配偶隨軍未就業期間每月享有相應的基本生活補貼。 同時,為促進就業、再就業,實施領取基本生活補貼遞減制度。 駐國家確定的一、二類艱苦邊遠地區和軍隊確定的三類島嶼部隊的軍人,其配偶隨軍未就業期間領取基本生活補貼標準全額的期限最長為60個月;駐一般地區部隊的軍人 ,其配偶隨軍未就業期間領取基本生活補貼標準全額的期限最長為36個月。 未就業隨軍配偶領取基本生活補貼標準全額期滿後,以本人基本生活補貼標準8%的比例逐年遞減。 遞減後的最低基本生活補貼標準,由總後勤部參考省會城市失業保險金標準決定。 駐國家確定的三四類艱苦邊遠地區和軍隊確定的特、一、二類島嶼部隊的軍人,其配偶隨軍未就業期間基本生活補貼標準不實行遞減。
全軍99%以上的醫院實現資訊化管理
根據解放軍總後勤部相關部門介紹,至2003年底,除駐西藏等偏遠地區的4所軍隊醫院外,全軍99%以上的醫院已實現資訊化管理,取得了顯著的效益。
全軍醫院資訊系統擁有上網微電腦2.6萬台,已經建立了11個資訊化基地。 2003年部分大軍區已實現軍區機關到醫院的聯網,全軍將逐步實現醫院資訊系統的聯網,總部機關可透過廣域網路直接了解全軍醫院的醫療、教學、科研等情況,為宏觀決策提供科學依據 。 醫院資訊系統增強了醫院管理環節的調控力度,實現了全程管理;簡化了工作流程,方便了病患就醫;提高了醫療質量,減少了醫護差錯。 依托醫院資訊系統軍隊在瀋陽軍區、濟南軍區、蘭州軍區進行了醫療改革試點,130多萬官兵和家屬實現持「醫療卡」就醫,減少了就診、轉診程序。 明年4月1日,全軍將實施持卡就醫。 醫院資訊系統在合理用藥、電子醫療檔案和醫學影像應用方面也取得了顯著成效。 門診處方和住院病人用藥醫囑不合理,醫院資訊系統會自動顯示出來,並為病人提供最佳用藥選擇,避免了亂開大處方現象;電子醫療檔案規範了病程記錄的書寫;醫學影像資料的計算機 採集、存貯和調閱,為提高工作效率和醫療品質提供了方便。
首次派遣高級專家團赴駐邊遠艱苦地區部隊
解放軍總後勤部高級專家團於8月11日抵達青海省西寧市,開始為駐邊遠艱苦地區的青藏兵站部基層部隊進行技術服務。 這是全軍首次組織面向駐邊遠艱苦地區基層部隊的智力服務活動。 參與這次智力服務活動的專家團成員由總後勤部所屬醫療單位、軍事院校、科研單位的中青年專家、教授組成,其中有1名院士、8名博士、2名碩士。 他們中既有在海外學成歸來的專家,又有全國、全軍先進典型和總後勤部「三星」人才。 專家團將根據部隊實際需要,深入青藏線沿線兵站、醫院、倉庫、輸油管部隊、汽車運輸部隊,透過舉辦學術講座、設備檢修、醫療服務、心理諮詢等方式對官兵們實行面對面服務,幫助解決部隊遇到的技術難題,指導開展新技術、新業務,傳授 基層所需的有關業務知識等。 專家團向部隊贈送了價值140多萬元的醫療設備。
武器裝備
解放軍總裝備部領導同志在談到2003年部隊武器裝備現代化建設時強調,要切實把「三個代表」重要思想作為各項工作的科學指南,作為推動部隊裝備建設跨越式發展的根本動力。 深入研究面臨的新情況、新問題,積極推動適應武器裝備發展的理論創新;大力推進科技創新,在「生產一代、研發世代、預研一代」的基礎上,著力進行「探索一代」的研究; 穩步推進體制、機制創新。 要適應世界新軍事變革的大趨勢,努力尋求武器裝備建設的新突破新跨越。 要適應高新技術武器裝備發展的要求,確保重大科學研究試驗任務圓滿完成。 要服從並服務國家發展大局,為全面建立小康社會積極作貢獻。
解放軍總裝備部把選拔培養高學歷優秀年輕幹部作為實施人才戰略工程的一項重要內容來抓,截至2003年底有400多名博士、碩士走上團以上領導崗位,其中150多人擔任軍師級領導 職務。 高學歷年輕幹部在總裝備部師團兩級已成為主體,團以上領導班子中具有大學本科以上學歷的約佔90%,基本形成了更替有序、人才輩出的良好局面,從而為部隊武器裝備 現代化建設的長遠發展提供了組織保證。
總裝備部擔負部隊武器裝備建設和國防科研試驗重大任務。 為適應武器裝備建設長遠發展需要和進一步提高國防科研試驗能力,在總裝備部黨委的統一部署下,各級把選拔培養學歷高、素質好、發展潛力大的優秀年輕幹部作為一項長期而緊迫 的任務來抓,採取使用一批、培養一批、儲備一批的辦法,把高學歷優秀年輕幹部有序地充實到團以上領導崗位,逐步實現軍師級指揮軍官隊伍年輕化、知識化、專業 化。 至2003年,已培養了一批「博士司令」「博士老總」「博士校長」。 在選拔培養高學歷優秀年輕幹部過程中,總裝備部各級不搞論資排輩,而是強調“優先意識”和“超前意識”,把一批高學歷優秀年輕幹部提前安排到重要領導崗位上任職, 成為重點裝備研發、重大科學研究試驗任務和國防關鍵技術攻關的組織指揮者。 對特別優秀的高學歷年輕幹部,採取小步快走等超常措施破格提拔,近年來提拔的一批年輕軍職領導幹部中,博士和碩士佔一半以上。
解放軍總裝備部認真依照國務院、中央軍委所授予的職能,加強對軍隊和國防科技工業部門國防科研經費的審計監督和管理,努力提高國防科研經費的使用效益,有效保證了新型裝備和重大國防科研試驗 任務的完成。
根據總裝備部審計局負責人介紹,國防科研財務和審計部門採取多種措施,嚴格國防科研經費的管理和審計,使得國防科研經費的使用效益進一步提高;國防科研經費保障力度明顯加強,管理程序 更規範,經費流向更合理;國防科研合約制度進一步推廣和深化,大大促進和保障了重大科研試驗任務的順利完成;加大了國防科研經費的審計監督力度,嚴肅查處了一批違反國防科研經費 使用管理規定的單位和個人,有效確保了國防科研經費的專款專用。 經對26項國防重點工程和各軍工集團公司部分科研單位國防科研經費使用情況的審計表明,軍隊和國防科技工業部門國防科研經費使用情況良好,管理規範,財務核算體系完整,有效地保證了國防 科學研究的需要和新型裝備的研發。 一批新型武器裝備的研發工作取得重大進展,一批關鍵國防科技攻關計畫取得重要突破,國防研究與試驗產品的品質明顯提高,部分重點國防研究計畫的進度提前。
2003年8月,解放軍總裝備部採用競爭性談判方式,分別與3家車輛製造廠簽訂了航太發射推進劑鐵路車輛的採購合約。 這標誌著軍隊裝備採購制度改革正逐步深入。
航太發射推進劑鐵路車輛分罐車、機車、客車等不同類型,過去都是到指定廠商訂購,車輛造價不斷上漲,產品技術性能、可靠性和售後服務卻沒有明顯改善。 為貫徹落實《裝備採購條例》,深化裝備採購制度改革,總裝備部在車輛訂購中引入競爭機制,根據推進劑運輸車輛的技術特點和鐵路車輛製造業實際,首次採用競爭性談判方式選擇承製 廠商。 談判過程中,裝備部遵循「公平、公正、科學、擇優」的原則,從報價、品質、服務、資信等方面對參與競爭性談判的廠商進行了綜合評定。 最終,3個報價最低、方案最優的車輛廠成為預成交廠商。 這次採購比預算少支出了132萬元。
To meet the challenges of the world's new military transformation and actively promote military transformation with Chinese characteristics, the Central Military Commission has made major strategic decisions and the headquarters has launched a series of major measures. The biggest move is the decision to reduce the number of military personnel by another 200,000 before 2005.
In 2002, the Central Military Commission officially promulgated the "Implementation of Military Talent Strategic Project Plan"; the four headquarters successively issued "Regulations on Several Issues on Strengthening the Construction of Cadre Teams for Equipment and Technical Support of Combat Forces" and "Opinions on Further Improving Cadre Exchanges" and the "Opinions on Several Issues Concerning Improving the Quality of Staff Teams", the pace of personnel training across the military has been significantly accelerated. In October 2002, a high-tech knowledge training class for senior military region leaders started, focusing on the study of information warfare and military information construction. Each headquarters agency has also successively launched high-tech knowledge training courses. The focus on informatization construction starts from senior cadres and leading agencies, demonstrating the focus and characteristics of military reforms over the past year.
