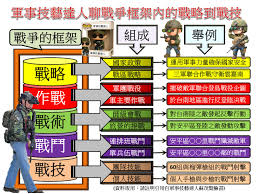
中國軍方:具備群體智慧的無人機有哪些作戰優勢?
現代英語:
A drone is an unmanned aerial vehicle that uses radio remote control equipment or autonomous control devices to control its flight.
Compared with manned aircraft, unmanned aircraft have advantages such as greater flexibility and higher cost-effectiveness in combat.
However, in system-of-systems warfare, due to the complex battlefield environment, dispersed resource allocation, and multi-dimensional combat styles, a single UAV is difficult to perform diverse combat missions.
By leveraging swarm intelligence to conduct intelligent drone swarm operations, the numerical advantage of drones can be transformed into an asymmetric warfare advantage.
Intelligent combat style of drone swarm
In recent years, unmanned aerial vehicle (UAV) swarms have played an increasingly important role in combat missions such as collaborative detection, all-domain strikes, and tactical deception, becoming one of the key development directions in the military field.
Based on the current level of collective intelligence and combat style of drone swarms, they can be divided into three types:
—Pseudo-swarm. This is a type of “swarm” where multiple drones are controlled separately by ground personnel. While the drones appear to be in a swarm, they are actually independent and do not interact or coordinate with each other.
In 2016, the U.S. Navy conducted hundreds of simulation tests of drone swarm attacks against the Aegis defense system. The results showed that when a swarm of eight drones launched a penetration attack, the defense system struggled to allocate firepower effectively, with an average of about 2.8 drones managing to evade the interception system and carry out the attack each time.
In the above cases, the drones appear to be in a “swarm” but lack collective intelligence; their combat capabilities are only enhanced by the numerical advantage brought about by the aggregation of multiple drones.
—Centralized Cluster. This is a clustering approach where a ground command center acts as the cluster’s brain, and drones operate independently, all under the unified command and control of this brain. In November 2020, the U.S. military conducted a two-hour autonomous, coordinated flight test using ground-based software to drive a cluster of Avenger drones. This project utilizes software to determine the optimal combat strategy, improving the flexibility and survivability of existing unmanned combat forces.
Centralized clusters have low levels of intelligence and face potential problems such as single-chain failures and poor reliability. When the communication link between the ground command center and the cluster is damaged, the entire cluster will lose its combat capability due to loss of control.
In 2018, Syrian opposition forces deployed a concentrated swarm of 13 fixed-wing drones to harass and attack a Russian airbase. Russia responded using electronic warfare combined with firepower to intercept the drones, ultimately capturing six and shooting down seven.
—Distributed Cluster. This is a cluster approach where there is no central controller, and drones collaborate and cooperate to execute combat missions through information sharing. This approach has advantages such as decentralization, low complexity, and self-organization, greatly improving the ability to perform complex tasks.
In 2017, the United States used three F/A-18 fighter jets to launch 103 drones, forming a distributed swarm for flight tests. The tests demonstrated functions such as aircraft launch and formation changes, achieving the expected combat results.
Compared to centralized clusters, distributed clusters possess a distributed architecture, and inter-machine information interaction provides the necessary conditions for the emergence of swarm intelligence. Unmanned aerial vehicle (UAV) swarms with swarm intelligence exhibit high autonomy and good security, representing a major development direction for swarm warfare.
Empowering clusters with intelligence by leveraging group behavior characteristics
In the magnificent natural world, there exist biological communities such as schools of fish, herds of mammals, swarms of bees, and flocks of birds. These individual organisms are fragile, but the groups they form through interaction and cooperation possess stronger abilities in foraging, seeking advantage and avoiding harm, and migration.
Biological communities achieve efficient collaboration through simple communication, exhibiting behavioral characteristics such as collaborative aggregation, target attraction, and collision avoidance and repulsion, thus achieving a win-win cluster effect.
This macroscopic intelligent behavior, exhibited by social organisms through cooperation, is known as swarm intelligence. Swarm intelligence is an important research area in artificial intelligence.
By combining unmanned aerial vehicle (UAV) system technology with research on the theory and methods of swarm intelligence, it is hoped that UAV swarms with more autonomous intelligence characteristics can be explored, thus forming advanced swarm intelligence.
—Based on the characteristics of collaborative aggregation behavior, distributed operation of UAV swarms is achieved. In nature, schools of fish foraging for food can gather through local information exchange to improve foraging efficiency. When encountering predators, they can quickly disperse and escape, distracting the predators and reducing the risk of being preyed upon. Similarly, the flight control of UAV swarms, through information exchange between adjacent UAVs, designs a UAV collaborative control protocol, enabling each member in the swarm to reach a “consensus” on global consistency, directional convergence, and desired formation, truly realizing distributed operation of the swarm. Just like the phenomenon of wave motion, information is transmitted rapidly and accurately between them, thereby achieving consistency in action.
