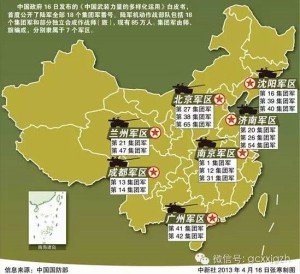
打贏信息化條件下局部戰爭是軍隊核心任務
來源:解放軍報
In order to win local wars under conditions of informatization, vigorously strengthen military struggle preparation, is a successful experience and important way to guide army building, our army is a major strategic task. Supremely important strategic task. People’s Army Central Military Commission established in accordance with the decisions and arrangements, preparations for military struggle toward a new journey stride forward.
Walking preparations for military struggle rational development road
New China came nearly 60-year history. For decades, the country was much larger rivals, dangerous, but always to stand up, continue to grow and live. There are a lot of successful experience, a very important one is to rely on comprehensive solid preparations for military struggle. It can be said, precisely because of the people’s army “ready”, was created a homeland security steel wall, the guardian of the people’s happiness and peace, prosperity and security of the economic and social development. Recalling decades stormy journey preparations for military struggle, glory Aureole achievements, we should also clearly see that not enough scientific areas. For example, many units ready for Military Struggle, the guiding ideology too much emphasis on specific threats, over-reliance on “the situation stimulus” caused suddenly strong suddenly weak level of combat readiness and combat effectiveness of the construction fluctuated, military preparations did not struggle to maintain autonomy and healthy sustainable development.
Different things when it moves, it is something different equipment variants. Currently, preparations for military struggle and stands at a new historical starting point. National security situation is undergoing complex and profound changes, on the one hand, traditional security threats and non-traditional security threats we face are increasing, the world’s major powers in my peripheral geostrategic competition intensified, neighboring countries, political turbulence, regional security environment, there are many hidden dangers domestic ethnic separatist forces and their activities is rampant, affecting national security instability, increasing uncertainty, preparations for military struggle facing unprecedented challenges; on the other hand, the international unilateralism setback, the financial crisis delayed the expansion of global hegemony, Taiwan situation has eased, I eased pressure on the main strategic directions, preparations for military struggle facing unprecedented opportunities.This opportunity is not only strategic, but also historic. How to seize the opportunity to make good use of the opportunity and momentum forward, the current preparations for military struggle to answer practical proposition. After 30 years of reform and development, army building a qualitative leap, the synthesis of troops, higher level of information, science and technology-intensive, quality and efficiency features more obvious preparations for military struggle with Keziliyong rich results and advancing the jump basic conditions. Into the new century, Hu focused on the special requirements of the party of national defense and army building, giving the army the “three offers, a play,” the historical mission, stressing that “in order to enhance our military must win local wars under information age conditions core, and constantly improve the ability to respond to multiple security threats and accomplish diverse military tasks. ” This series of major strategic thinking, adjust the point of preparations for military struggle to expand the mandate of the contents of preparations for military struggle.Scientific concept of development of this important guidelines established for military combat preparations put a higher demand good seek fast, according to a comprehensive, coordinated and sustainable development and people-oriented standards, there are many ideas need liberation, a lot of work need to innovate, many aspects need to be improved.
Advance preparations for military struggle in the new situation, because of the situation must change, because of the situation set policy, based on a new starting point, to seek new development. Should be based on the threat of grasping ready to strengthen all-round “threat awareness” and “enemy concept,” war is not far away and do not fully understand the only one of the grim reality, unswervingly push forward preparations for military struggle. Should be prepared based on the task grasp the fundamental task of the military is to fight and ready to fight, the battle can not fight a hundred years, but not a moment to relax ready, you must follow the standard effective functioning of the mission, to promote a comprehensive and systematic preparations for military struggle. Should be based on the ability to catch ready, out of the enemy carried away by emergency preparedness passive mode, active design of future wars, there are plans to increase planned to respond to multiple security threats and accomplish diverse military tasks ability, steadily push forward the scientific military preparations struggle.
