America Instigating Cyber Warfare – How China Will Realize the Chinese Dream in the Age of American Cyber Warfare //
美國煽動網絡戰 – 中國如何在美國網絡戰時代實現中國夢
If a power-state wants to realize the dream of the empire, it was a world war 100 years ago, a nuclear war 50 years ago, and now it is a cyber war.
How does the United States face the cyber war era?
Core tips
In recent years, the United States has taken a number of measures to accelerate the development of cyber warfare. After the Obama administration took office, it continued to play the “eight-one” “combination boxing” to improve its cyber warfare capabilities.
Because the United States adheres to the concept of absolute security in cyberspace, this will not only aggravate the insecurity of the United States, but will also induce instability in the objective, resulting in instability of the cyberspace situation.
Recently, foreign media reported the latest progress of the US military in cyber warfare: the US military has spent five years developing advanced cyber weapons and digital combat capabilities, and these weapons may soon be deployed more publicly and will be considered for the next few years. “Network militia.” The US’s measures to accelerate the development of cyber war deserve our high attention and in-depth study.
The era of cyber war has arrived
Today, one-third of the world’s population uses the Internet, and billions of people accept the services provided by the Internet. The arrival of cyber warfare is an inevitable historical necessity. The network revolution is also reshaping the new pattern of world political, economic, social and cultural development.
Cyber warfare in many fields. Cyber warfare has broken through the traditional warfare field, making war a veritable development in economic, political, and military fields. First, the cyber warfare in the economic field is aggressive. In particular, cyber warfare in the financial sector has been described as “a modern version of the bank.” Second, the cyber war in the political arena has intensified. Social networking as a tool for political change represents an amazing power. From the turmoil in West Asia and North Africa to the “Autumn Wall Street”, social networks are everywhere to participate and help. Under the conditions of informationization, the destructive power of network penetration even exceeds military intervention. The third is the initial test of the cyber warfare in the military field. The network has changed the traditional war mode, from the Gulf War embedded virus attack to the Russian-Georgian conflict to use the network “bee colony” attack, each war has a network war “shadow.”
Cyber warfare has become the “atomic bomb” of the information age. The research of RAND Corporation puts forward: “The strategic war in the industrial era is nuclear war, and the strategic war in the information age is mainly cyber warfare.” Why can cyber warfare compare with nuclear war? Because the two have similarities in the “fission reaction” and the destruction effect. If the computer network is abstracted into the weaving of points and lines, the point is the computer and the router, the line is the network channel and the TCP/IP transmission protocol extending in all directions, and the network viruses such as Trojans and worms are the potential “uranium” in the network. Why do viruses in the network cause fission? There are two main reasons: First, the inherent defects of the computer architecture provide a “soil and hotbed” for the virus. The weapon of cyber warfare is a virus such as a Trojan, a worm (which is essentially a malicious code). The reason why malicious code can be raging is because there are exploitable vulnerabilities in the system, and the source of the vulnerability lies in the inherent shortcomings of the von Neumann architecture used by computers. The principle is to store data and programs in the read and write memory (RAM), the data can be read and written, and the program can be changed. In the cybersecurity incidents that occur in today’s world, more than 50% of the exploits that are exploited are mainly due to this mechanism. Second, the open shared Internet provides a path and bridge for the fission of the virus. “Network warfare: The next threat to national security and countermeasures” clearly states that there are five major flaws in the Internet: fragile domain name service systems, unverified routing protocols, malicious traffic without censorship, decentralized network structures, and Clear text transmission. Once these defects are exploited, they may form a flood of attacks on the network, which acts like a weapon of mass destruction, and is as powerful as the “atomic bomb” of the industrial age.
In the process of changing times and the evolution of war, who can take the lead in shifting the focus from the traditional field of human activities to new important areas, who can gain huge strategic benefits. It can be said that mastering the right to make nets in the 21st century is as decisive as mastering the sea power in the 19th century and mastering the air power in the 20th century.
