China’s Military Taking Action to Defend Nation’s Network //
中國軍事行動維護國家網絡
網絡營門”走向守衛“網絡國門

Original title: from the guard “network camp” to guard the “network country”
Original: “National Defense Reference” 2017 No. 3
Cyber space was born in the military field, such as the first computer, Apache and GPS navigation systems are all derived from the military, today, cyberspace security has been closely related with national security, the military has once again become the maintenance of national cyberspace security , Whether it is the face of normalized network penetration, or large-scale network attacks, are an urgent need for the military from the guard “network camp” to guard the “network country”, breaking the traditional mission of the military mission, breaking the traditional battle preparation mode, To a new network of national defense thinking, casting the network era of the firm.
From the “network camp” to “network country”, a new era of military mission to bring new trends

Internet space is not only related to the maintenance of national strategic interests, a direct impact on political, economic, cultural security and social development, has become a modern battlefield joint war blood and ties. The Chinese army can not be limited to maintaining the internal security of the barracks, but also take the initiative to adapt to the trend of the times, the courage to take the “network of countries,” the country to play. Network strength is an important part of the network power construction, from the “network gate” to “network country” is the information age situation at home and abroad the inevitable trend of development.
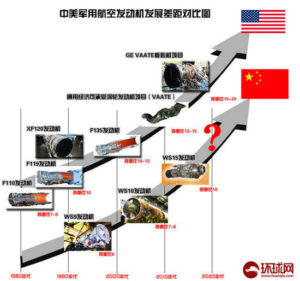
Guarding the “network country” is the cyberspace security situation forced. China as the first network power, the security situation is not optimistic, the strategic opponent has never stopped preparing for my network operations. The United States, Britain, France and other countries actively preparing for cyberspace, through the cyberspace security legislation to give the military functions, the development of network warfare forces, research and development of network warfare weapons equipment, the war will advance to the human “fifth space”, especially in China increasingly strong In the process of rising history, the western countries under the auspices of the Cold War mentality and containment subversion strategy, the use of network technology and means of communication to implement uninterrupted harassment, subversion and cyber attacks, seriously affecting my country’s security and social development, China has become Network security threats to the hardest hit, the virus attack the test field, the penetration of awareness of the destination, the national security is facing a huge risk.
In the coming period, China, as a big emerging country, will intensify its conflicts of interest, strengthen the network defense strategy and strengthen the cyberspace war preparation. It is an inevitable way to actively strive for the dominance and discourse of cyberspace. The only way to go. As the main force of national security and stability, the army must meet the requirements of cyberspace characteristics and become the backbone and main force against cyber invasion, network subversion and safeguard national security and social stability.
Winning the network war is the new military change in the information age. As one of the most advanced productive forces in the information age, network technology has made cyber space combat become the dominant factor to guide the evolution of modern warfare, which affects the whole situation of war. In recent years, from the Iranian “earthquake network” attack, Russia and Georgia conflict network warfare, the Ukrainian power grid was a large number of paralysis and the US military on the IS network attacks, cyberspace in combat show a huge role in the emergence of a sign that the network Has become an important model for future joint operations.
The US military attaches great importance to the construction of cyberspace armaments, the establishment of cyberspace headquarters, the introduction of cyberspace joint operations, a substantial expansion of network warfare forces, and strive to maintain its cyberspace hegemony, the control of cyberspace as a “third offset strategy “Absolute advantage of the most important content of competition.
The world has followed up the country, the military space militarization trend is obvious. Severe cyberspace The situation of military struggle requires the Chinese army to focus on the network battlefield space changes, to meet the requirements of the era of information warfare, to achieve in the cyberspace can fight, win the battle of the strong military goals.
Effective network of deterrence is to speed up the construction of the network power inherent. In China by the network power to the network power development process, can not do without a strong network space military power as a guarantee. The international competition of cyberspace is a comprehensive game of national comprehensive strength. Among them, the network military capability construction is directly related to the national security and stability, and the whole body is the core factor of the whole national security field.