In major breakthroughs improve the quality of preparations for military struggle
Unfocused no strategy, no emphasis on difficult to break. Make full use of important strategic opportunities, to seize the key content to seek a breakthrough, not only to follow the objective requirements of preparations for military struggle inherent laws, it is an urgent need to comprehensively improve the combat capability of the armed forces.
Practice basic military training as a peacetime army, and combat effectiveness is the basic way of development, is the most direct and most effective preparations for military struggle.We must further enhance awareness of the importance of military training, military training to effectively attach strategic position, really big catch in the army military training, training vigorously promote the formation of a new upsurge in transition. Joint training should seize the key to the combat effectiveness, strengthen joint awareness, improve the quality of the joint, improve joint training and regulations, improve the mechanism of joint training, promoting joint military training from form to substance. Should be training in complex electromagnetic environments as an important entry point and the starting point, and actively explore the organization and command training, research and technological measures for an effective way to combat training and weapons training, operational use, accelerating military training under conditions of mechanization to military training in conditions of informationization change. Training mission should be subject to the carrier, active configuration set up similar to actual battlefield environment, explore the combat training, field based training and base training, simulated training and network training as the main way to really, hard, in fact, test standards to test than pulling mechanism for the implementation of the path of combat training, enhance training effectiveness. Should actively carry out non-war military operations training to improve forces to carry out non-war military operations expertise, empowerment troops accomplish diverse military tasks.
People are fighting the various elements of the most active and most active element, talent preparations for military struggle preparation is the most important and the most difficult to prepare. Outcome of a war depends on the battlefield, but the link was to decide the outcome in the usual competition, in which the focus is talent. Currently, the key is to highlight the joint operations command personnel and high-level professional and technical personnel two “strategic starting point”, traction and promote the overall development of qualified personnel capacity building. Protruding joint operations command personnel training, establish and improve strategic and operational focus on training to improve pattern-level commanders around the joint operations to improve personnel training system, the reform of teaching contents and methods of joint operations, commanding officers to increase job rotation and cross-training, step up joint operational command emergency personnel training, strengthen and improve measures. Outstanding high-level professional and technical personnel training. Follow focus, both in general, to seize the lead, lead the overall principle, focus on training across disciplines planning to organize major research projects of leading scientists, to promote discipline capable of directing talents academic technology innovation and development, equipment and technology to solve complex security technical expert personnel problems, and provide a strong intellectual support information technology.
Soldiers rapidly guiding the iron law of war, under conditions of informationization more emphasis on “speed advantage.” Rapid response capacity has become an important indicator to measure the army’s combat readiness and combat capabilities. Should sound an agile and efficient emergency command mechanism. In recent years, the basis of summing up our military to accomplish diverse military tasks practical experience, grasp curing and conversion-related outcomes, the establishment of emergency response mechanisms and improve the regulatory system, improve the mechanism set up to develop response plans, organize relevant study and training, to ensure that if something happens quick response, efficient command, correct action. Should establish advanced and reliable command information system. In accordance with good interoperability, responsive, security and information sharing requirements established in the end longitudinal, transverse to the edge of the information networks and integrated one, simple hierarchy of command system, relying on information technology to improve emergency response command and rapid response capability. Grasp the strategic delivery of capacity-building characteristics and laws, focusing on the development of strategic transport aircraft (ship), military helicopters and new aircraft, and consider traffic battlefield, explore the establishment of smooth and efficient command and management mechanism, the overall advancement of the strategic transportation capacity building.