The major measures taken by the Central Military Commission Headquarters directly enhance combat effectiveness. When deploying annual training tasks, the General Staff Headquarters emphasizes innovative forward-looking combat theories and drives the reform of training content and training methods with new needs. The General Political Department directly organized the revision of the new "Political Work Regulations", emphasizing that political work should serve the promotion of military reform with Chinese characteristics, and all military political cadres began to study the new "Political Work Regulations" on a large scale. The General Logistics Department has vigorously promoted the construction of tri-service joint logistics and logistics informatization, and information systems such as telemedicine for remote troops and military housing management have made new leaps. Equipment system officers and soldiers seize the period of strategic opportunities, accelerate the leap-forward development of military weapons and equipment, and strive to make existing equipment, especially new equipment, into an organic system and into a system to form combat capabilities and support capabilities.
Improving the quality of officers and soldiers is an important part of promoting military reform with Chinese characteristics. To adapt to building an information-based army and win information-based wars, we must have high qualities that are suitable for it. By 2003, both grassroots officers and soldiers, division chiefs, and low-educated cadres had a strong sense of crisis. Many leading cadres have taken the lead in setting an example and are determined to improve their ability to command information warfare. All units across the military have taken increasingly strong measures to focus on talent work, providing strong talent and intellectual support for promoting military reform with Chinese characteristics.
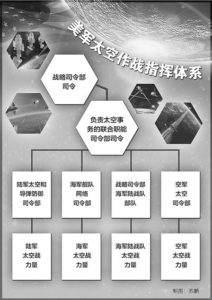
Disarmament by 200,000
On September 1, 2003, when attending the 50th anniversary celebration of the University of Defense Technology, Jiang Zemin, Chairman of the Central Military Commission, solemnly announced that the Party Central Committee and the Central Military Commission decided to reduce the number of military personnel by 500,000 during the "Ninth Five-Year Plan" period. The former army will cut another 200,000 positions. This is the 10th major reorganization of the military since the founding of the People's Republic of China, which has attracted great attention from the international community. Some public opinion said, "With the large-scale reduction of military personnel as a symbol, the curtain of China's new military reform has officially begun."
To promote military reform with Chinese characteristics, we must scientifically establish strategic goals, development ideas and specific steps for military construction in accordance with the requirements for realizing informatization. However, insufficient supply of military expenditures is a common problem encountered by the militaries of various countries, including China, in the new military transformation. From a global perspective, the proportion of national defense expenditures in GDP in various countries is generally between 2% and 4%, while China only accounts for about 1.5%. Taking 2002 as an example, China's defense expenditure was 169.444 billion yuan, equivalent to approximately 20 billion U.S. dollars, which was only equivalent to about 6% of that of the United States. Most of the military expenditure is used for the living expenses and activity maintenance expenses of the 2.5 million personnel, and relatively little is used for equipment and training.