At present, the interests of the world in the cyberspace mutual penetration, there “you have me, I have you, mutual cooperation and common development” situation. But this common development is not equal, the United States and Western powers to use cyberspace dominance, has made a certain degree of network deterrence, so that my network development and interests subject to others. How the army in the construction of the network to complete the mission of reorganization of the mission, the premise is to be able to contain the crisis, deter opponents of the network offensive and defensive ability to ensure the peaceful development of the network environment.
Therefore, the army needs to establish a deterrent strategic goal of effective deterrence, form a strategic balance with the enemy “destroy each other”, so as to enhance the strategic competitiveness, deter cyber space aggression and ensure the smooth development of the network power strategy.
From the “defensive responsibility” to “protect the network defenders”, the new situation requires the army to undertake new tasks
The army is to defend the national security of the main and pillars, cyberspace is no exception. The National Security Act of July 1, 2015 stipulates that “citizens of the People’s Republic of China, all state organs and armed forces, political parties and people’s organizations, enterprises and other organizations and other social organizations have the responsibility to safeguard national security And obligations. “The Network Security Act promulgated in November 2016 emphasized the need to maintain cyberspace sovereignty and national security.
On the basis of the laws of the two countries, the National Cyberspace Security Strategy (hereinafter referred to as the “Strategy”) was formally introduced on December 27, 2016, providing overall guidance for creating a new model of network power at a new starting point. Basically follow, clearly put forward nine strategic tasks, and further reflects the army in the process of building a network of power in the mission task.
Full of network of national mission, the army to defend the sovereignty of cyberspace strong pillars. “Strategy” listed in the nine strategic task is the first “firmly defend cyberspace sovereignty,” made it clear that “including economic, administrative, scientific and technological, legal, diplomatic, military and all other measures, unswervingly maintain our network Space sovereignty “. It can be seen that the military must assume the national mission of using the physical means of the physical space to defend the sovereign security and interests of the virtual cyberspace.
Internet space sovereignty is the core interests of the country, is an important component of national sovereignty, that the state in the cyberspace owned by the independent, equal rights, self-defense and management rights. Once the hostile forces have violated my cyberspace sovereignty, it is equivalent to violating the sovereignty of the landspace and other physical space, China will have the right to take all measures, including military means to give a strong fight back.
At the international level, the United States has long proposed a cyberspace deterrence strategy, declared the attack on the US network information facilities is equivalent to the war, the United States will take military strike measures to retaliate. Military means is the fundamental means of safeguarding national sovereignty, and plays a vital role in safeguarding national cyberspace security. Therefore, the historical forces of land, sea and air, should be given the historical mission of protecting the sovereignty of cyberspace, must rely on the powerful physical space to defend the national interests of cyberspace, a powerful deterrent to the hostile forces of the network destruction attempt.
According to the era of network security to play, the army to do to defend the national security of the ballast. The second focus of the “strategy” task emphasizes the need to resolutely safeguard national security, prevent, stop and punish any act of using the Internet for treason, secession, incitement to rebellion, subversion or incitement to subvert the people’s democratic dictatorship.
In the era of information network, the world’s military has become an important participant in cyberspace. The level of cyberspace capability has become one of the main indexes to evaluate the modernization degree of a country’s army. It is one of the main responsibilities of the information security army to carry out the task of network space mission.
From the historical process of China’s development, it is necessary to be highly vigilant about the national security strategy needs of the successful completion of the well-off society. It is necessary to be highly vigilant about the risk of being invaded, subversive and divided by cyberspace. The development of the overall situation of the danger of being destroyed, a high degree of vigilance of the development process of socialism with Chinese characteristics is disturbed, the risk of destruction.