Security is a combat. Modern warfare combat operations at any one time, against all the system, comprehensive security have become increasingly demanding. Promoting military struggle preparation, must comprehensively improve the combat support, logistics and equipment support and other comprehensive support capabilities. Our military has historically focused on promoting the coordination of combat forces and combat support forces, reconnaissance, early warning, command and communications, mapping navigation, meteorology and hydrology, engineering, chemical defense and other support to improve the ability to achieve overall synchronization. However, with the continuous expansion and development of the situation changes in battlefield space combat support capability system began to appear new “short board” must be filled as soon as possible to form the overall advantages of joint operations full-dimensional battlefield. Logistics focus is to improve the level of modernization. In accordance with the requirements of the development, the steady implementation of the logistics reform, to promote the integration of the security system to protect the way to the community development, support means to move information, logistics management to scientific change, and promote sound and rapid development of the logistics building. Focusing on strengthening security equipment supporting construction. Improve the capability of independent innovation, accelerate the construction and development of new weapons and equipment, and constantly optimize the structure of armament systems.Focusing on supporting systems and equipment, and security systems supporting supporting construction, improve the equipment series, universal, standardized level, and gradually promote the formation of the organized system equipped to combat and support capabilities, accelerate the establishment of military and civilian production, integrating the armed forces weapons and equipment research and production system and maintenance support system, and further improve the integration of military and civilian equipment development path.
Adhere to scientific development and innovation of military struggle preparation path
Advance preparations for military struggle in the new starting point, we must adhere to the scientific concept of development as guidance, the practical application of the requirements of the times thinking, to explore the development path of innovation and preparations for military struggle.
Continue to emancipate the mind, reform of the army in the tide of the overall advancement of military preparations struggle. The more in-depth preparations for military struggle, the more touches concept of development, institutional mechanisms, policies and systems and other aspects of deep-seated contradictions and problems, and promote the greater the difficulty. The fundamental way to solve these problems, is to continue to emancipate the mind, deepen reform of national defense and army building. Strategic objectives of military reform is building computerized armed forces and winning the information war, which point preparations for military struggle is the same. Preparations for military struggle is the leading military reform and traction, military reform is an important part of preparations for military struggle and optimized conditions, both unity of purpose, mutually reinforcing. Thus, under the new situation to promote the preparations for military struggle, must be combined with promoting defense and military reform, to improve the combat effectiveness as a starting point and goal of reform, with the standards and unify thought reform measure reform measures, testing the effectiveness of reform, promote reform in preparations for military struggle.
Strengthen scientific co-ordination, in the process of modernization of the armed forces to coordinate the promotion preparations for military struggle. Military modernization is a big system, military struggle preparation is the key indeed affect the whole body. Well prepared for military struggle, will be able to provide clear and specific requirements for the overall development of our military modernization construction, provide real starting point, forming a huge traction force. Must stand on military modernization development overall perspective, the effective co-ordination with the main good times, far and near, and built with an equal relationship, the process of preparations for military struggle becomes strengthen military modernization process, the process of military modernization into service the process of preparations for military struggle, so that the two complement each other to promote the coordinated development.
Leading Position of Information, in the mode of generating combat transition to push ahead with preparations for military struggle. Currently, information technology is profoundly changing the mode of generating combat, is also changing all aspects of army building. Promoting military struggle preparation, must quickly adapt to this new situation, take the initiative out of the mindset of mechanization to strengthen the concept of information-led, focusing on scientific and technological progress to improve combat effectiveness, explore innovative adaptation of information requirements of the military concept of war, military technology, military organization and military management, focus on improving the training of military personnel, weapons and equipment development, the level of information the best combination of people and weapons, accelerate the transformation of military training, and gradually establish an effective mechanism to combat the new generation and improve and promote preparations for military struggle to achieve a qualitative leap.
Prominent real traction in accomplishing diversified military tasks to accelerate preparations for military struggle. Practice tells us that no matter how the evolution of the international situation, how to expand the Functions of the Army, how onerous diverse military tasks, containment and win wars, preservation of peace is always the most important functions of the army and winning conditions under local war always is the core mission of our military. Only with the core military capabilities and accomplish diverse military tasks have a solid foundation. We must always take to improve the core military capabilities in the first place, aimed at promoting the fundamental function fully prepared, ready to do more hands without “one-track mind,” not ready to classify “one size fits all”, without further preparation, “superficial”, trying to force the ability to adapt to various conditions, to cope with various situations and accomplish diverse military tasks.