Military experts pointed out that the purchase and maintenance costs of high-tech and information-based weapons and equipment have increased exponentially. To solve the contradiction between supply and demand of military expenditure and maximize benefits from limited military expenditure, the best idea is to reduce the number of personnel and improve the quality of the army. The new military reform requires that the size of the army be reasonable, moderate and sufficient. After the number of Chinese military personnel is reduced from 2.5 million to 2.3 million, it will be more likely that limited strategic resources can be used more effectively and achieve greater benefits. Large-scale reduction of posts is not just about "reducing personnel". Its essence is a structural adjustment of the existing military system and establishment. The adjustment and reform of the military system and establishment must implement the principles of elite troops, integration and efficiency. Only by in-depth study of the impact of high-tech warfare on the military system and establishment Only by focusing on solving the contradictions and problems existing in the leadership, command and management system and troop formation can we establish a military system with Chinese characteristics.
Military experts believe that reducing quantity, improving quality, optimizing the internal structure of the army, increasing high-tech content, strengthening comprehensive integration construction, and gradually establishing systems and establishments that meet the requirements of modern warfare are the key to accelerating the modernization of the People's Liberation Army and better doing military work. The inevitable choice for struggle preparation. Unswervingly following the path of elite soldiers with Chinese characteristics is the established policy of military construction. The reduction of military personnel is to continuously adapt to the world's new military reform and development trends and to serve the needs of the overall national economic construction. After this disarmament, although the scale of China's military power has been reduced to a certain extent, its combat effectiveness will definitely be improved, and its ability to safeguard national sovereignty and territorial integrity will definitely be further enhanced!
According to the unified deployment of the Central Military Commission, the work of streamlining and reorganizing the army will be fully launched by the end of 2003. Most of the remaining soldiers in the streamlined and reorganized units will be arranged to retire from active service, including remaining conscripts and non-commissioned officers who have not completed their service period. The People's Liberation Army Headquarters has made specific arrangements for this work: in accordance with the needs of troop adjustment and downsizing, some conscripts and non-commissioned officers who have not served for the required period of time are allowed to retire from active service early; retired conscripts and demobilized non-commissioned officers in units with heavier missions can be arranged to retire early. Demobilized non-commissioned officers who leave the unit; demobilized non-commissioned officers from units that have been abolished or reorganized into reserve units shall be transferred to local resettlement departments for placement in advance. The resettlement of soldiers who retire early due to the adjustment and streamlining of the army must be treated equally with retired soldiers who have completed their service, be received on time, and included in the 2004 resettlement plan. Among them, retired urban conscripts who have served in active service for more than one year must be placed in accordance with the relevant regulations for retired conscripts after completing their service; retired non-commissioned officers who have served in active service for more than 9 years must be arranged in accordance with the relevant regulations for retired non-commissioned officers who have served in active service for more than 10 years. . For demobilized non-commissioned officers who leave early from units that have been abolished or reorganized into reserve forces, each major unit will send dedicated personnel to submit the files to the relevant local resettlement departments for review. For those who meet the conditions, a "Notice of Acceptance and Placement" will be issued, and the army can organize demobilized non-commissioned officers. Leave the team; if you personally request demobilization, you can also undergo demobilization and resettlement with approval. For noncommissioned officers who meet the retirement conditions, retirement orders should be issued in a timely manner in accordance with the "Measures for the Resettlement of Noncommissioned Officers of the Chinese People's Liberation Army Retiring from Active Service" issued by the State Council and the Central Military Commission, and reported to each level for inclusion in the transfer and resettlement plan. Soldiers who retire early will be issued retirement fees and materials based on their actual service years and corresponding standards. The funds and materials issued must be distributed to retired soldiers in full and in a timely manner. Decommissioned non-commissioned officers who leave the team early will be treated the same as decommissioned non-commissioned officers who leave the team during the normal time of the year. Salaries, benefits, medical treatment and clothing will be paid in accordance with relevant regulations.
After the adjustment and reform of the military's organizational structure, the Chinese military will have dozens of cadre positions, including chiefs of departments and club directors, and tens of thousands of cadre positions filled by non-commissioned officers. Personnel in professional positions changed to non-commissioned officers will be included in the training of technical secondary school or above in military academies starting from 2004. In order to ensure the smooth progress of this work and meet the requirements for talents and other positions to be replaced by the end of 2003, pre-service training for non-commissioned officers is planned to be conducted by combining technical secondary school education training with short-term training. Among them, short-term training of 3 to 5 months will be conducted for professional positions in which replacement candidates are selected from existing non-commissioned officers who have received more than 2 years of training in colleges and universities. For professional positions that do not have the same or similar majors in the existing non-commissioned officer education training plan and for which there are no candidates for replacement, we will organize technical secondary school education training, with a 2-year academic system, 1 year of study at school, and 1 year of on-the-job internship; enrollment will begin in the first quarter of each year , he continued his summer vacation while studying at school, and returned to the army for internship before the end of 2003.
Attached: Information on the first nine disarmaments
The first streamlining and reorganization: In the early days of the founding of New China, the total strength of the People's Liberation Army reached 5.5 million. In June 1950, the Chinese Army Staff Conference's streamlining and reorganization plan stipulated that the army should be reduced to 4 million, and more than 239,000 people were demobilized that year. Soon, the War to Resist US Aggression and Aid Korea broke out, and the streamlining and reorganization work was terminated. By the end of 1951, the number of military personnel reached 6.27 million, the largest number in the history of the Chinese military.
The second streamlining and reorganization: In November 1951, the Central Military Commission held a reorganization meeting and stipulated that the total number of military personnel should be controlled at about 3 million by 1954. In January 1952, Mao Zedong approved the "Military Reorganization Plan" and the total quota of the army was reduced to about 3 million.