Original Mandarin Chinese:
強權國家要想實現帝國夢想,100年前是發動世界大戰,50年前是籌劃核大戰,現在則是策動網絡戰
美國如何迎戰網絡戰時代
核心提示
近年來,美國採取多項舉措加快網絡戰的發展。奧巴馬政府上台以後,更是連續打出“八個一”的“組合拳”,提升網絡戰能力。
由於美國在網絡空間秉持絕對安全的理念,這不僅會加劇美國的不安全感,而且還會在客觀上誘發不安定因素,造成網絡空間態勢的不穩定。
近日,外媒報導美軍在網絡戰方面的最新進展:美軍已經花了5年時間開發先進的網絡武器和數字作戰能力,可能很快就會將這些武器進行更公開部署,並考慮未來數年建立“網絡民兵”。美國加快網絡戰發展的舉措值得我們高度重視和深入研究。
網絡戰時代已經到來
今天,全世界1/3人口使用國際互聯網,數十億人接受著網絡提供的各種服務。網絡戰的到來是不可阻擋的歷史必然,網絡革命也正在重塑世界政治、經濟、社會、文化發展的新格局。
多個領域迎來網絡戰。網絡戰已經突破傳統戰爭領域,使戰爭名副其實地在經濟、政治、軍事多個領域展開。一是經濟領域的網絡戰攻勢凌厲。特別是金融領域的網絡戰,被形容為“現代版的搶銀行”。二是政治領域的網絡戰愈演愈烈。社交網絡作為政治變革的工具體現了驚人的威力。從西亞北非動亂到“華爾街之秋”,處處都有社交網絡參與其中、推波助瀾。信息化條件下,網絡滲透的破壞力甚至超過軍事干預。三是軍事領域的網絡戰初試鋒芒。網絡改變了傳統戰爭模式,從海灣戰爭預埋病毒攻擊、到俄格衝突動用網絡“蜂群”攻擊,每一場戰爭都有網絡戰“影子”。
網絡戰成為信息時代的“原子彈”。蘭德公司研究提出:“工業時代的戰略戰是核戰爭,信息時代的戰略戰主要是網絡戰。”網絡戰為什麼能與核戰爭比肩?因為二者在“裂變反應”和破壞效果上極具相似之處。如果把計算機網絡抽象為點和線的編織,點就是計算機和路由器,線則是四通八達的網絡信道和TCP/IP傳輸協議,而木馬、蠕蟲等網絡病毒正是網絡中潛在的“鈾”。網絡中的病毒為什麼會產生裂變?主要有兩個原因:一是計算機體系結構的固有缺陷給病毒的產生提供了“土壤和溫床”。網絡戰的武器是木馬、蠕蟲(其實質是惡意代碼)等病毒。惡意代碼之所以能夠肆虐,是因為系統內存在可利用的漏洞,而漏洞的本源在於計算機採用的馮·諾依曼體系結構的先天不足。其原理是把數據和程序都統一存儲在讀寫存儲器(RAM)內,數據是可以讀寫的,程序也是可以改變的。當今世界發生的網絡安全事件,50%以上被利用的漏洞主要是源於這個機理。二是開放共享的互聯網為病毒的裂變提供了途徑和橋樑。 《網絡戰:國家安全的下一個威脅及對策》一書明確指出,互聯網存在五大缺陷:脆弱的域名服務系統、不經過驗證的路由協議、不進行審查的惡意流量、非集中式的網絡結構以及明文傳送。這些缺陷一旦被利用,就可能形成對網絡的攻擊洪流,其作用類似於大規模毀傷性武器,威力不亞於工業時代的“原子彈”。
在時代更迭、戰爭演變的進程中,誰能夠率先把關注點從人類活動的傳統領域轉入新的重要領域,誰就能獲得巨大戰略利益。可以說,21世紀掌握製網權與19世紀掌握制海權、20世紀掌握制空權一樣具有決定意義。
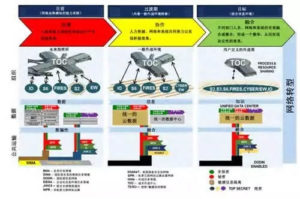
The main measures for the United States to accelerate the development of cyber war
Obama, who relies on the success of the network operator, attaches great importance to the construction of cyberspace. He delivered a “5·29” speech when he came to power, and believed that protecting the network infrastructure would be the top priority for maintaining US national security. During his tenure, Obama successively launched the “eight-one” “combination boxing”, which made the US cyber war into a period of rapid development.