—Utilizing target attraction behavior, drone swarms can achieve formation tracking. Just as a wolf pack, led by an alpha wolf, can divide tasks and cooperate closely to hunt prey, with the alpha wolf tracking the target and issuing commands, while the pack members perform different roles and work together efficiently to complete the hunt, drone swarms can follow a similar model. The alpha drone, with its strong detection, identification, and analysis capabilities, is responsible for tracking the target and generating its trajectory. Leveraging its high performance and situational awareness, it achieves real-time target tracking. Follower drones not only track the alpha drone’s trajectory in real time but also form the necessary swarm configuration through inter-drone collaboration, improving payload distribution efficiency and enhancing mission execution.
—Based on collision avoidance and repulsion behavior characteristics, intelligent collision avoidance is achieved for UAV swarms. Intelligent collision avoidance is a fundamental requirement for ensuring the flight safety and successful execution of missions by UAV swarms during combat operations. “Intelligent collision avoidance for swarms” aims to enable individual UAVs to avoid obstacles in the battlefield environment in real time, while preventing collisions between swarm members. To achieve this, an “intelligent repulsive potential field” can be constructed between UAVs and between the swarm and obstacles: when the relative distance is too small, a collision avoidance and repulsion mechanism is triggered, effectively coping with complex environments and combat modes.
Intelligent clusters lead to a new style of system-of-systems warfare
Judging from the development trends of the world’s military powers, with the application of information, unmanned and intelligent technologies on the battlefield, the ability to conduct systematic combat will become an important factor in determining the success or failure of a war.
The development of swarm intelligence technology will greatly promote the transformation of unmanned aerial vehicle (UAV) swarm warfare, and is an important means for future militaries to adapt to complex battlefield environments and enhance their combat capabilities. UAV swarms will revolutionize traditional warfare and become a new type of combat style for winning future battlefields.
Unmanned aerial vehicle (UAV) swarms possessing a certain degree of coordination and autonomy can carry different types of payloads and perform diverse combat missions. Experimental results from UAV swarm collaboration verification projects such as the US’s “Gremlins” and “Partridges” demonstrate that miniaturized, low-cost UAV swarms are expected to achieve collaborative capabilities in detection, perception, identification, communication, and attack in the short term through inter-UAV information sharing.
In light of this, major military powers continue to develop unmanned aerial vehicle (UAV) swarm warfare capabilities, hoping to use systematic, low-cost UAV swarms to harass relatively isolated, high-value military targets and leverage the advantages of asymmetric warfare.