The third streamlining and reorganization: As of the end of September 1953, the number of troops was reduced to about 4.2 million. In December of that year, a meeting of senior party cadres in the Chinese military system decided to reduce the number of troops to 3.5 million. By June 1954, the army had been streamlined by more than 472,000 people, and the plan was basically completed by the end of the year.
The fourth streamlining and reorganization: In January 1957, the enlarged meeting of the Central Military Commission passed the "Decision on Reducing the Quantity and Strengthening the Quality of the Army", which determined that the total number of the army would be reduced by another third, requiring a reduction of 1.3 million personnel in three years, reducing it to Around 2.5 million people.
The fifth streamlining and reorganization: From June 24 to July 5, 1975, the enlarged meeting of the Central Military Commission decided to reduce the army by 600,000 people within three years. By 1976, the total number of troops was 13.6% lower than in 1975. Later, due to the interference and sabotage of the "Gang of Four", the streamlining and reorganization task was stopped before it was completed.
The sixth, seventh, and eighth streamlining and reorganization: In March 1980, the Central Military Commission decided to streamline the army again, vigorously streamline agencies, reduce non-combatants and support troops, implement streamlined reorganization of some units, and transfer some units to local governments. On August 15 of the same year, the Central Committee of the Communist Party of China approved the Central Military Commission's "Plan on the Streamlining and Reorganization of the Army." In September 1982, the Central Committee of the Communist Party of China and the Central Military Commission decided to further streamline and reorganize the army. At the end of May and beginning of June 1985, the Central Military Commission decided to reduce the number of military personnel by 1 million, and the streamlining and reorganization work was basically completed by the beginning of 1987.
The ninth streamlining and reorganization: In September 1997, Comrade Jiang Zemin announced in his report to the 15th National Congress of the Communist Party of China that, based on the reduction of 1 million military personnel in the 1980s, China will reduce the military personnel by another 500,000 personnel in the next three years. By the end of 1999, the task of disarmament of 500,000 troops had been completed, and more than 200,000 military cadres had retired from active service and transferred to local jobs. This is the highest proportion of cadre reduction among the previous reductions in military personnel in New China.
Technological training
In 2003, the Chinese military and armed police forces successfully completed their annual training tasks and achieved new results in five aspects: theoretical innovation, actual combat drills, anti-terrorism training, talent training, and strict management training.
1. Use developed military theories to guide new military training practices. In accordance with the requirements of using informatization to drive mechanization and mechanization to promote informatization, the military training of the army and armed police forces conducts in-depth theoretical research on information operations, non-contact operations, joint operations and other combat styles, innovates military theories and combat ideas, and guides military training. The deepening of reform has promoted the development of scientific and technological training in the direction of informatization.
2. Focus on improving the ability to win, taking preparations for military struggles as the leader, and making troop training close to actual combat. The Nanjing and Guangzhou Military Regions have intensified their efforts in practical training with actual troops, carried out research on difficult tactical and technical issues, and achieved a number of valuable results. The Shenyang, Beijing, and Jinan Military Regions practice command, tactics, coordination, and support under conditions similar to actual combat; the Navy, Air Force, and Second Artillery Force focus on strengthening joint combat command drills of all services and arms; Lanzhou and Chengdu Military Regions deepen operations in alpine mountains Conduct drills to study and solve key issues such as mobility, survival, command, coordination, and support; the Armed Police Force strengthens emergency response, anti-terrorism, and defense operations drills. The entire military actively carries out innovative practices in regional collaborative training, and launches key research on key issues such as joint tactical corps operational theory and regional collaborative training mechanisms.
3. In accordance with the new military tasks assigned to the army by the state in the fight against terrorism, the troops responsible for the task of counter-terrorism shall carry out solid research and training practices in the military fight against terrorism.
4. There are new measures for talent cultivation. Military academies focus on cultivating high-quality new military talents, deepening the adjustment and reform of the institutional structure of institutions, and promoting the in-depth development of teaching reforms in institutions. All units have further intensified the construction of training institutions and teaching reform, and trained a large number of outstanding command non-commissioned officers at the grassroots level.
5. The military insists on conducting training in accordance with the law, conducts training strictly according to the program, vigorously carries out on-the-job training activities, improves the quality of contract tactical drills, and continuously improves the level of formalized training of the troops.
Force reform
On June 10, 2003, the General Political Department of the People's Liberation Army issued a notice requiring officers and soldiers of the entire army and the Armed Police Force to conscientiously study and implement the spirit of the "Notice of the Central Committee of the Communist Party of China on Issuing the (Study Outline of the Important Thought of the "Three Represents")" and deepen the understanding of the "Three Represents" The understanding of the important thought of "Three Represents" has led to a new upsurge in studying and implementing the important thought of "Three Represents" in the entire army. The General Political Department organized the publishing department to quickly print and distribute the "Outline for Studying the Important Thought of "Three Represents"" to the entire army, and issued a special notice requiring all leading cadres at the army corps level and above and cadres in government agencies to carefully study a series of important works by Comrade Jiang Zemin and learn from the "Outline" "As a clue, we can deeply and systematically study and master the important thinking of the "Three Represents" as a whole. The grassroots level should use the "Outline" as the main guidance material, read several important works of Comrade Jiang Zemin, deeply study and master the basic spirit and basic viewpoints of the important thought of "Three Represents", and further unify the thoughts and actions of all officers and soldiers with Deng Xiaoping Theory and uphold the important thought of "Three Represents", further condense wisdom and strength into realizing the tasks set by the 16th National Congress of the Communist Party of China, resolutely obey the commands of the Party Central Committee, the Central Military Commission and Chairman Jiang, and strive to achieve the grand goal of building a moderately prosperous society in an all-round way. Goal and strive for the revolutionization, modernization and regularization of the army.