The first is to launch a report. In the “Network Space Security Policy Assessment Report”, it emphasizes that cyber war is related to national security, affects social stability, is related to economic development, and determines the outcome of war.
The second is to strengthen a strategy. It has established a “three-in-one” national security strategy supported by the deterrent strategy of nuclear weapons, the preemptive strategy of space, and the network’s control strategy.
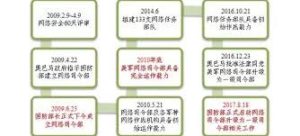
The third is to form a headquarters. In 2009, the US military established the Cyberspace Command, which is the main function of commanding cyber warfare. In May 2013, the US military set up a “joint network center” at each theater headquarters, and its cyber warfare command system was gradually improved. At the same time, the US military also plans to upgrade the Cyberspace Command to a formal combatant command, making it a level of organization with other theater headquarters. This will directly shorten the chain of command of the US cyber warfare forces and the military.
The fourth is to develop a road map. In 2010, the US Army officially issued the “Network Space Combat Capability Conception”, which is considered to be the first roadmap for the development of cyber warfare capabilities developed by the US military.
The fifth is to start a shooting range. In 2009, the US Department of Defense launched the “National Network Shooting Range” project, which was officially delivered in 2012. The US cyber warfare training and weapon evaluation have a realistic environment.
The sixth is to develop a series of weapons. The US military has developed and stocked more than 2,000 virus weapons, and these weapons are gradually moving toward a systemic direction. There are mainly anti-smuggling weapons represented by “seismic net” virus and “digital cannon”, intelligence warfare weapons represented by “flame” and “Gauss” virus, and psychology represented by “shadow network” and “digital water army”. War weapons.
The seventh is to plan a series of exercises. From 2006 to the present, the United States has organized several cross-border cross-border “network storm” exercises. Every time, the Internet is listed as an offensive and defensive target, targeting key infrastructure such as finance, transportation, electricity, energy, and communications. This reveals the main battlefield of cyberspace, which is an open Internet rather than a closed tactical network.
Eight is to support a number of social networking sites. A number of social networking sites such as “Twitter” and “Facebook” have become strategic tools to interfere in his internal affairs. This is a punch in the combination punch. In February 2013, after the overthrow of the opposition government in Tunisia and Egypt, Obama fully affirmed the important role played by Internet companies such as “Twitter” and “Facebook”. According to statistics, only “Facebook” social networking sites have more than 1.3 billion users worldwide.
Published the “Network War Declaration.” Obama’s move after the ruling shows that the United States has officially incorporated cyber warfare into the category of war and classified cyberspace as a new operational domain, reflecting the US’s advanced forecast and preemptive design for future wars. There are two main reasons for its deep motivation: First, to ensure its own network security – reflecting the United States’ concerns about its information security. The second is to ensure global cyber hegemony – reflecting the new concept of the American war.
In 2014, the US military actually promoted the “Network Space Warfare Rules” and “Network Space Warfare Joint Order”, which led to the international strategic competition to focus on the new global public domain of the Internet. The actions of the United States from the domestic to the international, the slave network to the use of force, from the declaration to the action, from the colonial land to the colonial thinking reflect the United States attempting to format the whole world with American values through the Internet. As one reporter said: “Modern American colonization is thought, not land.”
In April 2015, the United States released a new version of the Network Strategy Report, which comprehensively revised the 2011 Cyberspace Action Strategy Report issued by the US Department of Defense. It has the following new changes:
First, it provides a new basis for enhancing the important position of network power construction. The report further raises the threat of US cyberspace to a “first-tier” threat. At the same time, the report also regards China, Russia, Iran, and North Korea as potential “network opponents” in the United States. This is the latest and most serious judgment on the cyber threat situation.
The second is to provide new guidance for speeding up the construction of cyber warfare forces. The report focused on the three major tasks and five major goals of the Ministry of Defense in cyberspace, and further refined the construction goals of 133 cyber warfare detachments.
The third is to create a new pillar for maintaining a comprehensive military advantage. The report clearly stated that when the United States faces an attack against the interests of the United States or the United States in cyberspace, the US military can conduct cyber operations and implement cyber attacks. This is the most important adjustment to this cyberspace strategy. In the future, the US military will use cyber attacks as an important means of warfare. This is the main manifestation of the United States’ concept of “moving the Internet with the use of force” in cyberspace.