With the continuous upgrading of artificial intelligence technology, drone swarms with collective intelligence can leverage their advantages of strong environmental adaptability, flexible deployment, functional integration, small size and high efficiency to achieve intelligent networking, collaborative combat and strategic confrontation, implement all-round penetration against defense systems, form a “reconnaissance-resistance-strike-assessment” combat closed loop, and defeat the enemy in future multi-domain and multi-dimensional systemic warfare.
現代國語:
無人機蜂群作戰系統示意圖。
無人機是一種利用無線電遙控設備或者自主控制裝置操縱飛行狀態的無人飛行器。
與有人機相比,無人機在作戰中具備靈活性強、作戰效費比高等優勢。
然而,在體系化作戰中,由於戰場環境復雜、要素配置分散、作戰樣式多維,單一無人機難以勝任多樣化作戰任務。
依托群體智能開展智能化無人機集群作戰,可將無人機數量優勢轉化為非對稱作戰優勢。
無人機集群智能化作戰樣式
近年來,無人機集群在協同探測、全域打擊、戰術騙擾等作戰任務中,逐漸發揮出越來越重要的作用,成為軍事領域重點發展方向之一。
按照目前無人機集群的群體智能化程度與作戰樣式,可將其劃分為3種類型:
——偽集群。這是一種由地面人員分別操控多架無人機構成的“集群”方式。無人機看上去是集群,其實相互獨立,並不存在信息交互協同。
2016年,美國海軍進行了數百次無人機“集群”進攻“宙斯盾”防御系統的模擬試驗。結果表明,當由8架無人機組成的“集群”突防攻擊時,防御系統難以合理分配火力,平均每次約有2.8架無人機可避開攔截系統實施打擊。
上述案例,無人機在形式上表現為“集群”,但不存在群體智能,僅靠多架無人機集聚帶來的數量優勢提高作戰能力。
——集中式集群。這是一種以地面指揮中心作為集群大腦、無人機之間無交互、統一受集群大腦指揮調度的集群方式。2020年11月,美軍通過地面軟件驅動“復仇者”無人機組成集群,進行了約2小時的自主協同飛行試驗。該項目利用軟件確定最優作戰方案,提高了現有無人作戰力量的靈活性和生存能力。
集中式集群智能化程度低,面臨單鏈失效、可靠性差等潛在問題。當地面指揮中心與集群通信鏈路遭到破壞時,整個集群將因失去控制而喪失作戰能力。
2018年,敘利亞反對派出動13架固定翼無人機構成集中式集群,對俄羅斯空軍基地進行襲擾攻擊。俄方利用電子戰加火力殺傷的手段實施攔截,最終俘獲6架無人機,擊落7架無人機。
——分布式集群。這是一種不存在中心控制器、各無人機通過機間信息共享、協同配合執行作戰任務的集群方式。該方式具有去中心化、低復雜度和自組織性等優勢,極大提高了遂行復雜任務能力。
2017年,美國利用3架F/A-18戰斗機釋放了103架無人機,形成分布式集群進行飛行試驗,實現了載機發射、隊形變換等功能,達到了預期作戰效果。
相比於集中式集群,分布式集群具備了分布式體系結構,機間信息交互為群體智能的產生提供了必要條件。擁有群體智能的無人機集群,自主性高、安全性好,是集群作戰的主要發展方向。
利用群體行為特征為集群賦智
在瑰麗的自然界中,存在著魚群、獸群、蜂群和鳥群等生物群落。這些生物個體本身是脆弱的,但通過交互協作聚集而成的群體,則擁有更強的覓食、趨利避害和遷徙等能力。
生物群落通過簡單通信實現高效協同,表現出協同聚集、目標吸引和避撞排斥等行為特征,能夠達成合作共贏的集群效果。
這種由群居性生物通過協作表現出的宏觀智能行為特征,即為群體智能。群體智能是人工智能的一個重要研究方向。
結合無人機系統技術,研究群體智能的理論與方法,有望探求到更具自主智能特性的無人機集群,形成高級群體智能。
——根據協同聚集行為特征,實現無人機集群的分布式作業。在自然界中,覓食的魚群能通過局部信息交流聚集,提高覓食效率。在遭遇捕食者時,又可快速散開逃逸,分散捕食者注意力,降低被捕食風險。與之類似,無人機集群的飛行控制,通過相鄰無人機的信息交互,設計無人機協同控制協議,使得集群中的每一成員就全局一致、方向趨同和期望隊形等達成“共識”,真正實現集群的分布式作業。就像波動現象一樣,相互間迅速准確地傳導信息,從而達成行動的一致性。
——利用目標吸引行為特征,實現無人機集群的編隊跟蹤。狼群能在頭狼帶領下進行任務分工,密切配合圍捕獵物。頭狼負責追蹤目標並發布命令,狼群則擔負不同職責共同協作高效完成捕獵任務。無人機集群可參照狼群模式,利用目標吸引行為特征,形成領航跟隨任務模式。領航機探測識別與分析處理能力較強,負責跟蹤目標生成航跡,發揮高性能優勢和態勢感知能力,實現對目標的實時跟蹤,跟隨機既能實時跟蹤領航機航跡,又能通過機間協同形成任務所需的集群構型,提高載荷分布配置效能,強化任務執行力。
——依據避撞排斥行為特征,實現無人機集群的智能防撞。無人機集群在執行作戰任務時,實現智能防撞是保證自身飛行安全和順利執行任務的基本要求。“集群智能防撞”,就是要讓各無人機實時規避戰場環境中的障礙物,同時集群間不發生碰撞。要實現這一效果,可構建無人機之間和集群與障礙物之間的“智能斥力勢場”:當相對距離過小時,觸發避撞排斥機制,有效應對復雜環境和作戰模式。
智能集群引領體系化作戰新樣式
從世界軍事強國發展趨勢來看,隨著信息化、無人化和智能化技術應用於戰場,是否具備體系化作戰能力將成為決定戰爭成敗的重要因素。
群體智能技術的發展,將極大推動無人機集群作戰模式的變革,是未來軍隊適應復雜戰場環境、提升作戰能力的重要手段。無人機集群將顛覆傳統戰爭形態,成為制勝未來戰場的新型作戰樣式。
具備一定協同能力與自主性的無人機集群,可搭載不同種類載荷,執行多樣化作戰任務。從美國的“小精靈”“山鶉”等無人機集群協同作戰驗證項目的實驗效果來看,小型化、低成本的無人機集群,在短期內有望通過機間信息共享,形成探測、感知、識別、通信和攻擊等協同能力。
鑑於此,各軍事強國持續發展無人機集群作戰力量,期望以成體系的低成本無人機集群,襲擾相對孤立的高價值軍事目標,發揮出非對稱作戰優勢。
隨著人工智能技術的不斷升級,擁有群體智能的無人機集群,可發揮其環境適應能力強、部署靈活、功能集成、小型高效的優勢,實現智能組網、協同作戰與博弈對抗,對防御系統實施全向突防,形成“偵-抗-打-評”作戰閉環,在未來多域多維的體系化作戰中克敵制勝。