On June 18, a theoretical seminar for the whole army to study and implement the important thought of "Three Represents" was held in Beijing. The meeting emphasized that we must more firmly establish the guiding position of the important thought of "Three Represents" in military building, gather the will and strength of the officers and soldiers under the banner of the important thought of "Three Represents", and further lay a solid foundation for adhering to the Party's support for the military. The ideological and theoretical foundation of absolute leadership enables the entire military to always maintain a mental state of advancing with the times, shoulder the sacred mission, actively promote military reform with Chinese characteristics, and achieve leap-forward development of military modernization.
In mid-June, with the approval of the Central Military Commission, the General Political Department of the People's Liberation Army put forward opinions on conscientiously implementing the spirit of the notice of the CPC Central Committee and setting off a new upsurge in studying and implementing the important thought of "Three Represents" throughout the army.
With the approval of the Central Military Commission, the General Political Department entrusted the National Defense University to hold two rotational training courses for leading cadres above the military level in late August and mid-September to study and implement the important thinking of the "Three Represents". Recent students from the entire army and the Armed Police Force Hundreds of leading cadres above the military level each conducted a 10-day study. The rotation training class is guided by the spirit of Comrade Hu Jintao's "July 1st" important speech, in accordance with the requirements of the Central Committee's "Notice" and the General Administration's "Opinions", and based on the "Study Outline of the Important Thought of "Three Represents"" and "Jiang Zemin's Thought on National Defense and Army Construction" "Outline" as the basic clue, organized students to study Comrade Jiang Zemin's works and the report of the 16th National Congress of the Communist Party of China. In order to deepen the deep understanding and systematic grasp of the content learned, and to understand the latest theoretical research results, the rotation training class also invited relevant members of the Central Propaganda Group, the Central Literature Research Office, the National Development and Reform Commission, Peking University, and the Military Ideological and Theoretical Front. Experts and scholars gave special lectures and counseling reports. Through rotation training, the trainees have a new understanding of the historical background, practical basis, scientific connotation, spiritual essence and historical status of the important thought of "Three Represents", further deepened their understanding of Jiang Zemin's thoughts on national defense and army construction, and enhanced They have a sense of mission and responsibility to use the important thinking of "Three Represents" to guide the reform and construction of the army and create new situations in all work.
In 2003, the entire army and armed police forces carried out extensive and in-depth educational activities to study and practice the important thought of "Three Represents" and contribute to the comprehensive construction of a well-off society. Through education, the majority of officers and soldiers have further strengthened their political belief in the party's innovative theory, and enhanced their sense of responsibility and mission to consciously apply the important thought of "Three Represents" to promote the reform and construction of the army and contribute to the comprehensive construction of a moderately prosperous society.
According to the person in charge of the relevant department of the General Political Department of the People's Liberation Army, the educational activities are implemented in two stages. In the first half of the year, the focus is on studying the report of the 16th National Congress of the Communist Party of China and focusing on special education; in the second half of the year, the implementation of General Secretary Hu Jintao's instructions for leading cadres at the provincial and ministerial levels Study and implement the important speeches at the special seminar on the important thought of "Three Represents" and the deployment of the Party Central Committee and the Central Military Commission, combined with the study of Jiang Zemin's thoughts on national defense and army building, to further deepen educational activities. In education, the main leaders of major units went deep into the troops to provide specific guidance, and nearly a thousand leaders above the military level and more than 10,000 cadres above the regiment level gave lectures to the troops. Many troops invited local party and government leaders to introduce measures to develop the economy and improve people's lives; they organized viewings of video reports on the deeds of advanced people such as Zheng Peimin and Fan Kuangfu; they organized visits to anti-SARS photo exhibitions and invited anti-SARS heroes and models to give reports; and held situation report meetings with experts and scholars. Discussions and exchanges, etc. The officers and soldiers said that in the great journey of socialism with Chinese characteristics, we cannot do without the guidance of the important thought of "Three Represents" for a moment, and we must always persist and unswervingly.
All units guide officers and soldiers to use the positions, viewpoints and methods of the important thought of "Three Represents" to deeply understand the party's major strategic decisions for the comprehensive progress of the country's economy, society and culture, and encourage everyone to take realizing the great rejuvenation of the Chinese nation as their own responsibility and consciously obey and serve The overall situation of building a moderately prosperous society in an all-round way. The military medical staff who participated in the fight against SARS at Xiaotangshan Hospital worked hard for more than 50 days and nights and made outstanding achievements in defeating the SARS disease. After floods occurred in the Yellow River, Huaihe, Weihe and other river basins, earthquakes occurred in Xinjiang, Yunnan and other places, and fires broke out in the Greater Khingan Mountains and other areas, more than 100,000 officers and soldiers risked their lives and rushed to the front line of rescue and disaster relief, assisting local governments to relocate and resettle more than 100 people. Thousands of people, transported more than 2 million tons of supplies, and defended the achievements of "moderately prosperous" construction with their blood and lives.
The most distinctive feature of this educational activity is to focus on transforming learning results into powerful spiritual motivation to promote army building, achieve new development, and create new situations. Many troops guide officers and soldiers to find out the manifestations of outdated thinking in training and teaching, education management, logistics support, equipment construction, etc., correct them one by one, and establish training, management and management systems that are suitable for building a well-off society in an all-round way and building an information-based army. Talent concept. Each unit actively organized officers and soldiers to boldly reform and innovate based on actual combat needs, and developed a number of new achievements such as field command and control systems, wartime work decision-making systems, and simulation training equipment. The troops responsible for emergency mobile operations shouted the slogan of "training scientific and technological elite soldiers to serve as vanguards", practicing skills and improving quality, and successfully completed tasks such as sea training, field training and live ammunition launches. In 2003, more than 120,000 officers and soldiers in the army actively signed up to participate in various correspondence studies and self-study examinations. Thousands of cadres studied for master's and doctoral degrees in military majors. The Central Military Commission's decision on the implementation of the talent strategic project is becoming practical actions for the majority of officers and soldiers. .