Original Mandarin Chinese:
以打贏信息化條件下局部戰爭為重點,大力加強軍事鬥爭準備,是軍隊建設的一條成功經驗和重要指導方式,是我軍一項重大的戰略任務。戰略任務重千鈞。人民軍隊按照中央軍委既定的決策部署,向著軍事鬥爭準備新徵程闊步邁進。
走軍事鬥爭準備理性化發展之路
新中國走過近60年歷程。幾十年來,國家一度強敵環伺、危機四伏,卻始終屹立不屈,不斷生息壯大。成功的經驗有很多,很重要的一條就是靠全面扎實的軍事鬥爭準備。可以説,正是有了人民軍隊“時刻準備著”,才鑄就了祖國安全的鋼鐵長城,守護了人民群眾的幸福安寧,保障了經濟社會的繁榮發展。回顧幾十年軍事鬥爭準備的風雨徵程,在成績的榮耀光環背後,我們也要清醒看到不夠科學的地方。比如不少單位抓軍事鬥爭準備,在指導思想上過于強調具體威脅,過度依賴“情況刺激”,造成戰備水平忽強忽弱,戰鬥力建設忽高忽低,軍事鬥爭準備沒有保持自主、健康地持續發展。
時異則事移,事異則備變。當前,軍事鬥爭準備又站在了一個嶄新的歷史起點上。國家安全形勢發生復雜深刻變化,一方面,我們面臨的傳統安全威脅和非傳統安全威脅都在增加,世界主要大國在我周邊地緣戰略競爭不斷加劇,周邊國家政局持續動蕩,地區安全環境存在諸多隱患,國內民族分裂勢力及其活動猖獗,影響國家安全的不穩定、不確定因素增多,軍事鬥爭準備面臨前所未有的挑戰;另一方面,國際上單邊主義受挫,金融危機拖延了全球霸權擴張,臺海形勢明顯緩和,我主要戰略方向壓力有所減輕,軍事鬥爭準備面臨前所未有的機遇。這個機遇既是戰略性的,也是歷史性的。怎樣抓住機遇、用好機遇、乘勢推進,是當前軍事鬥爭準備需要回答的現實命題。經過30年改革發展,我軍建設出現質的跨越,部隊合成化、信息化程度更高,科技密集型、質量效能型特徵更加明顯,軍事鬥爭準備有了可資利用的豐富成果和推進躍升的基礎條件。進入新世紀新階段,胡主席著眼黨對國防和軍隊建設的特殊要求,賦予軍隊“三個提供、一個發揮”的歷史使命,強調“我軍必須以增強打贏信息化條件下局部戰爭能力為核心,不斷提高應對多種安全威脅、完成多樣化軍事任務的能力”。這一係列重大戰略思想,調整了軍事鬥爭準備的基點,拓展了軍事鬥爭準備的任務內容。科學發展觀這一重要指導方針的確立,對軍事鬥爭準備提出了好中求快的更高要求,按照全面、協調、可持續發展和以人為本的標準來衡量,還有很多思想需要解放,很多工作需要創新,很多方面需要提高。
新形勢下推進軍事鬥爭準備,必須因勢求變、因情定策,立足新的起點,謀求新的發展。應基于威脅抓準備,強化全方位的“威脅意識”和“敵情觀念”,充分認清戰爭並不遙遠且不只一種的嚴峻現實,堅定不移地推進軍事鬥爭準備。應基于任務抓準備,軍隊的根本任務是打仗和準備打仗,仗可以百年不打,但準備一刻也不能放松,必須按照有效履行職能使命的標準,全面係統地推進軍事鬥爭準備。應基于能力抓準備,跳出被敵情牽著走的被動應急準備模式,主動設計未來戰爭,有規劃有計劃地提高應對多種安全威脅、完成多樣化軍事任務能力,穩步科學地推進軍事鬥爭準備。
以重點突破提高軍事鬥爭準備質量
沒有重點就沒有戰略,沒有重點就難以突破。充分利用重要戰略機遇期,抓住重點內容謀求突破,既是遵循軍事鬥爭準備內在規律的客觀要求,更是全面提高部隊實戰能力的迫切需要。