The fourth is to create new conditions for reshaping the international network system. The report emphasizes the emphasis on strengthening the coordination between the military and the civilians; the key external development and cooperation with allies. The main goal of the cooperation is to share the costs and risks, promote the international code of conduct that is beneficial to the United States, and seize the right to speak and lead in the formulation of cyberspace rules.
Original Mandarin Chinese:
美國加快網絡戰發展的主要舉措
依靠網絡運營商競選成功的奧巴馬,對網絡空間的建設非常重視,一上台就發表了“5·29”講話,認為保護網絡基礎設施將是維護美國國家安全的第一要務。在任期間,奧巴馬連續打出了“八個一”的“組合拳”,使美國網絡戰進入快速發展時期。
一是推出一個報告。其在《網絡空間安全政策評估報告》中強調:網絡戰事關國家安全、影響社會穩定、關乎經濟發展、決定戰爭勝負。
二是強化一個戰略。其確立了以核武器的威懾戰略、太空的搶先戰略、網絡的控制戰略為支撐的“三位一體”國家安全戰略。
三是組建一個司令部。 2009年,美軍成立了以指揮網絡戰為主要職能的網絡空間司令部。 2013年5月,美軍在各戰區總部組建“聯合網絡中心”,其網絡戰指揮體係日漸完善。同時,美軍還計劃將網絡空間司令部升格為正式的作戰司令部,使其成為與其他戰區司令部平級的機構。此舉將直接縮短美國網絡戰部隊與軍方最高層的指揮鏈。
四是製定一個路線圖。 2010年,美陸軍正式出台《網絡空間作戰能力構想》,這被認為是美軍制定的首份網絡作戰能力發展路線圖。
五是啟動一個靶場。 2009年,美國防部啟動了“國家網絡靶場”項目,2012年正式交付使用,美國網絡戰演習訓練、武器測評擁有了逼真環境。
六是研發一系列武器。美軍已研發儲備了2000多種病毒武器,這些武器逐漸向體系化方向發展。主要有以“震網”病毒、“數字大砲”為代表的阻癱戰武器,以“火焰”“高斯”病毒為代表的情報戰武器和以“影子網絡”“數字水軍”為代表的心理戰武器。
七是策劃系列演習。從2006年到現在,美國已經組織了多次跨界跨國跨域“網絡風暴”演習。每一次都把互聯網列為攻防目標,瞄準的都是金融、交通、電力、能源、通信等關鍵基礎設施。這揭示了網絡空間的主戰場,是開放的國際互聯網而不是封閉的戰術網。
八是扶持一批社交網站。把“推特”“臉書”等一批社交網站變為乾涉他國內政的戰略利器。這是組合拳中的一記重拳。 2013年2月,在突尼斯、埃及政府被反對派推翻後,奧巴馬充分肯定了“推特”“臉譜”等網絡公司在其中發揮的重要作用。據統計,僅“臉譜”社交網站的全球用戶已超過13億。
發表“網絡戰宣言”。奧巴馬執政後的舉措,表明美國已經正式將網絡戰納入戰爭範疇,把網絡空間列為新的作戰域,這反映出美國對未來戰爭的超前預測和搶先設計。其深層動因主要有兩點:一是確保自身網絡安全———反映了美國對其信息安全的擔憂。二是確保全球網絡霸權———反映了美國戰爭的新理念。
2014年,美軍實案化推進《網絡空間作戰規則》和《網絡空間作戰聯合條令》,牽動國際戰略競爭向互聯網這一新全球公域聚焦。美國這些從國內到國際、從動網到動武、從宣言到行動、從殖民土地到殖民思想的行動舉措,反映出美國企圖通過互聯網,用美式價值觀格式化整個世界。正如一位記者所說:“現代美國殖民的是思想,而不是土地”。
2015年4月,美國又發布了新版網絡戰略報告,對2011年美國國防部出台的《網絡空間行動戰略報告》進行了全面修訂。其主要有以下幾個新變化:
一是為提升網絡力量建設重要地位提供新的依據。該報告進一步把美國在網絡空間的威脅上升為“第一層級”的威脅。同時,該報告還將中國、俄羅斯、伊朗、朝鮮視為美國潛在的“網絡對手”,這是其對網絡威脅形勢做出的最新、最嚴峻的判斷。
二是為加快網絡戰力量建設提供新的指導。報告重點明確了國防部在網絡空間的三大任務和五大目標,並進一步細化133支網絡戰分隊的建設目標。
三是為維持全面的軍事優勢打造新的支柱。報告明確提出,當美國面臨針對美國本土或美國在網絡空間利益的攻擊時,美軍可以進行網絡作戰,實施網絡攻擊。這是此次網絡空間戰略最重要的調整。未來,美軍將把網絡攻擊作為重要的作戰手段使用。這是美國在網絡空間“動網就動武”理念的主要體現。
四是為重塑國際網絡體系創造新條件。報告強調,對內重點加強軍民協同;對外重點發展與盟友合作。合作的主要目標是分擔成本和風險,推行對美有利的國際行為準則,搶奪網絡空間規則制定的話語權和主導權。
The three key pillars of the United States to accelerate the development of cyber war
There are three key pillars for the United States to accelerate the development of cyber warfare:
Technical pillar. The “Prism Gate Incident” further confirms that the United States has been monitoring the global network to the point of pervasiveness. The United States occupies the upstream of the industrial chain. From basic chips to hardware applications, from operating systems to commercial software, Midea has an absolute technological advantage, forming a complete set of industrial chains, supply chains and information chains. The overwhelming advantages of technology and the monopoly in many core markets are key to the acceleration of cyber warfare in the United States.