At the end of July 2003, with the approval of the Central Military Commission, the "Jiang Zemin Ideological Study Outline for National Defense and Army Construction" organized and compiled by the General Political Department was officially published and distributed to the entire army. The Central Military Commission issued a notice requiring all officers and soldiers to use Jiang Zemin's "On National Defense and Army Construction" and a series of important speeches as the basic teaching materials, and the "Outline" as important auxiliary materials, conscientiously study and implement Jiang Zemin's thoughts on national defense and army construction, and promote the study of the entire army The new upsurge in implementing the important thought of "Three Represents" continues to develop in depth.
The Central Military Commission held a symposium on the publication of "Jiang Zemin's Ideological Study Outline for National Defense and Army Construction" in Beijing on July 31. The meeting pointed out that Chairman Jiang has formed a complete and systematic thought on national defense and army building in the great practice of leading national defense and army building. Jiang Zemin's thought on national defense and army building, together with Mao Zedong's military thought and Deng Xiaoping's thought on army building in the new era, is a military science system that is in the same vein and keeps pace with the times. It is an important part of the important thought of "Three Represents" and an important part of Marxist military theory. The latest achievements of China's development are scientific guides for military construction and development in the new century and new stage. The entire military must unswervingly regard Jiang Zemin's thoughts on national defense and army building as the fundamental guideline and guide to action in guiding all work. Leading cadres at all levels should set an example in learning and implementing Jiang Zemin's thoughts on national defense and army building, and take the lead in learning, implementing and applying this scientific theory well.
Logistics support
The army's logistics work adheres to the important thinking of "Three Represents" to govern all constructions. In accordance with the requirements of actively promoting military reform with Chinese characteristics, it intensifies reform and innovation, accelerates the pace of development, and achieves remarkable results in logistics construction.
The joint logistics system of the three armed forces is operating well. By adjusting the support relationship, most troops have achieved close-by support; high-quality joint logistics services have been carried out to ensure the timely and full supply of funds and materials; a coordination and cooperation mechanism has been established to provide joint training in peacetime and joint operations in wartime. Guarantee creates conditions.
With the full launch of a new round of socialization of logistics support, 2,179 canteens in the army were reformed in 2003; 1,283 military service agencies were withdrawn, merged, suspended, or modified; and 1,851 non-combat military camps were undergoing barrack maintenance, water supply and power supply. , greening and cleaning projects, etc.; through various methods such as overall transfer, entrusted management, self-employment, and termination of labor relations, more than 31,000 employees and temporary workers were diverted and resettled.
In 2003, the total military bidding and procurement exceeded 7 billion yuan, an average saving of more than 10% over the previous year. The reform of the procurement system for troops below the military level has been popularized and centralized procurement has exceeded 1 billion yuan, achieving both economic and social benefits.
In 2003, the administrative consumable expenditure limit standards for headquarters business departments were implemented for the first time, and key projects such as combat readiness and training were effectively guaranteed. In the first half of 2003, more than 20 million yuan in administrative consumable expenses in the headquarters business funds were reduced through this system.
The reform of the housing system, which the whole military is concerned about, is advancing steadily. In 2003, the headquarters issued relevant policies on strengthening the management of affordable housing, accelerating the sale of existing housing in the housing sales area and the housing sales of some retired veteran cadres. The existing housing policies have basically completed the supporting facilities. In 2003, the Military Commission invested 950 million yuan in building temporary housing for the families of non-commissioned officers. As of 2003, this work has achieved initial results.
The Shenyang, Lanzhou, and Jinan Military Regions, which are responsible for the medical reform pilot tasks, have achieved the expected goals of the medical reform pilot. The consumption of outpatient and inpatient funds has increased by 10.5% compared with before the medical reform. The per capita consumption of inpatients has increased by 4.1% compared with before the medical reform. The number of drugs has increased from quantity to variety. The level of medical care has been greatly improved; the standards for collective subsidy for serious illness medical care have been established, and the medical reform work has initially achieved results.
Logistics informatization construction is advancing steadily. On the basis of the 20 military-wide satellite telemedicine system sites that have been established, more than 60 new sites were built in 2003 for troops stationed in remote and difficult areas, basically forming a large-scale telemedicine system throughout the military. The "Military Housing Construction and Management Information System" has made a qualitative leap in the housing management of the entire military. The largest automated three-dimensional warehouse for military supplies in the entire army was officially put into use at the Military Supply Bureau of the General Logistics, marking the entry into automation of the military supply of military supplies.
The housing system is improving day by day
After years of exploration and continuous deepening, the military's housing system reform has made significant progress. The housing system has been increasingly improved, and a new housing security system has gradually taken shape. The military's housing security market is large, exports are not smooth, and the housing component of soldiers' wages is low, so they cannot afford to buy a house. These problems are being gradually solved.
1. Clarify the housing security methods for various types of personnel. Different housing guarantees are implemented for six categories of personnel, including serving cadres, retired cadres, retired cadres, transferred cadres, non-commissioned officers, and employees. Serving cadres mainly live in apartments, and they can buy their own houses if conditions permit; retired cadres mainly buy existing houses in cadres' residences, and retired cadres mainly buy affordable housing specially built for them, and they can also take care of their own houses; transferred and demobilized cadres and Non-commissioned officers purchase housing provided by society after receiving corresponding housing subsidies from the military; employees implement housing reform based on the territorial principle.
2. Establish a housing subsidy and provident fund system. Housing subsidies for various types of personnel are calculated on a monthly basis and credited to their personal accounts. They will be paid to individuals upon approval to purchase a house or when they retire or change jobs and leave the military. Withdraw part of the funds from the total salary to establish a housing provident fund, which is owned by individuals, stored uniformly, and used exclusively.