軍事訓練作為和平時期軍隊最基本的實踐活動,是戰鬥力生成和發展的基本途徑,是最直接、最有效的軍事鬥爭準備。必須進一步提高對軍事訓練重要性的認識,切實把軍事訓練擺到戰略位置,真正在部隊形成大抓軍事訓練、大力推進訓練轉變的新高潮。應抓住聯合訓練這個戰鬥力生成的關鍵環節,強化聯合意識,提高聯合素質,健全聯訓法規,完善聯訓機制,推動軍事訓練從形式到實質的聯合。應以復雜電磁環境下訓練為重要切入點和抓手,積極探索組織指揮訓練、戰技術對策研練和武器裝備操作使用訓練的有效辦法,加速推進機械化條件下軍事訓練向信息化條件下軍事訓練轉變。應以使命課題訓練為載體,積極構設近似實戰的戰場環境,探索以對抗訓練、野戰化訓練和基地化訓練、模擬化訓練、網絡化訓練等為主要方式,以真、難、實為檢驗標準,以考、比、拉為落實機制的實戰化訓練路子,增強訓練實效。應積極開展非戰爭軍事行動訓練,提高部隊遂行非戰爭軍事行動專業技能,增強部隊完成多樣化軍事任務的能力。
人是戰鬥力諸要素中最積極、最活躍的要素,人才準備是軍事鬥爭準備中最重要、最艱巨的準備。戰爭勝負決于戰場,但決定勝負的環節卻在平時的競爭之中,其中的重點就是人才。當前,關鍵是要突出聯合作戰指揮人才和高層次專業技術人才兩個“戰略抓手”,牽引和推動人才隊伍能力建設的整體發展。突出聯合作戰指揮人才培養,重點建立健全戰略戰役層次指揮員培養提高模式,圍繞完善聯合作戰人才培訓體係、改革聯合作戰教學內容和方法、加大指揮軍官崗位輪換和交叉培訓力度、加緊聯合作戰指揮人才應急培訓等,加強和完善有關措施。突出高層次專業技術人才培養。按照突出重點、兼顧一般、抓住龍頭、帶動整體的原則,重點培養能夠跨學科領域謀劃組織重大項目攻關的科技領軍人才、能夠指導推進學術技術創新發展的學科拔尖人才、能夠解決裝備技術保障復雜難題的技術專家人才,為信息化建設提供強有力的智力支撐。
兵貴神速是戰爭指導的鐵律,信息化條件下更強調“速度優勢”。快速反應能力已成為衡量一支軍隊戰備水平和實戰能力的重要標志。應健全靈敏高效的應急指揮機制。在總結梳理近年我軍完成多樣化軍事任務實踐經驗的基礎上,抓好相關成果的固化和轉化,建立應急機制,健全法規制度,完善機構設置,制定應對預案,組織相關研練,確保一旦有事能快速反應、高效指揮、正確行動。應建立先進可靠的指揮信息係統。按照互操作性好、反應靈敏、安全保密和信息共享的要求,建立縱向到底、橫向到邊的信息網絡和綜合一體、層級簡捷的指揮係統,依靠信息技術提高應急指揮與快速反應能力。把握戰略投送能力建設的特點規律,重點發展戰略運輸機(艦)、軍用直升機和新型航行器,統籌考慮交通戰場建設,探索建立順暢高效的指揮管理機制,整體推進戰略輸送能力建設。
保障也是戰鬥力。現代戰爭中的任何一次作戰行動,都是體係的對抗,對綜合保障的要求越來越高。推進軍事鬥爭準備,必須全面提高作戰保障、後勤保障和裝備保障等綜合保障能力。我軍歷來注重協調推進作戰力量與作戰保障力量建設,偵察預警、指揮通信、測繪導航、氣象水文、工程防化等保障能力總體實現了同步提高。但隨著形勢的發展變化和戰場空間的不斷拓展,作戰保障能力體係開始出現新的“短板”,必須盡快補齊,以形成全維戰場的聯合作戰整體優勢。後勤保障重點是提高現代化水平。