Take preventive measures, requiring the state must have the means to deal with and deal with these dangerous measures, with the prevention, suppression and punishment of cyberspace according to the law of the powerful forces of destruction. The defense of the country has always been an unshirkable historical responsibility of the army. The inherent mission task determines that the Chinese army must take on the various measures taken in cyberspace to maintain national politics, economy, cultural security and social stability.
Offensive and defensive both strategic tasks, the army to enhance the ability to enhance the network space strong backing. The third and eighth of the nine major tasks in the Strategy make it clear that all necessary measures should be taken to protect critical information infrastructures and their important data from attack and destruction, and that both technology and management should be adhered to both protection and deterrence. Construction and international status commensurate with the network power to adapt to the network space protection, and vigorously develop the network security and defense means to detect and resist the network invasion, casting and maintenance of national network security strong backing. In all the state’s political, diplomatic, military, scientific and technological capacity to maintain security, military power has always been the foundation and support of all abilities. It is the fundamental guarantee of all ability and the ultimate guarantee of national security.
Therefore, the army must assume the strategic task of strengthening the national network space protection ability strong backing. In the real world, the army is the reassurance of safeguarding national security. In cyberspace, it should also become the safe dependency and guarantee of the people. As an important part of the national network space protection ability, the army must be both offensive and defensive, and have the ability to firmly safeguard the interests and security of the country and the people in the cyberspace, and can effectively eliminate the various crises and ideological turbulence caused by the network security threat So that people can truly feel the production and life to be effectively protected, as the people of the country’s network protection capacity of confidence in the emboldened.
The global responsibility of the joint defense, the military to do to maintain the important support of global network security. The final mandate of the Strategy explicitly proposes to strengthen international cooperation in cyberspace and to support the United Nations in its leading role in promoting the development of international rules for cyberspace, international cyberspace international counter-terrorism conventions that are universally accepted, and a sound mechanism for combating cybercrime Policy and law, technological innovation, standards, emergency response, key information infrastructure protection and other areas of international cooperation.
Cybercrime and cybercrime are the new forms of global threat catalyzed by information network fermentation, posing a great threat to the political, economic, military and cultural security of all countries in the world. It is not enough to rely solely on the power of government and civil society. And other Western countries have given the military the responsibility to protect the network security and the right to combat cyber terrorism. Maintaining global cyberspace security and stability is in line with the fundamental interests of China and the rest of the world. The army should be an important defender of cyberspace security and become an important force in combating global cybercrime and cybercrime.
The globalization and unboundedness of the network determines the international demand for combating cyber-terrorism and transnational cybercrime. The army should promote inter-State network governance and military cooperation within the framework of the UN Security Council, and use the strategy and technology of the Internet age to establish a joint defense Mechanism, and effectively safeguard the national and world cyberspace security.
From the “battlefield training” to “network preparation”, the new areas need to prepare for the military new initiatives
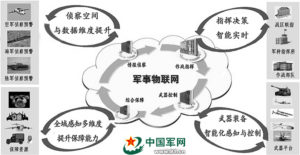
In the new historical situation, the cyberspace put forward new requirements to the military training mode, should adapt to the new features of the cyberspace and the new mission of the army to innovate and reform the traditional model, aim at the goal of strengthening the country and strengthening the macro- Focus on cyberspace military action legal needs, closely linked to cyberspace “military and civilian one” of the natural properties, the construction of “peace and war” network security attack and defense system, to create “military dual-use” network defense force.
Legislative empowerment, for the military to carry out functional mission to provide legal basis. Countries in the world, especially the Western developed countries in the network security legislation attaches great importance to network defense issues. The United States has promulgated the “National Security No. 16 Presidential Decree” “cyberspace action strategy” and a series of policies and regulations on how to protect the national network security in the field of national network security has been deepening norms.
At present, it is necessary to clarify the duties of the cyberspace army from the legal level. It should be based on the “National Security Law” and “Network Security Law”, and introduce the network defense law and relevant cyberspace military warfare regulations for network defense construction and military Action to provide regulatory support and action programs, so that the military in cyberspace responsibilities and mission more specific and specific.