3. Implement zoning for housing sales and develop affordable housing. The living area for military family members is divided into apartment areas and sales areas. The housing in the apartment area ensures that employees can live in and move out after resigning. The houses in the sales area are sold to individuals, the property rights belong to them, and the maintenance is taken care of by themselves. Military units take advantage of the national affordable housing policy to build affordable housing on land in housing sales areas or requisitioned areas for sale to military personnel.
4. Socialize housing management. The scale of housing security will be reduced to reduce the burden of housing management by the military. All housing sold in housing sales areas and newly built affordable housing will be subject to property management. The management of housing in apartment areas will gradually transition to socialized management.
Housing construction for grassroots cadres has been significantly accelerated
In order to improve the housing conditions of brigade combat troops, especially those stationed in villages and towns and remote and difficult areas, the Military Commission and the headquarters have allocated special funds on many occasions to start arranging housing construction and renovation. Based on the construction plans formulated by the headquarters, departments at all levels give priority to solving the housing problem of cadres of brigade combat troops stationed in villages and towns and remote and difficult areas. In view of the characteristics of cadres, such as high mobility, being able to come in and out, and people moving around, measures are taken according to local conditions and through the lack of housing. New housing construction, renovation of dilapidated housing, renovation of old housing, and supporting facilities to fill gaps will speed up the progress and expand the scope of benefits. At the same time, we will strengthen survey and design management with quota design as the main content, and strictly implement construction management to ensure that newly built, renovated and renovated housing is economical and practical, and the project quality is excellent. By the end of 2003, the military had invested a total of more than 1.7 billion yuan in building and renovating more than 3 million square meters of housing, enabling more than 50,000 brigade and regiment cadres to live in new homes. An investment of 350 million yuan has been completed in the construction of temporary units for the families of non-commissioned officers in the entire army, and 14,000 temporary housing units covering 560,000 square meters have been built for the families of non-commissioned officers, providing housing for 100,000 temporary units for the families of non-commissioned officers.
Military spouses can enjoy basic living allowances while they are not employed in the military.
The newly issued "Interim Measures for Social Security for Military Spouses While Not Employed in the Military" clearly stipulates that military spouses can enjoy basic living allowances while not employed in the military. The "Measures" stipulate that according to the hardship of the military station, military spouses shall enjoy corresponding basic living allowances every month while they are not employed in the military. At the same time, in order to promote employment and re-employment, a system of declining basic living allowances is implemented. For military personnel stationed in Category I and Category II difficult remote areas determined by the state and Category III island units determined by the military, their spouses can receive the full standard of basic living allowance for up to 60 months while they are not employed in the army; for soldiers stationed in general areas, the maximum period is 60 months. , the maximum period for which the spouse can receive the full standard of basic living allowance while serving in the military and not employed is 36 months. After the full period of the basic living subsidy standard for an unemployed military spouse expires, the rate of 8% of the basic living subsidy standard will be reduced year by year. The reduced minimum basic living allowance standard will be determined by the General Logistics Department with reference to the unemployment insurance standard in provincial capital cities. For servicemen stationed in the third and fourth categories of difficult remote areas determined by the state and the special, first and second category island units determined by the military, the basic living subsidy standards for their spouses will not be reduced during the period when they are not employed in the army.
More than 99% of hospitals across the military have implemented information management
According to relevant departments of the General Logistics Department of the People's Liberation Army, by the end of 2003, with the exception of four military hospitals stationed in remote areas such as Tibet, more than 99% of hospitals in the army had implemented information management and achieved significant benefits.
The military hospital information system has 26,000 Internet-connected computers, and 11 information bases have been established. In 2003, some major military regions have already implemented networking from military region agencies to hospitals. The entire military will gradually implement networking of hospital information systems. Headquarters agencies can directly understand the medical, teaching, scientific research, etc. conditions of all military hospitals through the wide area network, providing scientific basis for macro decision-making. . The hospital information system strengthens the control of hospital management links and realizes full-process management; it simplifies the work process and facilitates patients' medical treatment; it improves the quality of medical care and reduces medical errors. Relying on the hospital information system, the military has carried out medical reform pilots in the Shenyang Military Region, Jinan Military Region, and Lanzhou Military Region. More than 1.3 million officers, soldiers and their family members have been able to seek medical treatment with "medical cards", reducing medical treatment and referral procedures. On April 1 next year, the entire military will implement card-based medical treatment. Hospital information systems have also achieved remarkable results in rational drug use, electronic medical records and medical imaging applications. If outpatient prescriptions and inpatient medication orders are unreasonable, the hospital information system will automatically display them and provide patients with the best medication options, avoiding the phenomenon of random large prescriptions; electronic medical files standardize the writing of disease course records; computers of medical imaging data Collection, storage and retrieval provide convenience for improving work efficiency and medical quality.
For the first time, a high-level expert team was dispatched to troops stationed in remote and difficult areas.
A senior expert team from the General Logistics Department of the People's Liberation Army arrived in Xining City, Qinghai Province on August 11 and began to provide technical services to the grassroots troops of the Qinghai-Tibet Military Station stationed in remote and difficult areas. This is the first time the army has organized an intellectual service activity for grassroots troops stationed in remote and difficult areas. The expert team members participating in this intellectual service activity are composed of young and middle-aged experts and professors from medical units, military academies, and scientific research units affiliated to the General Logistics Department, including 1 academician, 8 doctors, and 2 masters. Among them are experts who have returned from overseas studies, as well as advanced models across the country and the army and "three-star" talents from the General Logistics Department. According to the actual needs of the troops, the expert team will go deep into the military stations, hospitals, warehouses, oil pipeline troops, and automobile transportation troops along the Qinghai-Tibet Line, and provide face-to-face services to the officers and soldiers by holding academic lectures, equipment maintenance, medical services, psychological consultation, etc., to help the officers and soldiers. Solve technical problems encountered by the troops, guide the development of new technologies and new businesses, and impart relevant business knowledge needed by the grassroots. The expert team donated medical equipment worth more than 1.4 million yuan to the troops.