Discourse pillar. The powerful ability of the United States to act in cyberspace determines its strong voice in online diplomacy. No matter what double standards it exhibits in cyberspace, it can influence the global public opinion space under the support of powerful discourse. Without the emergence of the “Prism Gate Incident,” the United States has created two “lie” that have become truths around the world: first, the West is a victim of cyberattacks; and second, China is a source of cyberattacks. This has greatly damaged China’s national image, reputation and international status in the international community, seriously affecting China’s high-tech exports, and achieving the “four-two-pound” effect that is difficult to achieve using trade protection and WTO rules. Even if the “Prism Gate Incident” tears open the “fair of justice” of the United States, it still shows superior combat capability, claiming to be monitored by itself, and placing national security on the basis of personal privacy in the name of counter-terrorism. Firmly control the right to speak in cyberspace.
Strategic pillar. A higher level than the technical pillar and discourse pillar is the strategic pillar. The core of the US strategic pillar is reflected in the pre-emptive global strategy and the overall layout of the game power. First, the advantages of multiple forces complement each other. At present, the United States is actively cultivating cyber security companies such as “Fire Eyes”, using their technological advantages and unofficial background to globally control, long-term tracking, collecting evidence, and acting as a pioneer, while the government and the military are hiding behind the scenes. This has earned the US diplomacy a flexible space for attack and retreat. Second, the network attack and defense and theft of intelligence are clear. The clear strategic division of labor has brought the benefit to the United States. Even if the “Prime Gate Incident” broke the news, the National Security Agency was “spoken” by the world, but there was no such thing as its cyberspace command. Instead, the cyberspace command made the cyberspace command The maintenance of national security is an excuse to accelerate the expansion of the army and develop at a high level. The United States has two clear main lines in cyberspace, namely: the National Security Agency is in charge of the network, and the Cyberspace Command is in charge of the network. This clear strategic thinking has provided strong support for the United States to accelerate the development of cyber warfare.