First, through the network of national defense legislation to further define the network sovereignty and network frontier, clear the scope of the military duties.
Second, through the construction of network operations laws and regulations, clear the military to defend the national network space security action authority, to distinguish between network intrusion, network damage and other military means of behavior. Third, through the international cooperation policy of cyberspace, clear military cooperation with other countries, civil forces and other international networks to combat terrorism, cybercrime function tasks.
Military and civilian integration, for the construction of network power to provide innovative power. The integration of military and civilian integration is the main practice of enhancing the competitiveness of cyberspace in the world. For the construction of China’s network power, it is necessary to construct military and civilian defense and defense system, and to develop military and national defense information infrastructure. Source.
First, the co-ordination of national, military and all levels of government and other military and civilian integration functional departments, set up a special command and coordination agencies, mobilize all national network power, building “military and civilian” “peace and war” network security attack and defense system.
Second, as soon as possible the introduction of network security integration of civil and military development of the guiding ideology, and gradually expand the integration of basic legal research and demonstration, to guide the long-term integration of military and civilian development.
Third, relying on the country’s existing public mobile communication network, optical fiber communication network and satellite system, the military and the people to build a nationwide information infrastructure, to achieve military and civilian unity, in charge of sharing.
The fourth is to establish a joint emergency response mechanism for military and civilian personnel, to increase the capacity of the training departments to control the situation, to strengthen the expertise of experts and emergency professionals to enhance the ability to quickly restore damaged networks or information systems.
Military and civilian training, for the cyberspace military capabilities to provide a realistic environment. The common characteristics of military and civilian space in the network space make the military and civilian training become an important way of military military training in cyberspace all over the world. The United States and NATO and other countries of the network space military and civilian joint exercises have been a series of “network storm” “network guards” and other training activities to attract the government, enterprises, research institutions and even private hackers extensive participation. Our military cyberspace military strength training also requires extensive participation in civil forces.
First, do a good job of military and political cooperation, the establishment of military and civilian joint attack and defense exercise mechanism, learn from the United States and other developed countries in the network warfare exercises in the red and blue confrontation training methods, and actively build the “national network shooting range”, planning the government, civil society series of joint exercises to enhance military and civilian , Officials and one network of offensive and defensive level.
Second, do a good job in military and military cooperation, relying on the Internet to set up a network of enterprises to improve the training area, to promote military and civilian ability to run between the offensive and defensive, and jointly improve the ability to prevent unknown risks.
Third, the organization of civil network security companies and hackers talent, to carry out network security competition and other activities, mutual confirmation, and jointly improve the level of network security technology and tactics.
Network reserve, to build a strong network of troops to provide the source of strength. Reserve as a reserve force of national defense, both military and civilian dual characteristics, is to achieve cyberspace economic development and national defense construction of organic unity of the powerful initiatives.
First, the national security sector as the leading, according to the national interests of the overall planning, the introduction of the network defense reserve is conducive to the construction of a series of laws and regulations, from the top to solve the network defense reserve construction in the construction of the main division of labor, promotion strategy, problem.
Second, innovative reserve organization and leadership system and comprehensive coordination mechanism, there are plans to reserve construction into the national network of information development at all levels and various fields.