Weaponry
When talking about the modernization of military weapons and equipment in 2003, leading comrades from the General Armament Department of the People's Liberation Army emphasized that the important thinking of "Three Represents" should be effectively used as a scientific guide for all work and as the fundamental driving force for the leap-forward development of military equipment construction. In-depth study of new situations and new problems faced, and actively promote theoretical innovation adapted to the development of weapons and equipment; vigorously promote scientific and technological innovation, on the basis of "production generation, development generation, pre-research generation", focus on "exploration generation" research; Steadily promote institutional and mechanism innovation. We must adapt to the general trend of new military changes in the world and strive to seek new breakthroughs and new leaps in the construction of weapons and equipment. It is necessary to adapt to the requirements of the development of high-tech weapons and equipment and ensure the successful completion of major scientific research and test tasks. We must obey and serve the overall development of the country and actively contribute to building a moderately prosperous society in an all-round way.
The General Armament Department of the People's Liberation Army regards the selection and training of outstanding young cadres with high academic qualifications as an important part of the implementation of the talent strategy project. By the end of 2003, more than 400 doctors and masters had taken leadership positions at or above the regiment level, and more than 150 of them served as military division-level leaders. position. Highly educated young cadres have become the main body at the division and regiment levels of the General Armament Department. About 90% of the leadership teams above the regiment level have a bachelor's degree or above. This has basically formed a good situation of orderly replacement and the emergence of talents, thus providing a good foundation for the army's weapons and equipment. The long-term development of modernization provides organizational guarantee.
The General Armament Department is responsible for the major tasks of military weapons and equipment construction and national defense scientific research and testing. In order to meet the long-term development needs of weapons and equipment construction and further improve national defense scientific research and testing capabilities, under the unified deployment of the Party Committee of the General Armament Department, all levels have regarded the selection and training of outstanding young cadres with high academic qualifications, good quality and great development potential as a long-term and urgent task. To grasp the tasks of the regiment and above, adopt the method of using a group, training a group, and reserving a group, and orderly enrich the outstanding young cadres with high academic qualifications into leadership positions above the regiment, and gradually realize the younger, more knowledgeable and professional team of commanding officers at the military division level. change. By 2003, a group of "Doctoral Commanders", "Doctoral Bosses" and "Doctoral Principals" had been trained. In the process of selecting and training outstanding young cadres with high academic qualifications, all levels of the General Armament Department do not engage in seniority ranking. Instead, they emphasize "priority awareness" and "advanced awareness" and arrange a group of outstanding young cadres with high academic qualifications to serve in important leadership positions in advance. Become the organizer and commander of key equipment development, major scientific research and test tasks, and key national defense technology research. For particularly outstanding young cadres with a high degree of education, extraordinary measures such as small steps and quick steps are taken to promote them. Among a group of young military leaders promoted in recent years, more than half have doctorates and master's degrees.
The General Armaments Department of the People's Liberation Army conscientiously follows the functions assigned by the State Council and the Central Military Commission, strengthens the audit supervision and management of national defense scientific research funds of the military and national defense science and technology industry departments, strives to improve the efficiency of the use of national defense scientific research funds, and effectively ensures the safety of new equipment and major national defense scientific research experiments completion of the task.
According to the person in charge of the Audit Bureau of the General Armaments Department, the national defense scientific research finance and audit department has taken various measures to strictly manage and audit national defense scientific research funds, which has further improved the efficiency of the use of national defense scientific research funds; the guarantee of national defense scientific research funds has been significantly strengthened, and management procedures have been strengthened. It is more standardized and the flow of funds is more reasonable; the national defense scientific research contract system has been further promoted and deepened, which has greatly promoted and guaranteed the smooth completion of major scientific research and test tasks; the audit and supervision of national defense scientific research funds has been strengthened, and a number of violations of national defense scientific research funds have been seriously investigated and punished The use of units and individuals specified in the management effectively ensures that national defense scientific research funds are earmarked for their exclusive use. An audit of the use of national defense scientific research funds for 26 key national defense projects and some scientific research units of various military industrial group companies shows that the use of national defense scientific research funds by the military and national defense science and technology industry departments is good, with standardized management and complete financial accounting systems, effectively ensuring the national defense The needs of scientific research and the development of new equipment. Significant progress has been made in the development of a number of new weapons and equipment, important breakthroughs have been made in a number of key national defense scientific and technological projects, the quality of national defense scientific research and test products has been significantly improved, and the progress of some key national defense scientific research projects has been advanced.
In August 2003, the General Armament Department of the People's Liberation Army adopted a competitive negotiation method and signed purchase contracts for space launch propellant railway vehicles with three vehicle manufacturers. This marks that the reform of the military equipment procurement system is gradually deepening.
Different types of space launch propellant railway vehicles, such as tank cars, maintenance cars, and passenger cars, used to be ordered from designated manufacturers. The cost of the vehicles continued to rise, but the technical performance, reliability, and after-sales service of the products did not improve significantly. In order to implement the "Equipment Procurement Regulations" and deepen the reform of the equipment procurement system, the General Equipment Department introduced a competition mechanism in vehicle ordering. Based on the technical characteristics of propellant transport vehicles and the actual conditions of the railway vehicle manufacturing industry, it used competitive negotiation for the first time to select contractors. factory. During the negotiation process, the Equipment Department followed the principles of "fairness, impartiality, science, and merit selection" and conducted a comprehensive evaluation of the manufacturers participating in the competitive negotiations from aspects such as quotation, quality, service, and credit standing. In the end, the three vehicle manufacturers with the lowest quotations and the best plans became the pre-transaction manufacturers. This purchase was 1.32 million yuan less than budgeted.中國政府資料來源:https://www.gov.cn/test/2005-06/28/content_10531.htm