Original Mandarin Chinese:
美國加快網絡戰發展的三個關鍵支柱
美國加快網絡戰發展有三個關鍵性支柱:
技術支柱。 “棱鏡門事件”進一步證實美國對全球網絡的監控達到了無孔不入的程度。美國占據了產業鏈上游,從基礎芯片到硬件應用,從操作系統到商用軟件,美都具有絕對的技術優勢,形成了一整套完整的產業鏈、供應鍊和信息鏈。技術領域的壓倒性優勢和在眾多核心市場的壟斷地位是美國能加快網絡戰發展的關鍵。
話語支柱。美國在網絡空間強大的行動能力決定了其在網絡外交上強大的話語權。無論它在網絡空間展現怎樣的雙重標準,都能在強大的話語支撐下影響全球輿論空間。要是沒有“棱鏡門事件”的出現,美國已在全球製造出兩個已經成為真理的“謊言”:第一,西方是網絡攻擊受害者;第二,中國是網絡攻擊源。這在國際社會極大地損害了中國的國家形象、信譽和國際地位,嚴重影響了中國的高科技出口,達到了利用貿易保護和WTO規則博弈難以實現的“四兩撥千斤”效果。即便是“棱鏡門事件”撕開了美國的“正義面紗”,它仍然表現出超強的戰鬥能力,對外聲稱自己被監控;對內以反恐為名,將國家安全置於個人隱私之上,牢牢掌握著網絡空間的話語權。
戰略支柱。比技術支柱和話語支柱更高一層的是戰略支柱。美方的戰略支柱核心體現在先發製人的全球戰略和博弈力量的整體佈局。一是多元力量的優勢互補。目前,美國積極培植“火眼”這樣的網絡安全企業,利用他們的技術優勢和非官方背景在全球布控、長期跟踪、蒐集證據、充當先鋒,而政府和軍隊則躲在背後,水到渠成時再投入博弈,這為美國的外交贏得了進可攻、退可守的彈性空間。二是網絡攻防和竊取情報涇渭分明。清晰的戰略分工對美國帶來的好處是,即使“棱鏡門事件”的爆料讓美國國家安全局被世界“吐槽”,但是卻絲毫沒有殃及其網絡空間司令部,反而使網絡空間司令部以維護國家安全為藉口,理直氣壯加速擴軍,高調發展。美國在網絡空間有兩條清晰的主線,即:國家安全局主管網絡獲情,網絡空間司令部主管網絡攻防。這種清晰的戰略思路為美國加快網絡戰發展提供了強有力的支撐。
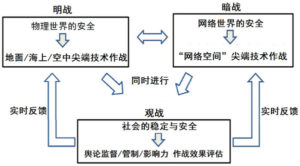
Absolute Security: Double Standards and Realistic Paradox of American Cybersecurity Concept
It can be seen that on the issue of network security, the United States pursues the concept of absolute security and attempts to use force to move the military to achieve absolute control over cyberspace. It can be seen from Snowden’s breaking news that the US network monitoring of the international community is systematic, large-scale, and uninterrupted, but it requires other countries to strictly control itself, and it cannot be half-step. This is an asymmetrical mindset and a double standard.
Is it feasible? The problem of cyberspace is very complicated, and the processing methods cannot be too simple. To deal with these problems, new rules, new methods, and new thinking are needed. First, there are many kinds of cyberspace actors, and they are mixed. Second, the attack path and source can be virtual forged, and the source of evidence must rely on multiple parties. Due to the complexity and uncertainty of virtual space, many rules of armed conflict law for physical space are difficult to use in cyberspace. For example: How to define war and peace in cyberspace? How to distinguish between military targets and civilian targets? How does the neutral concept apply? In a country that declares neutrality, it is difficult to control the computer malicious code of others without flowing through the network equipment in its own territory, and it is difficult to avoid the control and utilization of the network facilities of the belligerents. For example, in the case of cyber attacks in foreign countries, network equipment in China has also been used by hackers as “broilers” and “springboards”. China is an innocent victim. If “the state responsibility of cyberattacks launched through the country is not properly prevented by “neutral state standards” and “the destruction of cyberattacks by force”, China may suffer innocent blame. And the United States has such a strong technology that it is difficult to completely prevent being exploited, attacked, and controlled. Cyberspace cannot easily be judged or written. Management methods and patterns suitable for physical space may not be suitable for virtual space. Feel free to reduce the trajectory of cyberspace, and at the same time push up the risk of conflict escalation. Therefore, any dispute arising out of cyberspace should be resolved in a peaceful manner and should not be threatened by force or by force.