Third, focus on the military and local management reform of the two models to the provincial and municipal governments, military and local enterprises and institutions under the management mechanism to establish a network of national defense reserve personnel to jointly use the mechanism, improve the national emergency mobilization mechanism, the establishment of national network defense professionals Database, the network militia and reserve forces into the scope of the people’s armed mobilization, usually in accordance with the provisions of the militia emergency unit into the training, the urgent selection of elite personnel with the team to participate in the task of non-war military operations, wartime, So that the national defense potential into national defense strength. (An Weiping, deputy chief of staff of the northern theater)
Original Mandarin Chinese:

原題:從守衛“網絡營門”走向守衛“網絡國門”
原載:《國防參考》2017年第3期
網絡空間誕生於軍事領域,如首台計算機、阿帕網和GPS導航系統等都源於軍方,時至今日,網絡空間安全已與國家安全息息相關,軍隊又再次成為維護國家網絡空間安全的主角,無論是面對常態化的網絡滲透,還是大規模的網絡攻擊,都迫切需要軍隊從守衛“網絡營門”走向守衛“網絡國門”,突破傳統的軍隊使命任務,突破傳統的應戰備戰模式,以全新的網絡國防思維,鑄造網絡時代國之堅盾。
從“網絡營門”到“網絡國門”,新時代帶來軍隊使命新趨勢

網絡空間不僅事關國家戰略利益維護,直接影響政治、經濟、文化安全和社會發展,也成為現代戰場聯合作戰的血脈和紐帶。中國軍隊不能局限於維護軍營內部網絡安全,更要主動適應時代趨勢,勇於承擔把守“網絡國門”的國家擔當。網絡強軍是網絡強國建設的重要一環,從“網絡營門”走向“網絡國門”是信息時代國內外形勢發展的必然趨勢。
守衛“網絡國門”是網絡空間安全形勢所迫。中國作為第一網絡大國,安全狀況不容樂觀,戰略對手從未停止對我網絡作戰准備。美、英、法等國積極備戰網絡空間,通過網絡空間安全立法賦予軍隊職能,發展網絡戰部隊,研發網絡戰武器裝備,將戰爭推進到了人類的“第五空間”,特別是在中國日益強大崛起的歷史進程中,西方國家在冷戰思維和遏制顛覆戰略的主導下,利用網絡技術手段和傳播方式實施不間斷的騷擾、顛覆和網絡攻擊行動,嚴重影響我國家安全與社會發展,中國逐漸成為網絡安全威脅的重災區、病毒攻擊的試驗場、意識滲透的目的地,國家安全面臨著巨大風險。