按照時代發展要求,穩步實施後勤改革,將保障體制向一體化推進、保障方式向社會化拓展、保障手段向信息化邁進、後勤管理向科學化轉變,推動後勤建設又好又快發展。裝備保障重點是加強配套建設。提高自主創新能力,加快新型武器裝備建設發展,不斷優化我軍武器裝備結構體係。注重裝備的體係配套、係統配套和保障配套建設,提高裝備係列化、通用化、標準化水平,逐步推進裝備成係統成建制形成作戰能力和保障能力,加快建立軍民結合、寓軍于民的武器裝備科研生産體係和維修保障體係,進一步完善軍民融合發展裝備的路子。
堅持科學發展創新軍事鬥爭準備路徑
在新的起點上推進軍事鬥爭準備,必須堅持以科學發展觀為指導,切實運用符合時代要求的思維方式,探索創新軍事鬥爭準備的發展路徑。
繼續解放思想,在軍隊改革大潮中整體推進軍事鬥爭準備。軍事鬥爭準備越深入,觸及發展理念、體制機制、政策制度等方面的深層次矛盾和問題就越多,推進的難度也越大。解決這些問題的根本出路,在于繼續解放思想、深化國防和軍隊建設改革。軍隊改革的戰略目標是建設信息化軍隊、打贏信息化戰爭,這與軍事鬥爭準備的基點是一致的。軍事鬥爭準備是軍隊改革的龍頭和牽引,軍隊改革則是軍事鬥爭準備的重要內容和優化條件,二者目標一致、互為促進。因此,新形勢下推進軍事鬥爭準備,必須與推進國防和軍隊改革結合起來,把提高戰鬥力作為改革的出發點和落腳點,用戰鬥力標準統一改革思想,衡量改革措施,檢驗改革成效,在改革中推進軍事鬥爭準備。
加強科學統籌,在軍隊現代化建設進程中協調推進軍事鬥爭準備。軍隊現代化建設是個大係統,軍事鬥爭準備則是牽一發而動全身的關鍵。軍事鬥爭準備做好了,就能為我軍現代化建設整體發展提供明確具體的需求,提供實實在在的抓手,形成巨大的牽引力量。必須站在軍隊現代化建設發展全局的高度,切實統籌好主與次、遠與近、建與用等關係,把軍事鬥爭準備的過程變成加強軍隊現代化建設的過程,把軍隊現代化建設的過程變成服務軍事鬥爭準備的過程,使二者互為促進,協調發展。
堅持信息主導,在戰鬥力生成模式轉變中創新推進軍事鬥爭準備。當前,信息技術正在深刻改變著戰鬥力生成模式,也在改變著軍隊建設的方方面面。推進軍事鬥爭準備,必須敏銳地適應這個新形勢,主動跳出機械化思維定勢,強化信息主導觀念,注重依靠科技進步提高戰鬥力,探索創新適應信息化戰爭要求的軍事理念、軍事技術、軍事組織和軍事管理,著力提高軍事人才培養、武器裝備發展、人與武器最佳結合的信息化水平,加快推進軍事訓練轉變,逐步確立新型戰鬥力生成與提高的有效機制,推動軍事鬥爭準備實現質的躍升。
突出實戰牽引,在完成多樣化軍事任務中加速推進軍事鬥爭準備。實踐告訴我們,無論國際局勢如何演變、軍隊的職能使命如何拓展、多樣化軍事任務多麼繁重,遏制戰爭、打贏戰爭、維護和平始終是我軍職能的重中之重,打贏信息化條件下局部戰爭永遠是我軍的核心任務。只有具備了核心軍事能力,完成多樣化軍事任務才有堅實基礎。必須始終把提高核心軍事能力放在首要位置,瞄準根本職能推進全面準備,做到多手準備而不“單打一”,分類準備而不“一刀切”,深入準備而不“表面化”,努力使部隊具備適應各種條件、應對各種情況、完成多樣化軍事任務的能力。
Source: PLA Daily
Originally Published 2009年01月08日