Is the effect controllable? There are two situations in which a consequence assessment is required. First, what should I do if I misjudge? Simplifying the threshold of attack can make a neutral country or an innocent suffer a disaster. Second, can you solve the problem? In 2014, local conflicts such as the Ukrainian crisis and the Palestinian-Israeli conflict led to cyber conflicts, and large-scale cyber attacks continued to take place. Western countries headed by the United States have imposed sanctions on Russian banks and enterprises, resulting in a clear upward trend in cyberattacks against the US financial industry. It can be seen from the effect evaluation that it cannot be said that deterrence and force have no effect on the solution of the problem, but it is not a panacea. If a big country like the United States and Russia uses force in cyberspace, what kind of negative effects and consequences will this bring to world peace?
Is it desirable to think? Although the United States has the most powerful army and the most advanced technology in the world, it is still constantly looking for opponents, rendering crises and exaggerating threats. This makes the whole world lack of security, objectively induces unstable factors, and stimulates negative energy and potential threats. It is precisely because the United States pays too much attention to its own national interests and is unwilling to adjust its strategic demands for the sound development of the international system. This has led the United States to continually fall into the “security dilemma” and “more anti-terrorism” circles since the “9.11” incident. This phenomenon deserves the United States to ponder.
(The author is the vice president of the National Innovation and Development Strategy Research Association)
Original Mandarin Chinese:
絕對安全:美國網絡安全觀的雙重標準及現實悖論
可以看出,在網絡安全問題上,美國奉行絕對安全的理念,企圖通過動網就動武,實現對網絡空間的絕對控制。通過斯諾登的爆料可以看出,美國對國際社會的網絡監控是系統的、大規模的、不間斷的,但是其要求其他國家嚴格自我管控,不能越雷池半步。這是一種不對稱的思維,也是一種雙重標準。
方法上是否可行?網絡空間的問題非常複雜,處理方法不能過於簡單,處理這些問題需要有新規則、新方法、新思維。一是網絡空間行為體多種多樣,“魚龍混雜”。二是攻擊路徑、源頭可以虛擬偽造,溯源取證要靠多方配合。由於虛擬空間的複雜性、不確定性,用於實體空間的武裝衝突法的很多規則很難在網絡空間使用。例如:在網絡空間戰爭與和平如何界定?軍用目標和民用目標如何區分?中立概念如何適用?一個宣布中立的國家,很難控制他人的計算機惡意代碼不流經自己領土內的網絡設備,也很難躲避交戰方對其網絡設施的控制和利用。例如在外國發生的網絡攻擊事件中,中國境內的網絡設備也被黑客用作“肉雞”和“跳板”,中國是無辜的受害方。如果以“中立國標準追究沒有適時阻止經由本國發動的網絡攻擊的國家責任”,“以武力毀傷摧毀網絡攻擊來源”,中國可能會遭受無辜的非難。而美國有那麼強的技術也難以完全阻止被利用、被攻擊、被控制。網絡空間不能輕易下判書、下戰書。適合實體空間的管理方法和模式未必適合虛擬空間。隨意降低網絡空間動武門檻,同時會推高衝突升級的風險。因此,網絡空間發生的任何爭端應以和平方式解決,不應使用武力或以武力相威脅。
效果上是否可控?有兩種情況需要作後果評估。第一,誤判了怎麼辦?簡單化地降低打擊門檻可能會讓中立國或無辜者蒙受災難。第二,能否解決問題? 2014年,烏克蘭危機、巴以沖突等局部地區對抗導致網絡衝突不斷,大規模網絡攻擊事件持續上演。以美國為首的西方國家對俄銀行、企業進行製裁,導致對美金融行業的網絡攻擊呈明顯上升趨勢。由此可見,從效果評估看,不能說威懾和武力對問題的解決沒有效果,但它不是萬能的。如果美俄這樣的大國在網絡空間動武,這會給世界和平帶來什麼樣的負面效應和惡果?
思維上是否可取?儘管美國擁有世界上最強大的軍隊、最先進的科技,但仍然在不斷尋找對手、渲染危機、誇大威脅。這讓整個世界缺少安全感,客觀上誘發不安定因素,激發負能量和潛在威脅。正是因為美國過度關注自身的國家利益,不願意為了國際體系良性發展,調整戰略訴求,才導緻美國從“9·11”事件以來,不斷陷入“安全困境”和“越反越恐”的怪圈,這種現象值得美國深思。
(作者係國家創新與發展戰略研究會副會長)。
Original Referring URL: http://www.81.cn/wjsm/2016-02/17/