未來一段時期內,中國作為新興大國,與各方利益沖突還將加劇,堅定推進網絡國防戰略,加強網絡空間的作戰准備,是積極爭取網絡空間的主導權和話語權的必然途徑,也是中國崛起的必由之路。軍隊作為國家安全穩定的主要力量,必須適應網絡空間特點要求,成為抗擊網絡入侵、網絡顛覆的中堅和主力,維護國家安全和社會穩定。
打贏網絡戰爭是信息時代新軍事變革所趨。網絡技術作為信息時代最先進生產力之一,使得網絡空間作戰成為引導現代戰爭形態演變的主導因素,影響著戰爭全局。近年來,從伊朗“震網”攻擊、俄格沖突網絡戰、烏克蘭電網遭大規模阻癱以及美軍對IS的網絡攻擊,網絡空間在實戰中所展現出的巨大作用逐漸顯現,預示著網絡作戰已成為未來聯合作戰重要樣式。
美軍高度重視網絡空間軍備建設,成立網絡空間司令部,推出網絡空間聯合作戰條令,大幅度擴編網絡戰部隊,極力維護其在網絡空間霸權,把對網絡空間控制能力作為形成“第三次抵消戰略”絕對優勢最重要的競爭內容。
世界多國紛紛跟進,網絡空間軍事化趨勢明顯。嚴峻的網絡空間軍事斗爭形勢要求中國軍隊著眼網絡戰場空間變化,適應信息化戰爭時代要求,實現在網絡空間能打仗、打勝仗的強軍目標。
有效網絡懾戰是加速網絡強國建設內在所需。在中國由網絡大國向網絡強國發展過程中,離不開強大的網絡空間軍事力量作為保障。網絡空間國際競爭表現為國家綜合實力的全面博弈,其中,網絡軍事能力建設的好壞,直接關系到國家安全與穩定,牽一發而動全身,是整個國家安全領域的核心要素。
當前,世界各國在網絡空間的利益互相滲透,出現“你中有我、我中有你,互相合作,共同發展”的局面。但是這種共同發展是不對等的,美國及西方強國利用網絡空間主導權,已經取得了一定的網絡懾戰優勢,使我網絡發展及利益受制於人。軍隊如何在網絡強國建設中完成守土有責的使命重托,前提就是要形成能夠遏制危機、懾控對手的網絡攻防能力,確保和平發展的網絡環境。
因此,軍隊需要確立有效懾戰的威懾戰略目標,形成能與敵“相互摧毀”的戰略制衡能力,從而增強戰略競爭力,懾止網絡空間侵略,保障網絡強國戰略順利推進。
從“守土有責”到“護網衛國”,新形勢要求軍隊承擔新任務
軍隊是保衛國家安全的主力和柱石,網絡空間也不例外。2015年7月1日施行的《國家安全法》規定:“中華人民共和國公民、一切國家機關和武裝力量、各政黨和各人民團體、企業事業組織和其他社會組織,都有維護國家安全的責任和義務。”2016年11月頒布的《網絡安全法》強調了要維護網絡空間主權和國家安全。
在這兩個國家法律的基礎上,2016年12月27日,《國家網絡空間安全戰略》(下文簡稱《戰略》)正式出台,為在新的起點上開創網絡強國新格局提供了總體指導和基本遵循,明確提出了九大戰略任務,進一步體現了軍隊在建設網絡強國進程中的使命任務。
全力護網的國家使命,軍隊要做捍衛網絡空間主權的堅強柱石。《戰略》中列出的九大戰略任務首項就是“堅定捍衛網絡空間主權”,明確提出要“採取包括經濟、行政、科技、法律、外交、軍事等一切措施,堅定不移地維護我國網絡空間主權”。可見,軍隊須承擔起運用實體空間的軍事手段,保衛虛擬網絡空間主權安全和利益的國家使命。
網絡空間主權是國家的核心利益,是國家主權的重要組成,表明國家在網絡空間所擁有的獨立權、平等權、自衛權和管理權。一旦敵對勢力侵犯了我網絡空間主權,就等同於侵犯了我陸海空等實體空間的國家主權,中國將有權利採取包括軍事手段在內的一切措施給予堅決回擊。
在國際上,美國早就提出網絡空間威懾戰略,宣告對美國網絡信息設施的攻擊等同於戰爭行為,美國會採取軍事打擊措施進行報復。軍事手段是維護國家主權的保底手段,在維護國家網絡空間安全中發揮著至關重要的作用。因此,陸海空天軍事力量理所應當地被賦予了保護網絡空間主權的歷史使命,必須憑借強大的實體空間武力保衛網絡空間的國家利益,有力震懾敵對勢力的網絡破壞企圖。
依網衛國的時代擔當,軍隊要做保衛國家安全的壓艙石。《戰略》任務的第二項著力強調要堅決維護國家安全,防范、制止和依法懲治任何利用網絡進行叛國、分裂國家、煽動叛亂、顛覆或者煽動顛覆人民民主專政政權的行為。
信息網絡時代,世界各國軍隊都已經成為網絡空間重要參與者,網絡空間能力水平成為評估一個國家軍隊現代化程度的主要指標,遂行網絡空間使命任務、維護國家安全成為信息化軍隊的主要職責之一。
從中國發展所處的歷史進程來看,要適應全面建成小康社會決勝階段的國家安全戰略需求,必須高度警惕國家在網絡空間被侵略、被顛覆、被分裂的危險,高度警惕由網絡空間引發改革發展大局被破壞的危險,高度警惕中國特色社會主義發展進程被干擾、破壞的危險。
防患於未然,要求國家必須具有應對和處置這些危險的手段措施,具有防范、制止和依法懲治網絡空間違法破壞行為的強大力量。保衛國家歷來是軍隊不可推卸的歷史責任,固有的使命任務決定了中國軍隊必須承擔起在網絡空間採取各種措施,維護國家政治、經濟、文化安全和社會穩定的時代擔當。
攻防兼備的戰略任務,軍隊要做提升網絡空間防護能力的堅強后盾。《戰略》中九大任務的第三項和第八項明確提出,要採取一切必要措施保護關鍵信息基礎設施及其重要數據不受攻擊破壞,要堅持技術和管理並重、保護和震懾並舉;要建設與我國國際地位相稱、與網絡強國相適應的網絡空間防護力量,大力發展網絡安全防御手段,及時發現和抵御網絡入侵,鑄造維護國家網絡安全的堅強后盾。在國家所有維護安全的政治、外交、軍事、科技能力中,軍事力量歷來是所有能力的基礎和支撐,是所有能力的根本保障,是國家安全的最終依托。
因此,軍隊必須承擔起提升國家網絡空間防護能力堅強后盾的戰略任務。現實社會中,軍隊是維護國家安全的定心丸,在網絡空間也同樣應成為人民群眾的安全依賴和保障。軍隊作為國家網絡空間防護能力生成的重要一環,必須做到攻防兼備、懾戰一體,有能力堅決維護國家和人民在網絡空間的利益和安全,能夠有效消除網絡安全威脅造成的各種危機和思想動蕩,使人民能夠切實感受到生產生活得到有效保護,成為全國人民對國家網絡防護能力充滿信心的底氣所在。
聯防聯治的全球責任,軍隊要做維護全球網絡安全的重要支撐。《戰略》任務最后一項明確提出要強化網絡空間國際合作,支持聯合國發揮主導作用,推動制定各方普遍接受的網絡空間國際規則、網絡空間國際反恐公約,健全打擊網絡犯罪司法協助機制,深化在政策法律、技術創新、標准規范、應急響應、關鍵信息基礎設施保護等領域的國際合作。
網絡恐怖主義和網絡犯罪是經過信息網絡發酵催化出的全球威脅新形態,對世界上所有國家的政治、經濟、軍事、文化安全都構成巨大威脅,僅僅依靠政府和民間的力量是不夠的,美國等西方國家紛紛賦予軍隊保護網絡安全的職責和打擊網絡恐怖主義的權限。維護全球網絡空間安全與穩定符合中國以及世界各國的根本利益,軍隊應成為全球網絡空間安全的重要維護者,成為打擊全球網絡恐怖主義和網絡犯罪的重要力量。
網絡的全球化、無界性決定了打擊網絡恐怖主義和跨國網絡犯罪的國際需求,軍隊應在聯合國安理會的框架下,推進國家間網絡治理軍事合作,利用網絡時代的戰略和技術,建立聯防聯治機制,切實維護國家和世界網絡空間安全。
從“沙場練兵”到“網絡備戰”,新領域需要軍隊備戰新舉措
在新的歷史形勢下,網絡空間對軍隊練兵備戰模式提出了全新的要求,應適應網絡空間新特點和軍隊新使命對傳統模式進行創新改革,以強國強軍目標為統攬,加強宏觀統籌,著眼網絡空間軍事行動的法理需求,緊扣網絡空間“軍民一體”的天然屬性,建設“平戰結合”的網絡安全攻防體系,打造“軍地兩用”的網絡國防力量。
立法賦權,為軍隊遂行職能使命提供法理依據。世界各國尤其是西方發達國家在網絡安全立法上高度重視網絡國防問題。美國先后出台了《國家安全第16號總統令》《網絡空間行動戰略》等一系列政策法規,對如何在網絡國防領域保護國家網絡安全進行了不斷的深化規范。
當前,從法律層面厘清網絡空間軍隊的職責任務非常必要,應以《國家安全法》《網絡安全法》為依據,出台網絡國防法和有關網絡空間軍事作戰條令法規,為網絡國防領域建設和軍事行動提供法規支撐和行動綱領,使軍隊在網絡空間的職責和使命更加明確具體。
一是通過網絡國防立法進一步界定網絡主權和網絡邊疆,清晰軍隊的職責范圍。
二是通過網絡作戰法規建設,明確軍隊遂行保衛國家網絡空間安全的行動權限,區分應對網絡入侵、網絡破壞等行為的軍事手段。三是通過網絡空間國際合作政策,明確軍隊協同他國、民間力量等打擊國際網絡恐怖主義、網絡犯罪的職能任務。
軍民融合,為網絡強國建設提供創新動力。軍民融合是世界強國提升網絡空間競爭力的主要做法,對於中國網絡強國建設來說,構建軍民融合網絡安全攻防體系,開發軍地兩用的國防信息基礎設施,是激發軍隊網絡空間作戰能力創新的源泉。
一是統籌國家、軍隊和各級政府等軍民融合職能部門,設置專門的指揮協調機構,調動一切國家網絡力量,建設“軍民一體”“平戰結合”的網絡安全攻防體系。
二是盡快出台網絡安全軍民融合深度發展指導性意見,逐步展開軍民融合基本法律研究論証,指導中長期軍民融合發展。
三是依托國家現有公共移動通信網、光纖通信網及衛星系統,軍民共建覆蓋全國全軍的信息基礎設施,實現軍民統建、分管共享。
四是建立軍民聯合的應急響應機制,加大培訓軍地主管部門控制事態的能力,加強專家和應急專業力量,提升快速恢復受損網絡或信息系統的能力。
軍民聯訓,為網絡空間軍事能力生成提供實戰化環境。網絡空間的軍民共用特性使得軍民聯訓成為世界各國網絡空間軍事演訓的重要方式。美國及北約等國家的網絡空間軍民聯合演習已經形成系列化,“網絡風暴”“網絡衛士”等演練活動吸引了政府、企業、研究機構甚至民間黑客的廣泛參與。我軍網絡空間軍事力量訓練也需要廣泛吸引民間力量參與。
一是搞好軍政合作,建立軍民聯合攻防演練機制,借鑒美國等發達國家網絡戰演練中的紅藍對抗訓練方法,積極建設“國家網絡靶場”,策劃政府、民間機構系列聯合演習,提升軍民一體、官民一體的網絡攻防水平。
二是搞好軍企協作,在互聯網上依靠網信企業設置演練場區,促進軍民之間攻防能力磨合,共同提高防范未知風險能力。
三是組織民間網絡安全公司和黑客人才,開展網絡安全競賽等活動,互相印証,共同提高網絡安全防護技戰術水平。
網絡預備役,為建設強大網軍提供力量源泉。預備役作為國防力量的后備補充,兼有軍事和民用雙重特點,是實現網絡空間經濟發展與國防建設有機統一的有力舉措。
一是以國家安全部門為主導,依據國家利益進行統籌規劃,出台有利於網絡國防預備役建設的系列法規政策,從頂層上解決網絡國防預備役建設中軍民共建的主體分工、推進策略、利益協調等問題。
二是創新預備役組織領導體制和綜合協調機制,有計劃地把預備役建設融入國家網絡信息化發展的各個層面和各個領域。
三是著眼軍隊和地方兩頭管理模式改革,以各省市政府、軍隊和地方企事業單位的管理機制為依托,建立網絡國防預備役人才聯合培養使用機制,完善國家應急動員機制,建立國家網絡防御專用人才數據庫,將網絡民兵和預備役部隊建設納入人民武裝動員的范圍,平時按規定編入民兵應急分隊進行訓練,急時挑選精干人員隨隊參加遂行非戰爭軍事行動任務,戰時按需要成建制征召使用,使國防潛力轉變為國防實力。
Referring URL:
http://military.people.com.cn/BIG5/n1/2017/0417/c1011-29215670.html